Test Your Bot Defense Standard Configuration
Use the following information to help ensure that Bot Defense Standard is properly configured, that it is injecting JavaScript tags in your application pages correctly, or that you have correctly integrated the mobile SDK.
Verify that Bot Defense is Injecting JavaScript Tags in Your Application Pages
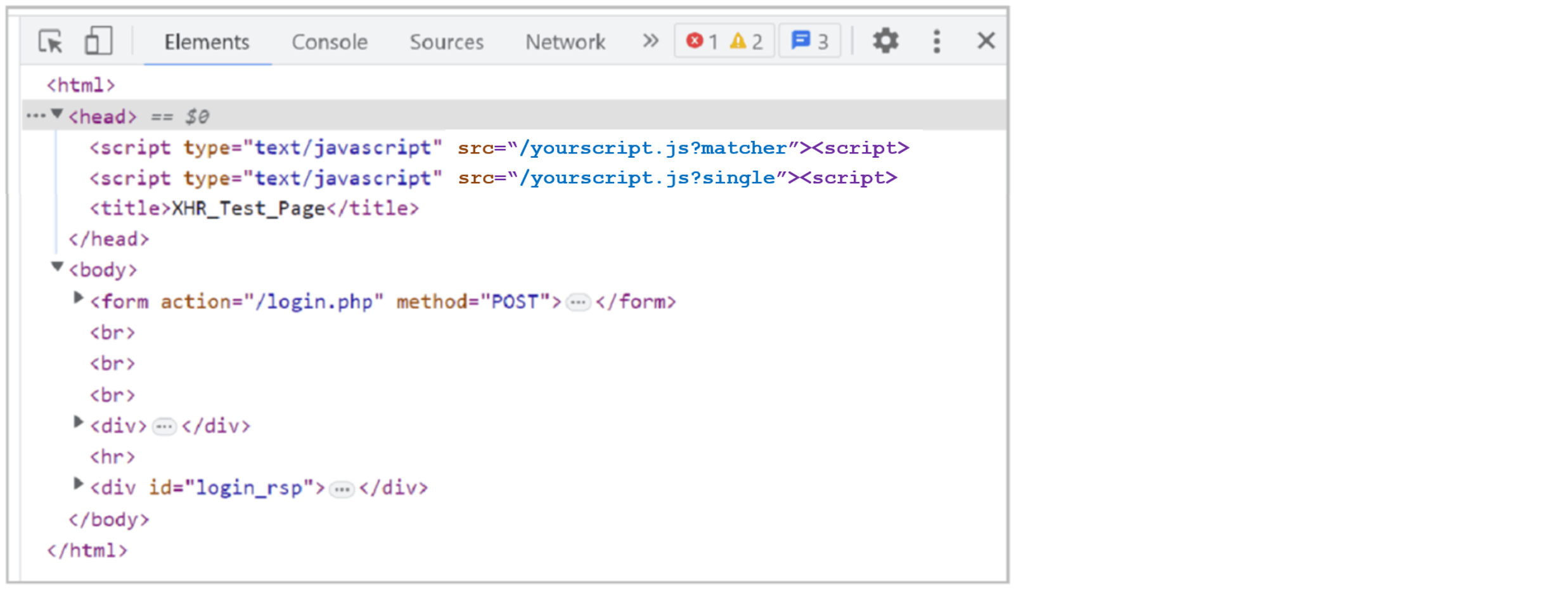
To confirm that Bot Defense Standard added JavaScript tags to an entry page, use the following procedure to inspect the page in your browser and look for Bot Defense-specific headers.
-
Open one of the application pages you chose to protect.
-
Use the developer tools in your browser or view the page source to inspect the page and confirm that Bot Defense has inserted JavaScript tags with the query string parameters:
?matcherand?single. For example:yourscript.js?matcher
yourscript.js?single
Figure: JavaScript tags
If the JavaScript tags appear correctly, then Bot Defense is injecting JavaScript tags into your application pages. If you do not see both JavaScript tags, check your configuration to confirm it is correct. If necessary, contact F5 Support for additional assistance.
