Enable API Discovery on BIG-IP Virtual Server
Objective
This document provides instructions on how to discover and monitor APIs on a BIG-IP Virtual Server.
Prerequisites
-
A valid F5 Distributed Cloud Services Account. If you do not have an account, see Getting Started with Console.
-
A Secure Mesh Site deployed with reachability to the BIG-IP instances. For more information, see Infrastructure Requirements for more details.
Configuration
Step 1: Log into Console and navigate to API Discovery.
-
Log into Console.
-
Click Web App & API Protection.
Figure: Console Homepage
-
Select Manage > BIG-IP Virtual Servers.
-
In the API Discovery column of the BIG-IP Virtual Server, click Enable to open the API Discovery configuration page.
Alternatively, click ... for your BIG-IP Virtual Server, and then select Manage Configuration to open the API Discovery configuration page.
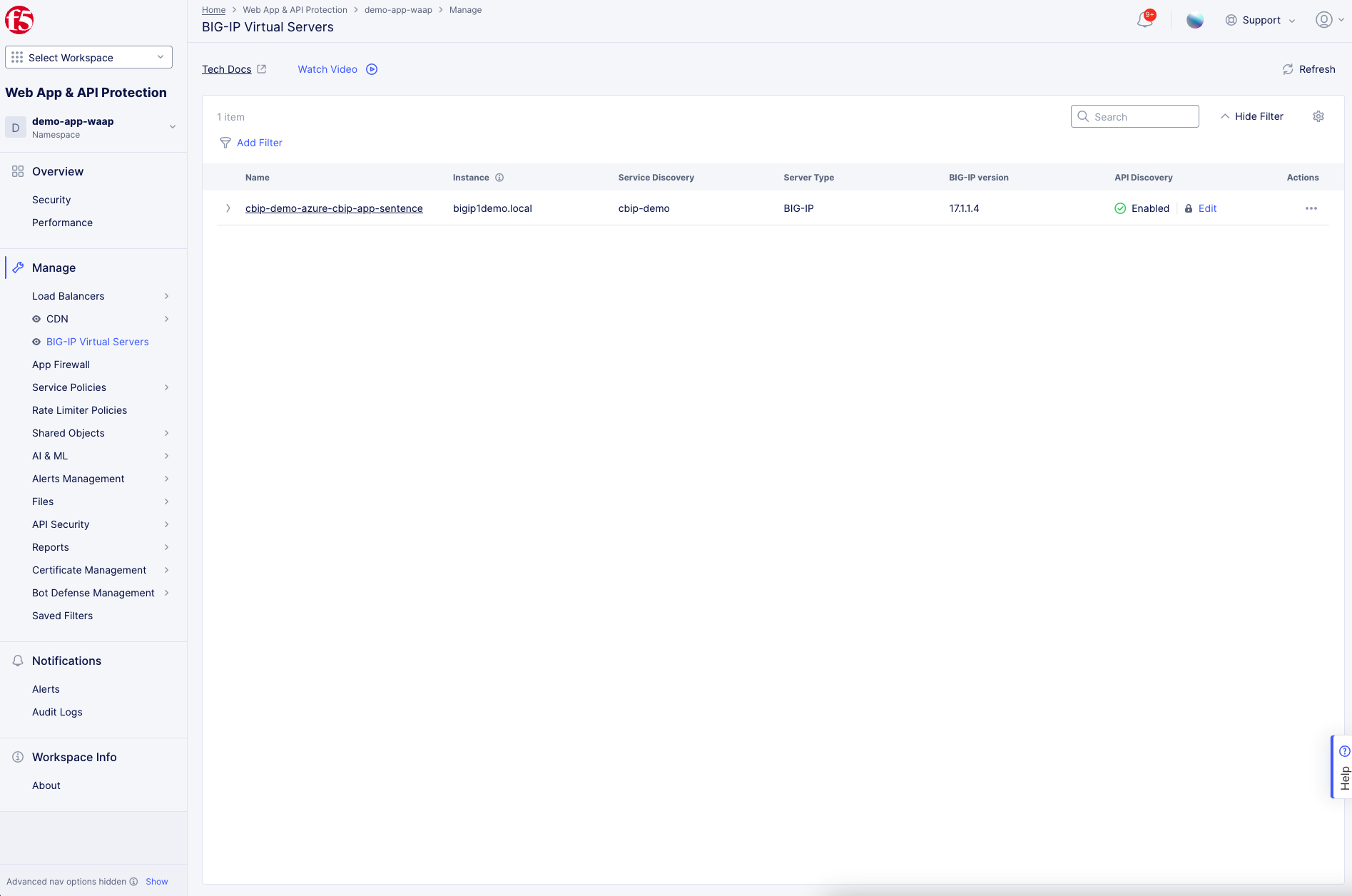
Figure: WAAP - BIG-IP Virtual Servers
Step 2: Configure API Discovery.
