Plan Your Bot Defense Standard Deployment
Bot Defense Standard protects your applications from automated attacks by identifying and mitigating malicious or bad bots. For more information about Bot Defense, see Bot Defense Overview.
When you deploy Bot Defense, F5 recommends that you set up a test environment to configure and test different configuration options before you set up your production environment.
After you decide on your final configuration options and are certain they provide the results you want, you can then set up a production environment.
Your configuration and testing process should include the following steps:
- Enable Bot Defense in the Distributed Cloud Console.
- Thoroughly review Bot Defense prerequisite information and decide what resources you want to protect.
- Build a test system to test different configuration options. If you plan to use Bot Defense with BIG-IP v14-16 or with Distributed Cloud Web App & API Protection, you can follow the instructions in the Bot Defense BIG-IP v14-16 Quick Start or Bot Defense Web App & API Protection Quick Start to help you quickly set up your test system. Otherwise, see Configure Bot Defense to see configuration instructions.
- Build your production system. After you finish working with your test system, configure your production system based on the settings you tested and finalized in your test system.
- Test your production system and confirm that it is functioning as you intended.
- Check for false positive results to make sure Bot Defense is correctly identifying traffic. This step allows you to see how Bot Defense is handling live requests rather than just your test requests.
- When you are sure that Bot Defense is correctly identifying traffic, you can enable mitigation actions for your endpoints.
Prerequisites
-
You must have a valid Distributed Cloud Console account. For information, see Getting Started with Distributed Cloud Console.
-
You must have an Organization plan.
-
You or another admin must have the following assigned roles:
- f5xc-bot-defense-admin: Provides advanced administrative access, including Bot Defense subscription management.
- f5xc-bot-defense-user-role (or ves-io-power-developer-role or greater): Provides access for general administration, such as managing protected applications.
- f5xc-bot-defense-monitor-role (or ves-io-monitor-role or greater): Provides read-only access for operations such as viewing dashboards and reports.
- f5xc-bot-defense-report role: Provides permissions to create and manage monthly Bot Defense reports.
You can also create custom roles that include access to the required API groups. Use the above roles for guidance on the required API groups. For a complete list of the API groups included in the above roles, see View RBAC Policy Rules and API Groups.
If you do not have any of these roles, contact your Bot Defense administrator.
-
Depending on how you host your applications, you must have sufficient permissions to configure Bot Defense with your BIG-IP, application platform or content delivery network.
Decide What Resources You Want to Protect
During your planning process, you must decide which applications and endpoints you want to protect. Bot Defense can protect both web and mobile endpoints. For information on the following configuration options, see Configure Bot Defense.
- For applications that route traffic through F5 Distributed Cloud Mesh, you can use the F5 Distributed Cloud Console to configure Bot Defense on your HTTP load balancers.
- For applications that route traffic through BIG-IP:
- If you use BIG-IP version 17.0 or later, you can configure Bot Defense directly on BIG-IP.
- If you use BIG-IP version 14-16, you can download a BIG-IP iApp template to enable Bot Defense with BIG-IP.
- For web application hosted on a third-party content delivery network, you can configure Bot Defense on Adobe Commerce Cloud, Amazon CloudFront, Salesforce Commerce Cloud or Cloudflare.
- For many other third-party applications, you can configure Bot Defense using a custom connector.
- For mobile endpoints, you can either embed the F5 Distributed Cloud Mobile SDK in the application you want to protect, or you can use the F5 Mobile SDK Integrator to automatically integrate the Mobile SDK with your application with no coding required.
Enable Distributed Cloud Bot Defense Standard
To use Bot Defense, you must first enable it in the Distributed Cloud Console.
-
On the Distributed Cloud Console Home page, select Billing.
-
Select Manage > Billing Plan and scroll to the Organization Plan.
-
Under the Organization Plan, select Bot Defense. The Bot Defense landing pages appears.
Note: If Bot Defense is already enabled, the Bot Defense Monitor page appears and you can begin using Bot Defense.
-
From the Bot Defense landing page, select Request Service.
Best Practices
Common best practices
-
When configuring endpoints, use wildcards to terminate the match. For example:
/login*This prevents attackers from adding a slash to the end of the request (for example,
/login/) when both variants reach the same application endpoint.
- When you apply mitigation actions, configure Bot Defense to respond in a way that mimics how your application responds to other invalid requests (for example, when invalid credentials are used), and that you configure error codes and messages similar to other messages and error codes that are generated by your application. This helps prevent an attacker from knowing if the response came from the application or from Bot Defense.