Verify Mobile SDK Integration
If you chose to integrate the F5 Mobile SDK with your mobile application, perform the following tasks to verify that you integrated it correctly:
-
Review the SDK integration documentation that you received from F5 and confirm that you followed all integration steps.
-
SDK Initialization
- Deploy the application on a device for the first time (if the device already has the application, remove it before this test).
- Start the application.
- On the Bot Defense Dashboard or the Traffic Analyzer, filter by your client IP address and look for a GET request configuration fetch from your application. If you do not find the GET request, recheck your configuration. For additional assistance, contact F5 Support.
-
Decorated Request
- Make a request for every protected URL.
- On the Bot Defense Dashboard, filter by your client IP address. All protected requests should be marked as “Human.”
-
Mitigation
- Temporarily alter the application code so that it does not call
getRequestHeaders. - Launch the application and make protected requests.
- On the Bot Defense Dashboard, filter by your client IP address. All protected requests should be marked as “Automation.” A GET request configuration fetch should appear immediately after each blocked mitigated request.
- Update your code to call
getRequestHeadersagain.
- Temporarily alter the application code so that it does not call
Successfully complete all test cases to confirm that your integration is working correctly.
Note: F5 recommends that you incorporate these mobile SDK test-cases into your standard regression testing.
Before you release a new application into your production environment, F5 recommends that you set the mitigation action for the application to Continue or Flag and then perform a false positive analysis on your traffic.