- In the API Definition section, provide an OpenAPI Specification file. This is an optional step.
Note: An API Definition groups multiple OpenAPI Specifications into an inventory of APIs. This allows users to manage APIs by removing or moving discovered/shadow APIs into the inventory. For more details, see Import OpenAPI Specification files and create API Definitions.
-
In the API Discovery drop-down menu, select Enable. You can configure the following fields in the API Discovery section:
- Optionally, in the Learn from Traffic with Redirect Response field, select a redirect response learning option.
- Optionally, in the Purge Duration for Inactive Discovered APIs from Traffic field, enter the number of days to purge inactive discovered APIs.
- Optionally, in the Settings field, select the API Discovery Setting Object to define a customer configuration for the API Discovery process.
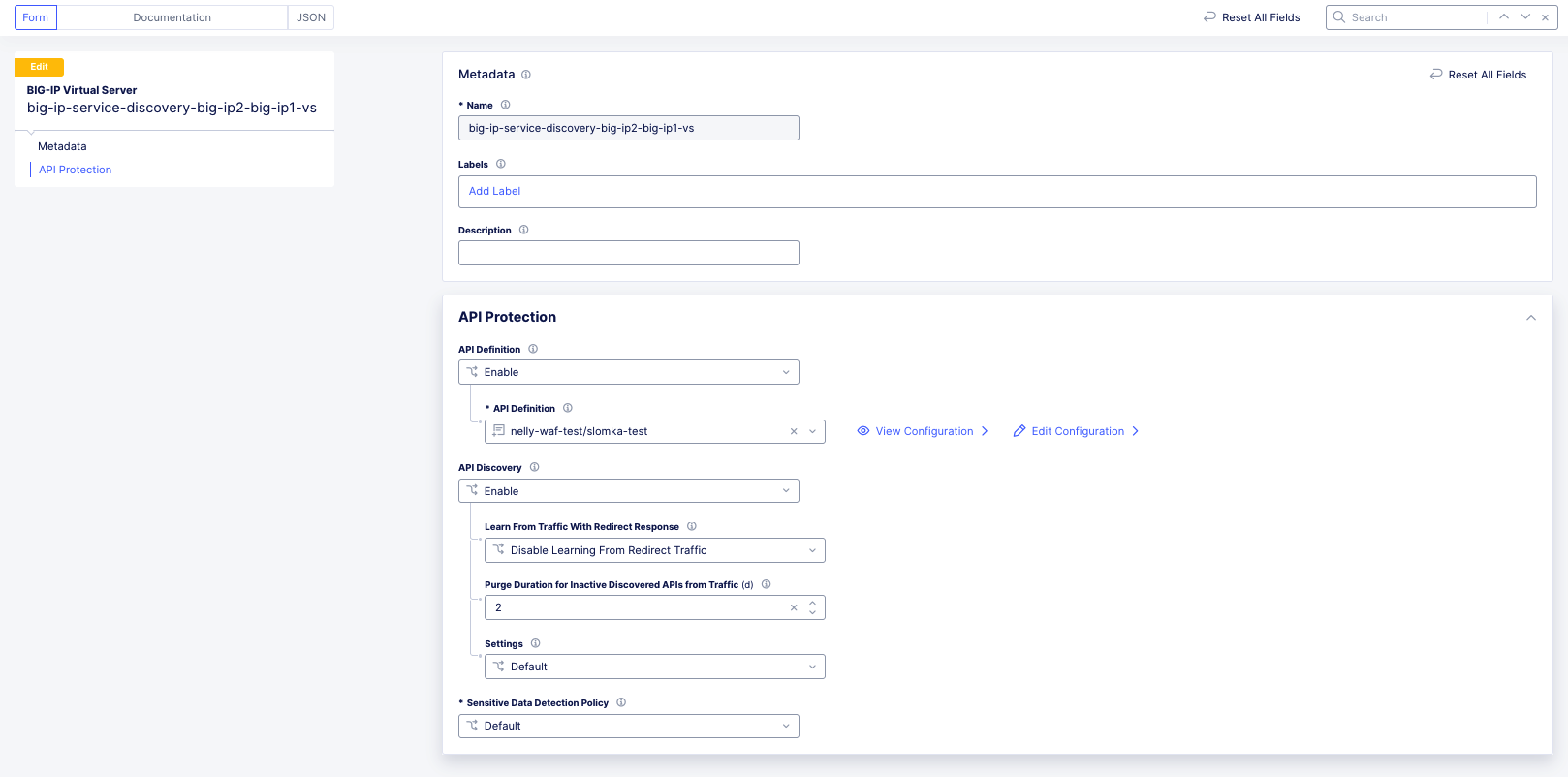
Figure: WAAP - Manage BIG-IP Virtual Servers
Step 3: Optionally, Configure Sensitive Data Detection Policy.
-
Create a new sensitive data policy with a compliance framework.
-
Create a custom sensitive data type.
-
Configure the sensitive data policy in the Distributed Cloud Virtual Server.
-
View the compliance framework in an API inventory with endpoints governed by a compliance framework.
For information on configuring a sensitive data detection policy, see Discover Sensitive Data and Compliance
Monitor API Endpoints
Follow these steps to monitor the API Endpoints configured for your BIG-IP Virtual Servers:
-
From the BIG-IP Virtual Servers in your namespace, click a Virtual Server name to display all endpoints for that Virtual Server.
-
From the Security Dashboard in your namespace, click a Virtual Server name in the Application Delivery table widget to display all the endpoints for that Virtual Server.
For more details, see API Endpoint Discovery and Schema Learning
Handle Blocked Requests in API Discovery for BIG-IP versions v15.1.x and Earlier
For BIG-IP version v15.1.x and earlier systems that have ASM provisioned, API Discovery requires a dedicated version of the iRule that supports detection of requests that are blocked by the applied security policy.
This iRule version ensures that only traffic permitted by the ASM is used for API Discovery, preventing blocked or malicious requests from being included in the discovered API inventory.
To enable API Discovery for blocked requests, you must add the ASM_REQUEST_DONE section in the API Discovery iRule of the BIG-IP Virtual Server.
Follow these steps to enable API Discovery for blocked requests:
-
Ensure that the ASM is provisioned and attached to the Virtual Server used for API Discovery.
-
Ensure that you enable the Trigger ASM iRule Events Mode for the ASM policy.
