Manage Roles
Overview
This guide provides an overview of Role-based Access Control (RBAC) for F5 Distributed Cloud Services and includes instructions for managing roles. RBAC helps define and enforce user permissions within the platform.
Refer to the Role-Based Access Control Concepts guide for a comprehensive understanding of RBAC terms and concepts.
Prerequisites
A valid F5 Console Account is required. If you do not have an account, see Getting Started with Console.
View Role Permissions and API Groups
You can view predefined roles policy rules, groups and various API groups information in the F5® Distributed Cloud Console.
Step 1: Log into F5 Distributed Cloud Console, view in-built roles policies.
- Open F5 Distributed Cloud Console homepage, select
Administrationbox.
Figure: Homepage
-
Select
IAMin left column menu > selectRoles. -
Select
>for any policy from the displayed list to view the policy information in JSON format.
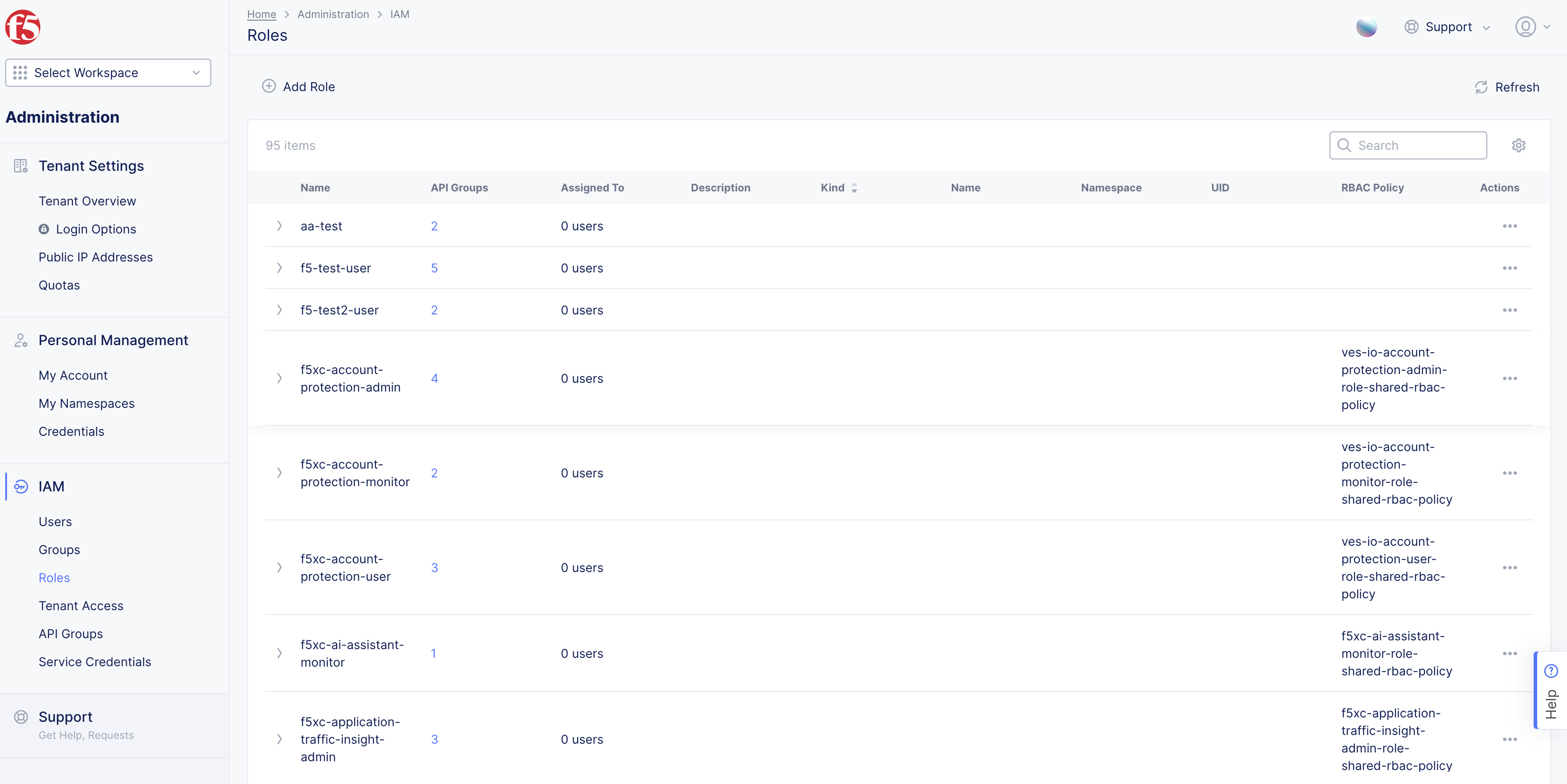
Figure: Open Roles
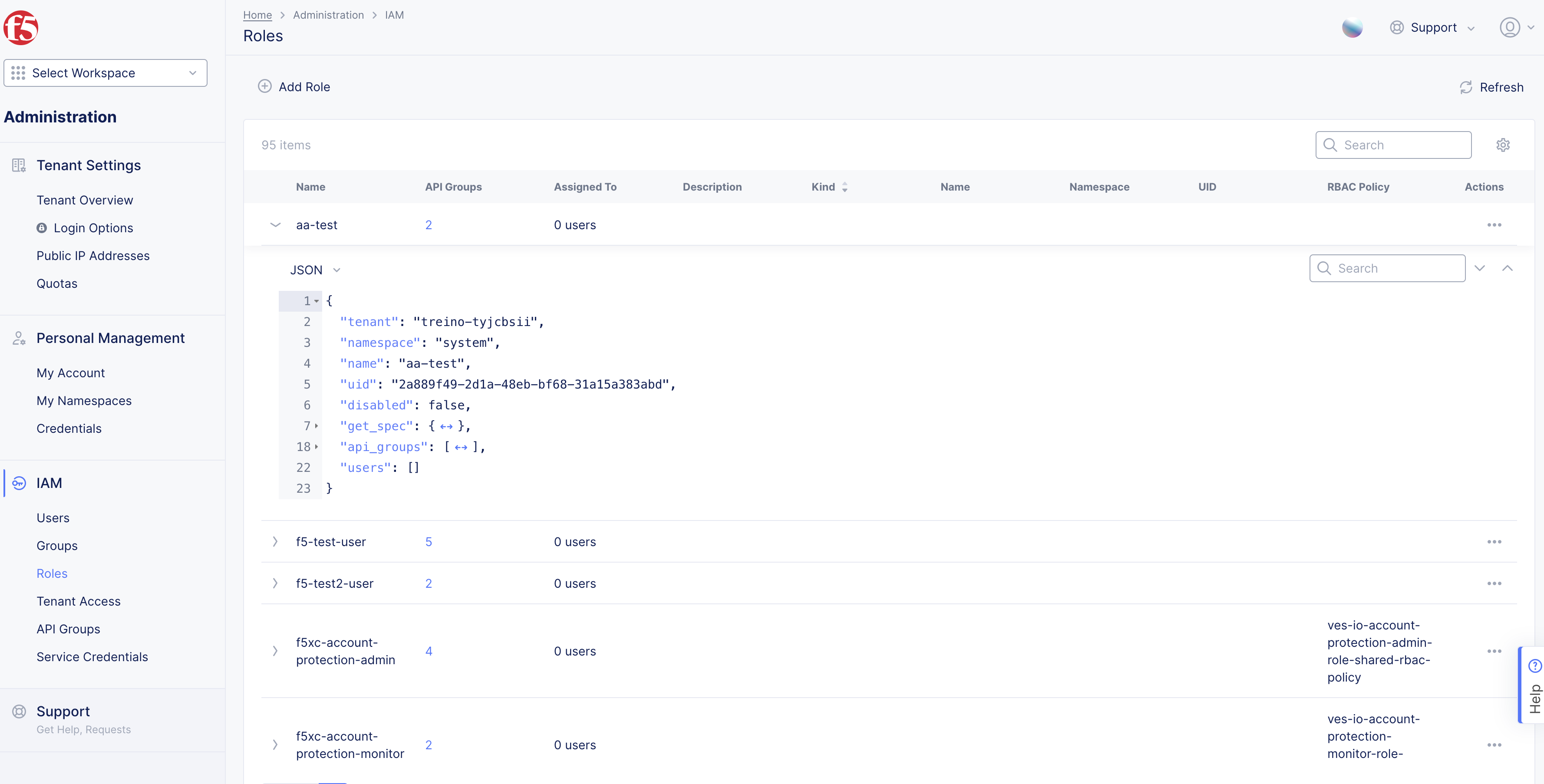
Figure: In-built RBAC Policy Rules
Note: The
api_groupsfield in the displayed information shows the API groups associated with the rule.