Analyze Bot Defense Results
After you enable Bot Defense Standard in your production environment, before you enable mitigation actions for your web and mobile applications, you must confirm that Bot Defense is working as expected and that no legitimate traffic is marked as automation. F5 recommends that you also explore your traffic reports and examine anything unexpected. Resolve all issues before you enable the Block or Redirect mitigation actions.
Analyze Protected Website Traffic
Perform the following tests to help confirm that Bot Defense Standard identifies web traffic correctly.
-
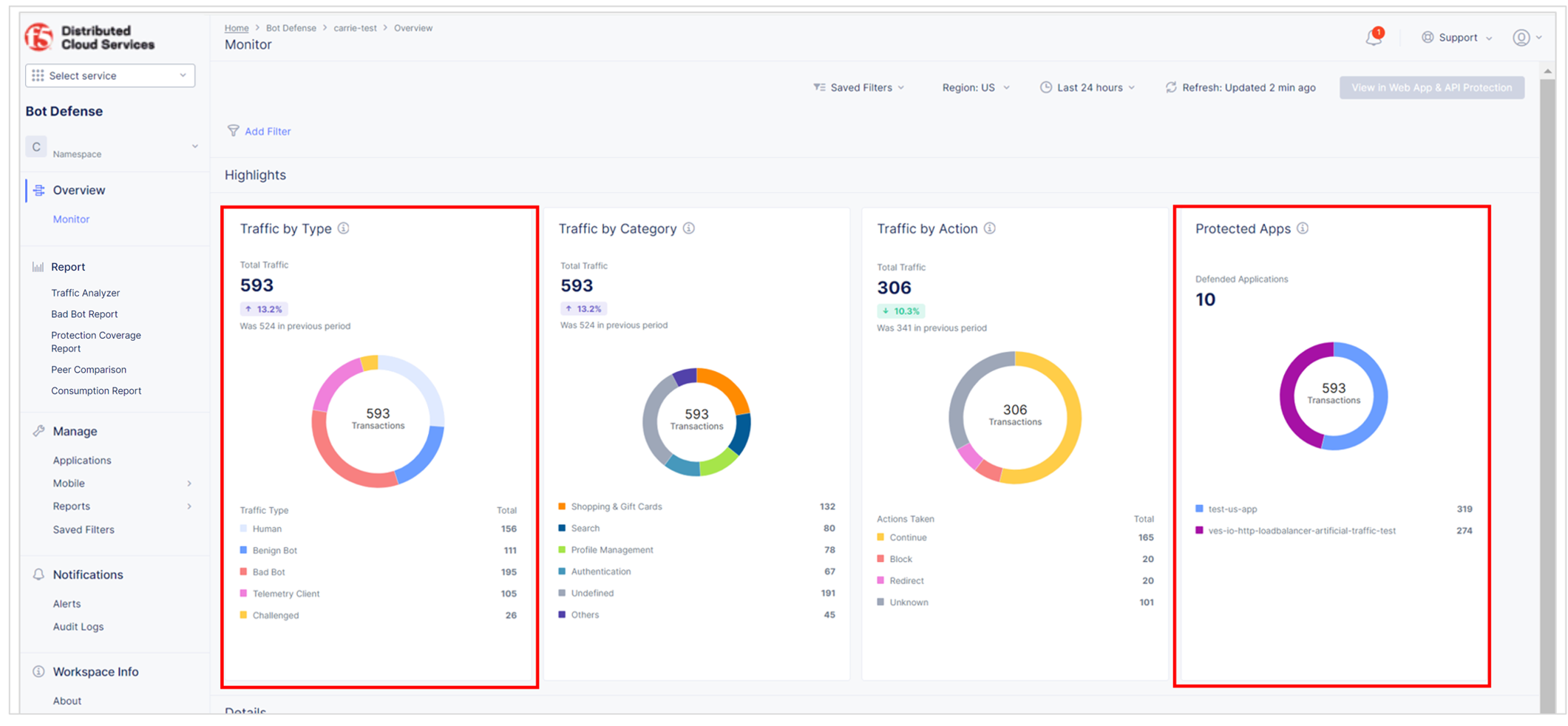
Review the Bot Defense dashboard to see the types of traffic identified by Bot Defense. From the Bot Defense Home page, select Overview > Monitor.
- In the Protected Apps Overview widget, check that your protected application is listed and that the amount of traffic is appropriate.
- In the Traffic Overview widget, check that the level of human, benign bot, bad bot and other activity is appropriate.

Figure: Bot Defense dashboard
From the time-period drop-down menu, select Last 24 hours. In the Traffic Visualized section, check whether traffic marked as malicious increases during the day and decreases at night. If so, this might indicate human traffic.

Figure: Timeframe controls
-
From the Bot Defense Home page, select Report > Traffic Analyzer.
-
Look at the distribution of IP addresses and the countries of origin. Confirm that this distribution looks like it comes from your normal user base.
-