Web application best practices
- Identify the specific URL paths you want to protect with Bot Defense. Typically, endpoints such as login and sign-up pages are more susceptible to bot attacks. Identify and configure only the endpoints you want to protect to avoid unnecessary charges.
- Use wildcards cautiously. Avoid using
/*endpoint configurations where all endpoints are configured for protection by Bot Defense. This can unnecessarily increase your costs.
Protect Mobile Endpoints
To protect mobile endpoints with Bot Defense, you must complete the following high-level steps:
- Review the best practices below for protecting mobile endpoints.
- Download the base configuration for the F5 Distributed Cloud Mobile SDK.
- Use one of the following two options to integrate the F5 Distributed Cloud Mobile SDK with your mobile application:
- Option 1: Update your mobile app to integrate the Mobile SDK library into your Android or iOS application.
- Option 2: Use the Distributed Cloud Mobile SDK Integrator, which enables you to integrate the Mobile SDK with your application without making code changes.
Mobile application best practices
When you configure protection for mobile endpoints, F5 recommends that you follow these best practices:
-
Add Bot Defense headers only to those requests which are also configured for Bot Defense protection in WAAP or iApp. This helps avoid consuming unnecessary transactions from your daily limit.
-
Before you onboard a mobile application, identify all URLs that must be protected.
-
F5 recommends that you integrate the F5 Distributed Cloud Mobile SDK with applications that have forced-upgrade capability. This allows you to upgrade users to the version of the application that you have integrated with the Mobile SDK. If your applications do not have forced upgrade capability then you cannot enable mitigation actions until all users have upgraded to the version of your application that includes the Mobile SDK.
-
F5 recommends that you integrate the Mobile SDK as described in the Mobile SDK documentation, which is included in your SDK download file. If you need to deviate from those recommendations, see the F5 knowledge base for other integration considerations or contact F5 Support.
-
Initialize the Mobile SDK as early as possible in the application lifecycle to ensure the SDK is initialized and ready to add headers before a protected request is made.
-
If you use push notifications on Android, you must be aware of special integration considerations when push notifications are sent to many applications at once. See your Android documentation for information.
-
So that you can examine traffic filtered by a specific version of your application, F5 recommends that you include an application version marker in the User-Agent header of the request.
Example:
User-Agent: sometext MyApp/3.3 sometext -
For all responses returned to protected requests, execute
parseResponseHeaders(). -
Each set of headers contains a unique token. Do not send the same set of headers more than once.
-
The Mobile SDK is obfuscated. If you use code obfuscation, exclude the Mobile SDK so it is not obfuscated again.
-
If your application uses WebView to access the protected content, consider using the JavaScript solution to add telemetry headers to protected requests. See the F5 knowledge base for information about how to use JavaScript with WebView or contact F5 Support.
-
To help you identify SDK integration problems early during development, in your test environment, F5 recommends that you keep your mitigation actions set to Block.
Add a Mobile Base Configuration
To use the F5 Distributed Cloud Mobile SDK or Mobile SDK Integrator to protect mobile endpoints, you must download a mobile base configuration file and bundle it with your mobile application before you release the application in the app store. The mobile base configuration file contains configuration information needed to initialize the Mobile SDK and is used during the first launch of an application that uses the SDK. After the initial launch of the application, SDK calls the Bot Defense server and downloads new configuration information each time the application launches.
You can download the mobile base configuration from either Bot Defense Standard or Web App and API Protection (WAAP).
To download the Mobile Base Configuration file:
- Do one of the following:
- In Bot Defense, select Manage > Mobile > Mobile Base Configurations.
- In WAAP, select Manage > Bot Defense Management > Mobile Base Configurations.
- In the Actions column, select the Action menu (…) next to your operating system and select Download Mobile Base Configuration file.
- Save the file in a location you can access easily.
Next Steps
After you download the mobile base configuration file, provide it to your application developers so they can bundle the file with your mobile application that uses the F5 Distributed Cloud Mobile SDK or Mobile SDK Integrator before you release the application in the app store.
Then either work with your developers to integrate the Mobile SDK with your application or configure the Mobile SDK Integrator to automatically integrate the Mobile SDK with your application.
Add the F5 Distributed Cloud Mobile SDK to your mobile applications
To protect your native applications from malicious automation, you can integrate the F5 Distributed Cloud Mobile SDK with your native applications, which allows applications to route traffic to Bot Defense for evaluation. You can download iOS and Android versions of the Mobile SDK from either Bot Defense or Web App and API Protection (WAAP) in the Distributed Cloud Console.