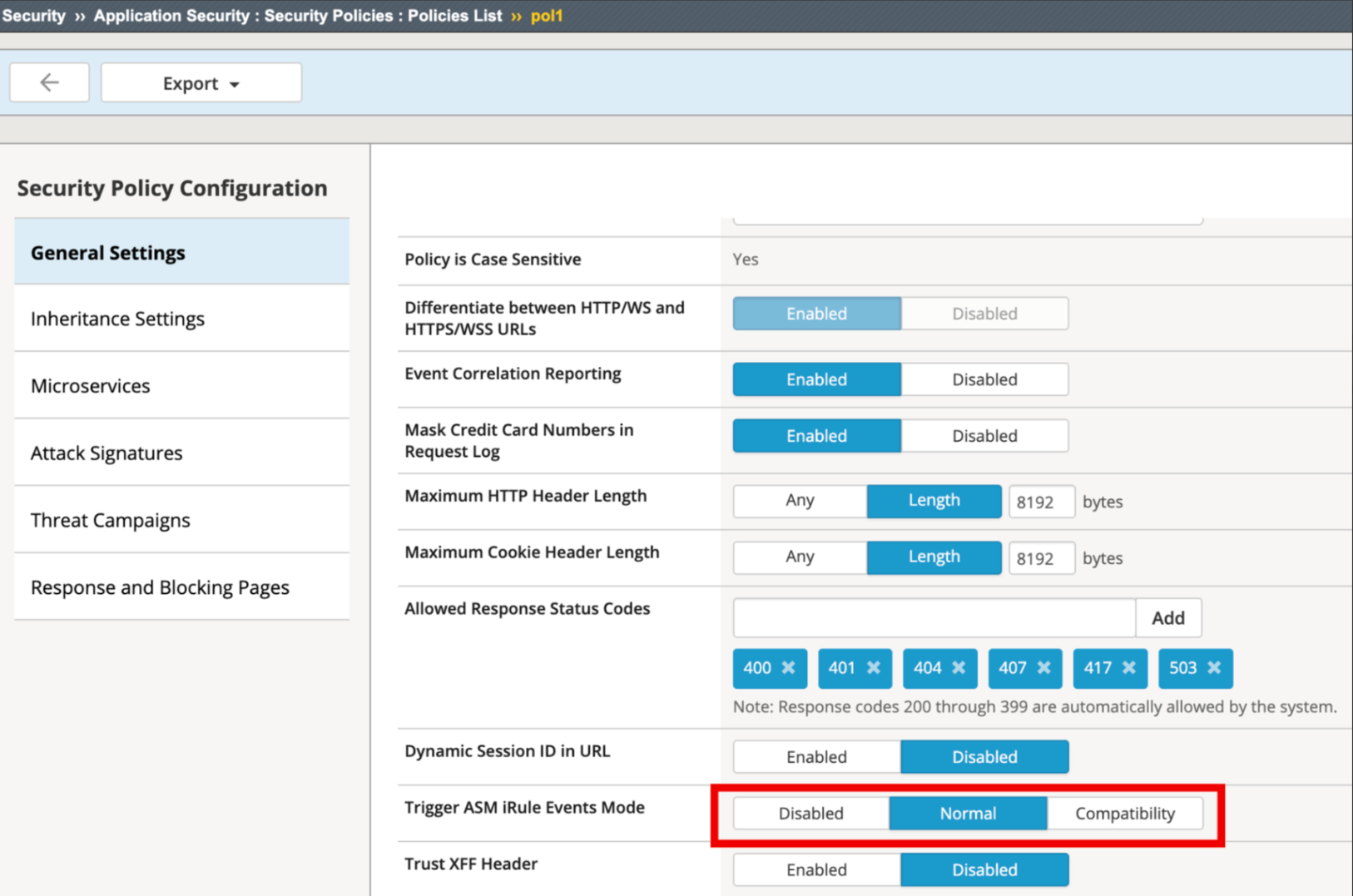
Figure: BIG-IP - Trigger ASM iRule Events Mode
- Add the ASM_REQUEST_DONE section to the APID iRule of the APID-enabled Virtual Server.
when ASM_REQUEST_DONE {
if {[ASM::violation count] > 0} {
#log local0. "Request has ASM violations"
set request_has_violations 1
}
}
Append the following code snippet in HTTP_RESPONSE_RELEASE event(as part of headers collection).
if {$request_has_violations} {
append resJsonArrayStr "\"X-Content-Type-Options\": \"nosniff\","
append resJsonArrayStr "\"X-Frame-Options\": \"SAMEORIGIN\","
append resJsonArrayStr "\"X-XSS-Protection\": \"1; mode=block\""
}
Note: This configuration is not required for BIG-IP versions v16.1.x, and later.