Step 2: View API Groups.
-
Select
...(ellipsis) icon, or the linked number underAPI Groupscolumn to view or edit. -
Select
>for any group from the displayed list to view the group information in JSON format.
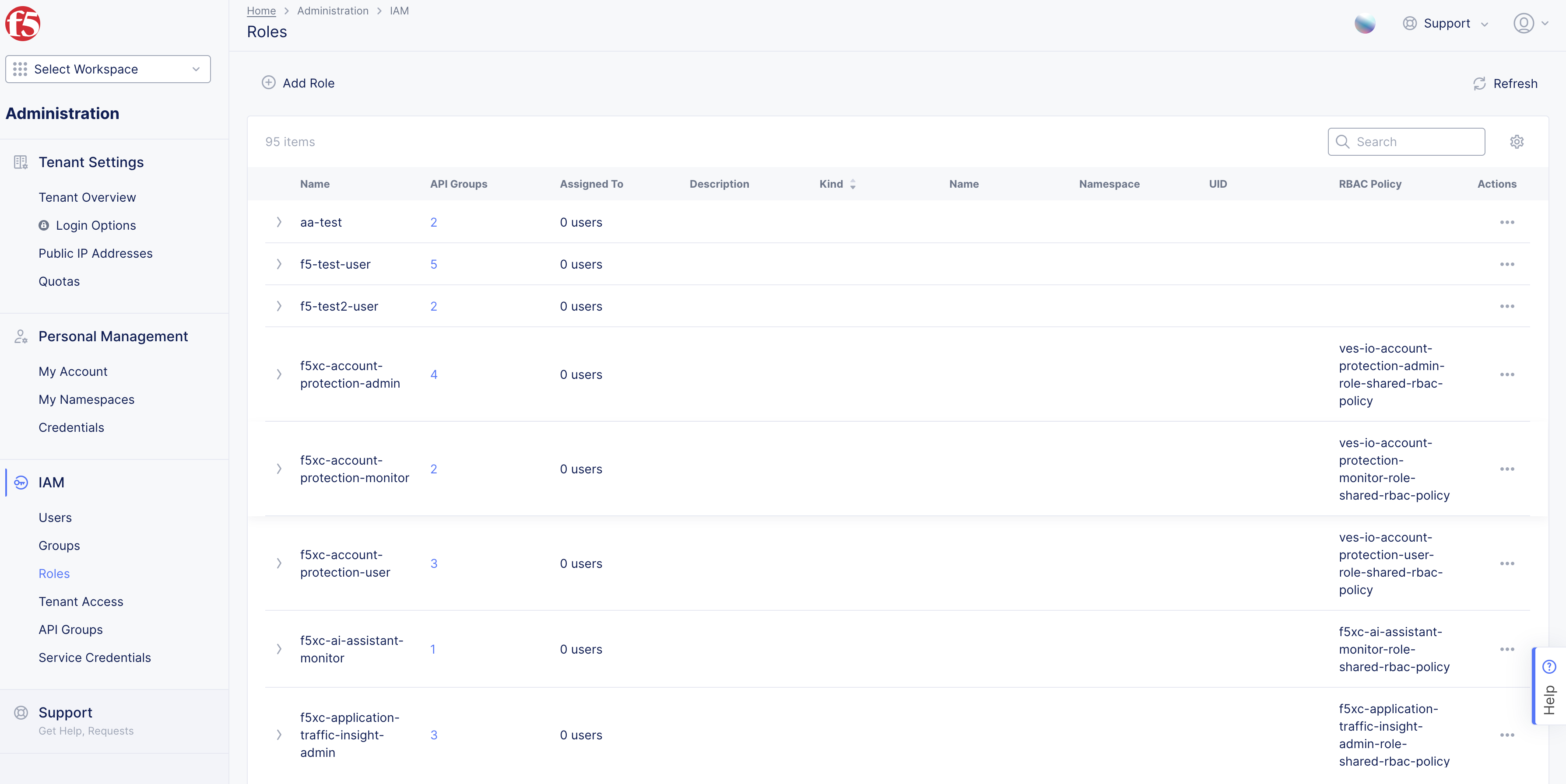
Figure: API Group Information
Note: The
elementsfield in the displayed information shows the APIs associated with the group.