To download the F5 Distributed Cloud Mobile SDK
- Perform one of the following steps:
- In Bot Defense, select Manage > Mobile > Mobile SDKs.
- In WAAP, select Manage > Bot Defense Management > Mobile SDKs.
- In the Actions column, select the Action menu (…) next to the SDK for your operating system and select Download Mobile SDK.
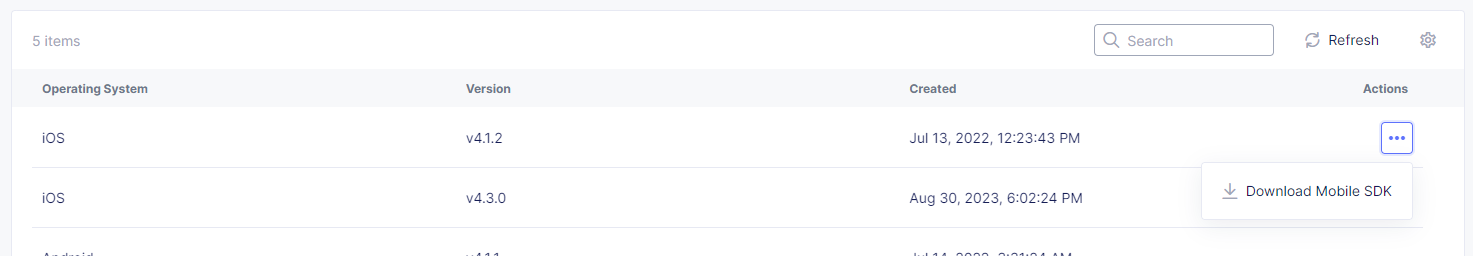
Figure: Download the F5 Distributed Cloud Mobile SDK from Bot Defense
For instructions on how to integrate the Mobile SDK, see the following documentation included in the SDK download file:
- F5 Mobile SDK for iOS Integration Guide (
XC_iOS_IntegrationGuide.pdf) - F5 Mobile SDK for Android Integration Guide (
XC_Android_IntegrationGuide.pdf)
Note: You can also integrate Bot Defense with Flutter, React Native, Xamarin, Xamarin.forms, and Cordova. Contact F5 Support for information about integrating with these frameworks.
Keep the following suggestions in mind when you update your app to integrate the Mobile SDK:
- Use
getRequestHeadersandparseResponseHeaders API, rather than thegenerateHeadersandanalyzeResponse. This API is simpler and meets the needs of Bot Defense. - For body, you can pass in
nilon iOS andnullon Android. - For Bot Defense Standard,
getRequestHeadersalways returns headers, regardless of which URL is passed. For this reason, your developer should only add headers to requests that require protection. - Similarly,
parseResponseHeadersshould be called for every response to the protected requests.
Integrate the F5 Distributed Cloud Mobile SDK using the Mobile SDK Integrator
The Distributed Cloud Mobile SDK Integrator is a no-code solution for integrating the F5 Distributed Cloud Mobile SDK with your mobile application. The Mobile SDK Integrator supports most iOS and Android native apps and can be tied directly into CI/CD pipelines to support rapid deployments.
Use the Mobile SDK Integrator:
- For emergency integrations when you need to integrate quickly.
- If you have apps that use 3rd-party libraries that are not suitable for manual integration.
- If you have multiple apps and need a single integration method that works for all app architectures. The SDK Integrator facilitates a universal integration approach.
The F5 Distributed Cloud Mobile SDK Integrator is available to all Bot Defense customers for an annual subscription fee. For more information about the Mobile SDK integrator or Bot Defense, contact info@f5.com or visit https://www.f5.com/company/contact.
You can download the Mobile SDK Integrator either from Bot Defense or from Web Application and API Protection (WAAP).
To download the Mobile SDK Integrator:
-
On the Distributed Cloud Console Home page, select Billing.
-
Select Manage > Billing Plan and scroll to the Organization Plan.
-
Under the Organization Plan, select Mobile SDK Integrator. The Mobile SDK Integrator landing page appears.
Note: If Mobile SDK Integrator is already enabled, the Mobile SDK Integrator download page appears.
-
From the Mobile SDK Integrator landing page, select Request Service.