Look at the User Agent column and decide if there are any suspicious user agents present. You can also use this technique to identify wanted automation (benign bots), such as test tools or SEO bots.
-
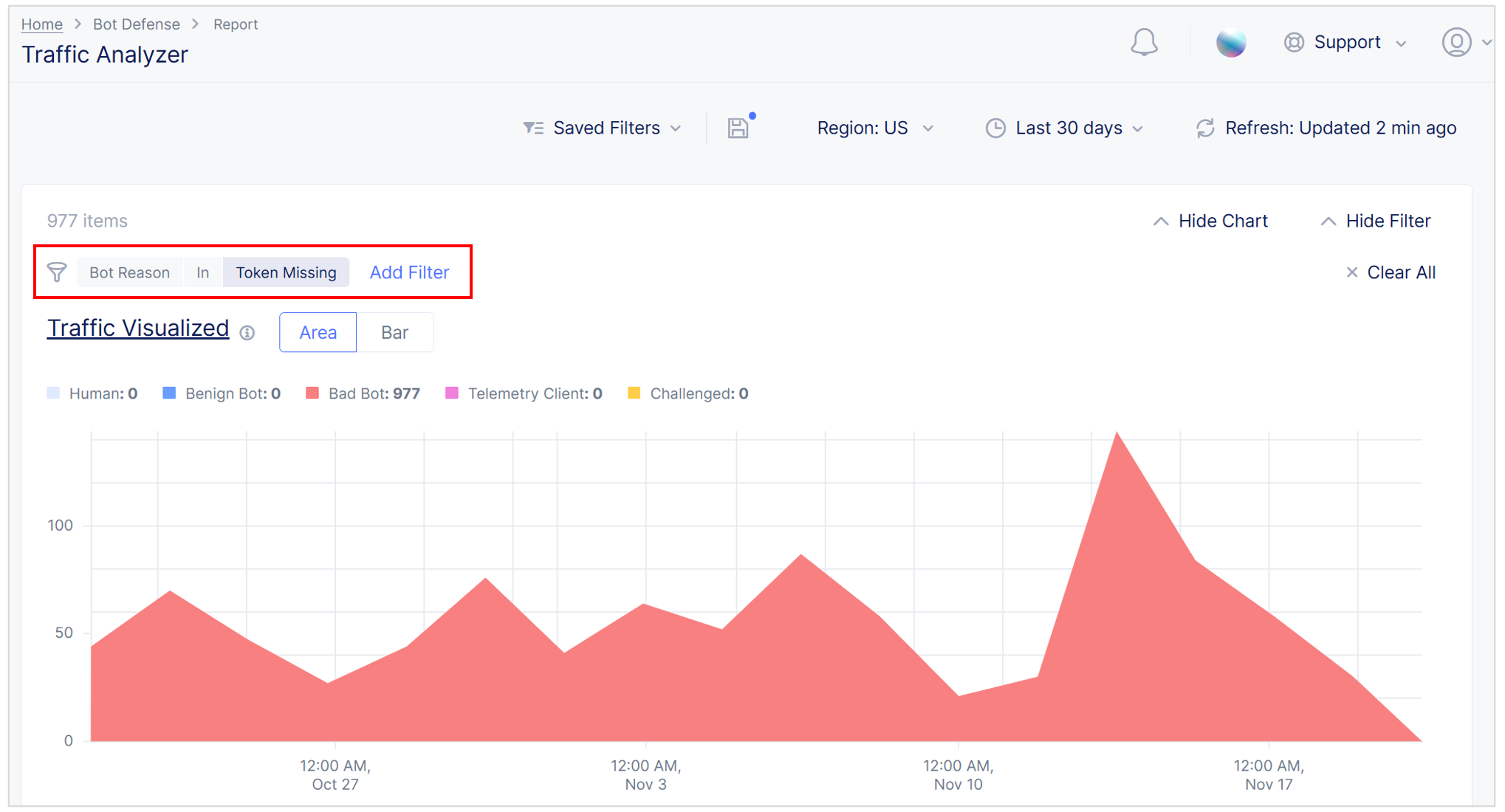
Select Add Filter. From the drop-down menu, select Bot Reason, select In, select Token Missing and select Apply. Review the traffic and determine if it looks legitimate.
If a normal user request appears in the "token missing" results, it could mean that one of the following occurred:
- The Bot Defense JavaScript did not run.
- Another JavaScript on the page interfered with the Bot Defense JavaScript.
- The request was made before the Bot Defense JavaScript loaded.
When this happens, change the Web Client JavaScript Mode for the endpoint to Sync JS with no Caching, and change the JavaScript Location for the endpoint to
After <head>.These configuration changes help rule out interference from other JavaScripts that are being executed on the page, help eliminate any potential race conditions when the Asynchronous option is used and minimize any potential network issues.

Figure: Traffic Analyzer report
If you see legitimate traffic flagged as automation, determine if you can add it to an Allow list.
-
Analyze Protected Mobile Traffic
Perform the following tests to help confirm that Bot Defense Standard identifies mobile traffic correctly.
- Confirm that the number of protected requests with no telemetry headers is low or non-existent and that requests with headers are marked as Human.
- Confirm that configuration update requests are made at an expected rate. Each configuration fetch corresponds to approximately one user session.
Review your traffic reports and examine any unexpected results. Resolve all issues before you enable mitigation actions.