Step 3: View APIs Associated with API Group.
-
Select
...(ellipsis) icon inActionscolumn. -
Select
Edit.
Figure: API Group List
- Select
Elementscolumn linked number to view APIs in another window.
Figure: API Group List
- Review API
Elementsin this window forPath Ranges.
Figure: API Group Elements
Note: Roles are assigned to namespace,
Sharedapplies to all services except system and application.SystemandApplicationare restricted as they are management namespaces for development, SecOps, and more. Not everyone needs or is allowed to access these areas of the console.
Add Role
Follow these steps to add role and assign API groups to it:
Note: At least one API group must be assigned during role creation.
Step 1: Navigate to the Roles Configuration and Open Roles Creation Form.
-
On the
F5 Distributed Cloud Consolehomepage, click theAdministrationbox. -
From the left menu, select
IAM. -
Select
Roles>+ Add Role.
Figure: Navigate to Roles
Step 2: Select API Groups for the Role.
Role creation requires you to select API groups.
- Enter
Namein Role Name box in pop-up window.
Note: When naming your custom role, follow the
RFC 1035naming convention. You can use lowercase letters (a-z), numbers (0-9), and hyphens (-). The first two characters MUST be lowercase letters (a-z). Example: aa-role2-k8s.
- Click
+ Allowed API Groups.
Note: Roles are assigned to namespaces. The "Shared" namespace applies to all services except system and application namespaces. "System" and "Application" namespaces are restricted, as they are used for management purposes (e.g., development, SeCops), and access to these areas is not required or permitted for everyone.
- Select the
Allowed API Groupsby checking box.
Note: Adding objects to a namespace after role creation does not automatically grant role access, you must manually add it.
- Click
Savebutton to assign the selected API groups to the role.
Note: Select the value under the
Elementscolumn to view the list of APIs that are part of the associated group.
Step 3: Add Additional Allowed API Groups.
-
Select the
Allowed API Groupsby checking box. -
Select
Savebutton to create the role.
Note: Role cannot be created without selecting
+ Allowed API Groups.