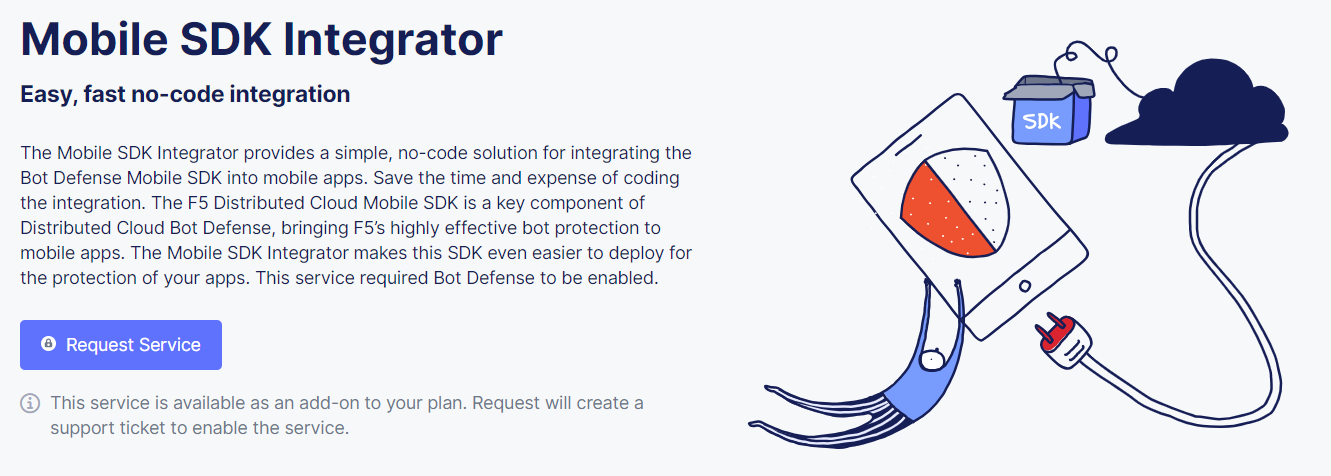
Figure: Mobile SDK Integrator landing page
After F5 fulfills your service request to enable Mobile SDK Integrator, perform the following steps:
- From the Distributed Cloud Console dashboard, do one of the following:
- Select Bot Defense and then select Manage > Mobile > Mobile SDK Integrator.
- Select Web App & API Protection and then select Manage > Bot Defense Management > Mobile SDK Integrator.
- From the Actions column next to the operating system for your app, select the Action menu (…) and then select Download Mobile SDK Integrator.
- Extract the contents of the download file.
Next Steps
After you download and extract the Mobile SDK Integrator, from the extracted file directory, open the documentation for your operating system:
- Android: F5-XC-Mobile-SDK-Integrator-Android.pdf
- iOS: F5-XC-Mobile-SDK-Integrator-iOS.pdf
Review the documentation for additional information about the contents of the extracted download file directory, system requirements and instructions for using the Mobile SDK Integrator.
Configure Mitigation Actions
When Bot Defense detects automated traffic, you can configure the system to take any of the following actions:
-
Continue: Allows traffic to continue to the origin server where your application resides. You can choose to add a header that enables you to monitor traffic in reporting and analytics dashboards.
Note: When you configure Bot Defense on Web App and API Protection (WAAP), this option is called Flag.
-
Redirect: Redirects automated traffic to a different page. You provide the appropriate Status Code and URI where you want to redirect the bot. Use this option to deceive bots into thinking their request successfully went through. You can also redirect to a page with more information for human users that may have been incorrectly redirected.
-
Block: Prevents automated traffic from reaching the origin server where your application resides. You can customize the status code, content type, and body of the response message or use the default values provided by the system.
Important: In the message you display to blocked requests, do not mention “automation”, F5, or Bot Defense so that you do not expose additional information attackers.
Note: Mobile clients only allow Continue and Block. If you select Web and Mobile Client, you can select mitigation actions for each client type.
F5 recommends that you select a mitigation response that mimics how the application responds when a request is invalid (for example, when invalid credentials are used).
If you enable Bot Defense through an HTTP load balancer in Web App & API Protection (WAAP), you can configure Bot Defense to distinguish between malicious automation (bad bots) and benign bots (good bots). This allows you to apply mitigation actions only to malicious automation or to both malicious and benign bots.
Enable mitigation actions
When you initially set up your Bot Defense deployment, F5 recommends that you set your mitigation actions to Continue (Flag), which logs, but does not block, any traffic. When you complete your testing and are sure that the system properly identifies malicious traffic, you can enable the Block or Redirect mitigation actions to protect your endpoints from malicious traffic.