Analyze Protected Requests
Perform a false positive analysis to determine if Bot Defense marks any legitimate traffic to your mobile application as non-human.
- In the Bot Defense Traffic Analyzer report, add the User Agent filter.
- Select In and then select your application version.
- Then select Apply.
Important: Make sure the Bot Reason and Traffic Type columns are displayed.
In the list of filter results, is any traffic marked as non-human? For example, is traffic identified as Benign Bot or Bad Bot? If yes:
- If the Bot Reason column displays Token Missing, look at the IP distribution and decide if the traffic looks like user traffic or automation. Is the traffic limited to a particular platform (iOS or Android)?
- If the Bot Reason column displays something other than Token Missing, but the traffic looks human, this is unexpected behavior. Investigate or contact support@cloud.f5.com for assistance.
- If the IP Address distribution looks organic and is not concentrated on only a few specific IP addresses, this might indicate that there is a problem with your SDK integration.
- In the Path column, carefully examine the URLs that are being marked as illegitimate. If traffic from the URLs that are marked as malicious increases during the day and decreases at night, this might indicate human traffic. Additionally, if the traffic is from a wide range of IP addresses, it can also indicate human traffic.
If the flagged traffic is an expected automation, for example, for a monitoring service, determine if you can add the IP addresses to an Allow list.
Review Configuration Update Request Frequency
Mobile applications that are integrated with the F5 Mobile SDK fetch new configuration settings from Bot Defense at specific times during the application lifecycle, including:
- At application launch
- At mitigation
- After four hours (if the application is in the foreground).
Typically, there is approximately one configuration fetch during each active user session. Since some users launch an app but do not proceed further, and others have two sessions within the same four-hour period, it is normal to see an average of 0.5-2 sessions per configuration fetch.
How you view configuration fetches depends on how you host your application pages you want to protect. The following sections provide information about how to find the number of configuration fetches in each platform.
Note: For all third-party platforms, including Cloudflare, Amazon CloudFront, Adobe Commerce Cloud and Salesforce Commerce Cloud, use the native logging and reporting capabilities of your platform to view configuration fetches. For information, see the documentation for your platform.
View Configuration Fetches in Web App & API Protection
When you use Bot Defense enabled on an HTTP load balancer in Web App and API Protection (WAAP), you can use the Security Dashboard in WAAP to view configuration fetches requested by the mobile application you integrated with the F5 Mobile SDK.
To view the number of configuration fetches:
-
Log into Web App & API Protection (WAAP) and check to make sure you are in the correct namespace.
-
From the Web App & API Protection navigation panel, select Overview > Dashboards > Security Dashboard.
-
In the Load Balancers widget, select the name of the load balancer that services your production traffic.
-
Select the Requests tab.
-
Add one of the following filters:
- For Android applications, enter
req_path in /v1/android/update. - For iOS applications, enter
req_path in /v1/ios/update.
- For Android applications, enter
-
Look at the number of items returned by your search. The number of items should be equal to the number of user sessions you observed during the same period.
For example, the number of configuration fetches should be equal to the number of login requests you observed during your false positive analysis.
View Configuration Fetches in BIG-IP
For BIG-IP versions 14-17 and later, use your native BIG-IP log files to view configuration fetches. For information on viewing BIG-IP log files, see your BIG-IP documentation.
Next Steps
After you confirm that Bot Defense is functioning as expected, that legitimate traffic is not being marked as automation, and that your mobile applications are communicating properly with Bot Defense, you can enable mitigation actions. For information see Configure Mitigation Actions.
On this page:
- Verify that Bot Defense is Injecting JavaScript Tags in Your Application Pages
- Verify Mobile SDK Integration
- Analyze Bot Defense Results
- Analyze Protected Website Traffic
- Analyze Protected Mobile Traffic
- Analyze Protected Requests
- Review Configuration Update Request Frequency
- View Configuration Fetches in Web App & API Protection
- View Configuration Fetches in BIG-IP
- Next Steps