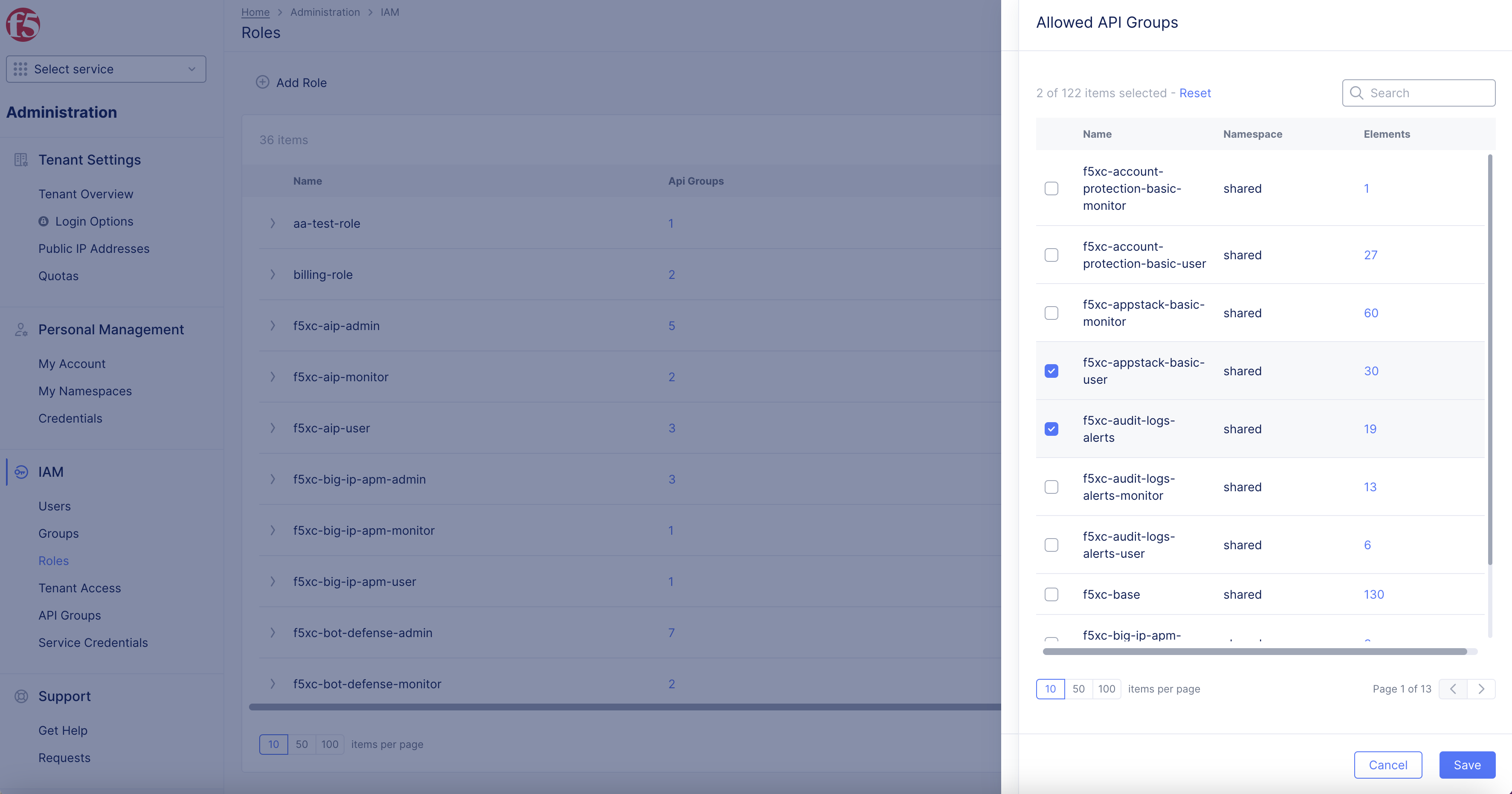
Figure: API Group Selection
Step 4: Add Additional Role Access.
Note: When you add objects to a namespace, role access is not granted automatically, you must assign it manually.
Editing a Role in Administration:
-
Go to
IAM>Roles. -
Select the
Roleyou want to edit. -
Click the ... (ellipsis) icon and choose the
Editoption. -
Click the
+ Allowed API Groupsbutton. -
Check boxes of
Name,Namespace, andElementsrows that you want to grant access to for the role.
Note: Roles are assigned to namespaces. "Shared" applies to all services except for system and application namespaces. "System" and "Application" namespaces are restricted, as they are used for management purposes (e.g., development, SeCops), and not everyone requires or is allowed to access these areas of the console.
-
Click the
>button to view more options on subsequent pages. -
Click
Savebutton to update the role access.

Figure: API Group Selection
Create Tenant-Level Role Policies
F5 Distributed Cloud Services provides the ability to control Console access through Role policies. Tenants can raise service request, and provide list of RBAC policies to apply to platform access.
Role policy rules are the same as service policy rules. For example, tenant can request to enable a rule to allow or deny access based on parameters such as source IP address, ASN, country, and more. See Service Policy API for more information.
When this tenant-level role policy is enabled, it is prioritized over any user-defined and shared role policies.
See Raise Support Request for instructions on how to raise support requests.