Important: Before you enable mitigation actions, F5 strongly recommends that you complete a false positive analysis of your traffic.
To enable mitigation actions for malicious traffic:
- Update the mitigation actions in your web and mobile endpoint configurations.
- If you configured web scraping protection, make sure to update the mitigation actions in your web scraping configuration.
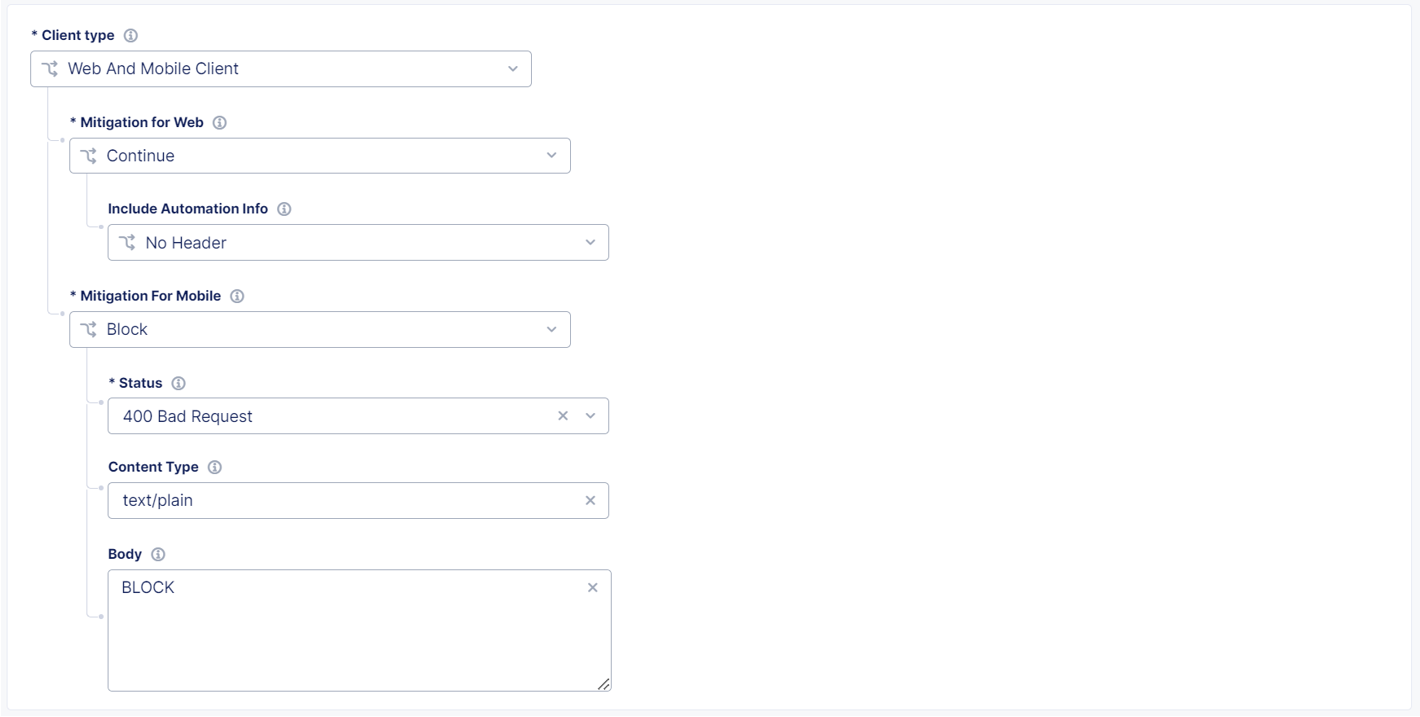
Figure: Configure mitigation actions
For information about how to configure mitigation actions on your specific platform, see Configure Bot Defense and then view the configuration documentation for your platform.
Important: To disable mitigation actions, reset the mitigation action to Continue.
On this page:
- Prerequisites
- Decide What Resources You Want to Protect
- Enable Distributed Cloud Bot Defense Standard
- Best Practices
- Common best practices
- Web application best practices
- Protect Mobile Endpoints
- Mobile application best practices
- Add a Mobile Base Configuration
- Add the F5 Distributed Cloud Mobile SDK to your mobile applications
- Integrate the F5 Distributed Cloud Mobile SDK using the Mobile SDK Integrator
- Configure Mitigation Actions