Role-Based Access Control Concepts
Objective
This guide provides an overview of Role-based Access Control (RBAC) concepts for F5 Distributed Cloud Services.
Roles and Privileges
Every user can have one or more Roles assigned, and these Roles are mapped to a certain set of privileges. The privileges define the operations the user can perform. Permissions are based on the API Groups associated with the role. Refer to the Manage Roles guide for a comprehensive understanding of Role Permissions and API Groups.
API Groups
Each API Group grants specific permissions (that can be assigned via Roles), determining the range of actions users can perform, from reading information to modifying system settings.
API Groups are critical in managing and setting up access control in F5 Distributed Cloud Console. API Groups are collections of related API endpoints that define the functionalities available to various user Roles.
By categorizing APIs into various services, the platform provides precise control over who can view or change different configurations, allowing user administrators to tailor access rights for a user or team.
Every service on the platform follows a similar pattern to workspaces:
f5xc-${service}-monitorf5xc-${service}-userf5xc-${service}-admin
These service level API Groups are then used to compose Roles.
Roles and Namespaces
-
Role: A role is a collection of allowed API Groups. Users can be assigned one or more roles within multiple specific namespace, with the resulting permissions being the combined access from all assigned roles.
-
Namespaces: A Namespace can also be custom-created under account settings - my namespaces, the System, Shared and Application are the system-defined ones. Refer to the Namespaces section for more details.
Note: Role assignments in System and Shared namespaces must be explicitly specified. For Application namespaces, users can either assign roles to a specific namespace, such as the default namespace, or apply roles to all application namespaces by selecting the "All application namespaces" option in the F5 Distributed Cloud Console. Alternatively, this can be achieved via an API request by using * as the namespace value in the payload.
For a namespace to appear in the namespace drop-down menu of the F5 Distributed Cloud Console, the user must be assigned at least one Role (including one API Group) within that namespace.
If a user is not configured with a role or assigned to a group with a role they will not have access to anything within the console.
Types of Roles
There are two types of roles listed as below:
- System-defined Roles: System-defined roles are the predefined roles provided by F5 Distributed Cloud as managing permissions among users can be complex and time-consuming task. F5 Distributed Cloud simplifies user administration by providing several predefined Roles. These predefined Roles control the privileges of users and broadly correlate to the workspaces listed on the homepage, aligning with the most common use cases and ensuring consistency and security across the platform. See System-defined Roles for more details.
- Custom Roles: You can create and customize Roles by assigning one or more API Groups. Roles can be assigned to users or groups, and updated or removed as needed. See Add Role section.
System-defined Roles
System-defined roles can be utilized to efficiently manage user privileges and capabilities. System-defined roles include Workspace Roles, Utility Roles and Legacy Roles.
Note: System-defined roles or default cannot be changed or customized as they are predefined in the system. If you want to customize a role, refer to the Custom Roles section under Types of Roles.
System-Defined Roles have the following permissions:
- Admin: This role provides full access to a specific workspace, including read and write permissions. Admins can manage resources, configure settings, and implement significant changes. They also have access to "admin-level" APIs when supported by the workspace's services.
- User: This role provides read and write permissions within a designated namespace. Users can view data, check statuses, and modify configurations. However, they do not have access to "admin-level" APIs, even if these are available in the workspace.
- Monitor: Monitor roles are designed specifically for monitoring purposes, offering read-only access to view data and check statuses without the ability to modify configurations.
Types of System-defined Roles
Workspace Roles
- Workspace and Services: Refer to the Workspace and Services section for more details on workspace-service relationship.
Each workspace has generally three levels of permissions in the system-defined workspace roles:
f5xc-${workspace}-monitorf5xc-${workspace}-userf5xc-${workspace}-admin
For example, Web Application and API Protection (WAAP) workspace has these three roles:
f5xc-waap-monitorf5xc-waap-userf5xc-waap-admin
The f5xc-waap-admin Role is a predefined admin role specific to the WAAP workspace. Assigning this role to a user provides them with the following capabilities:
- Read Permissions: can access all data within the WAAP workspace.
- Write Permissions: can modify configurations, create new policies, and manage WAAP settings.
- Administrative Permissions: has access to admin level functions within the WAAP workspace.
See API Groups section for more details.
See below Concept chart on workspace role concept naming for more details.
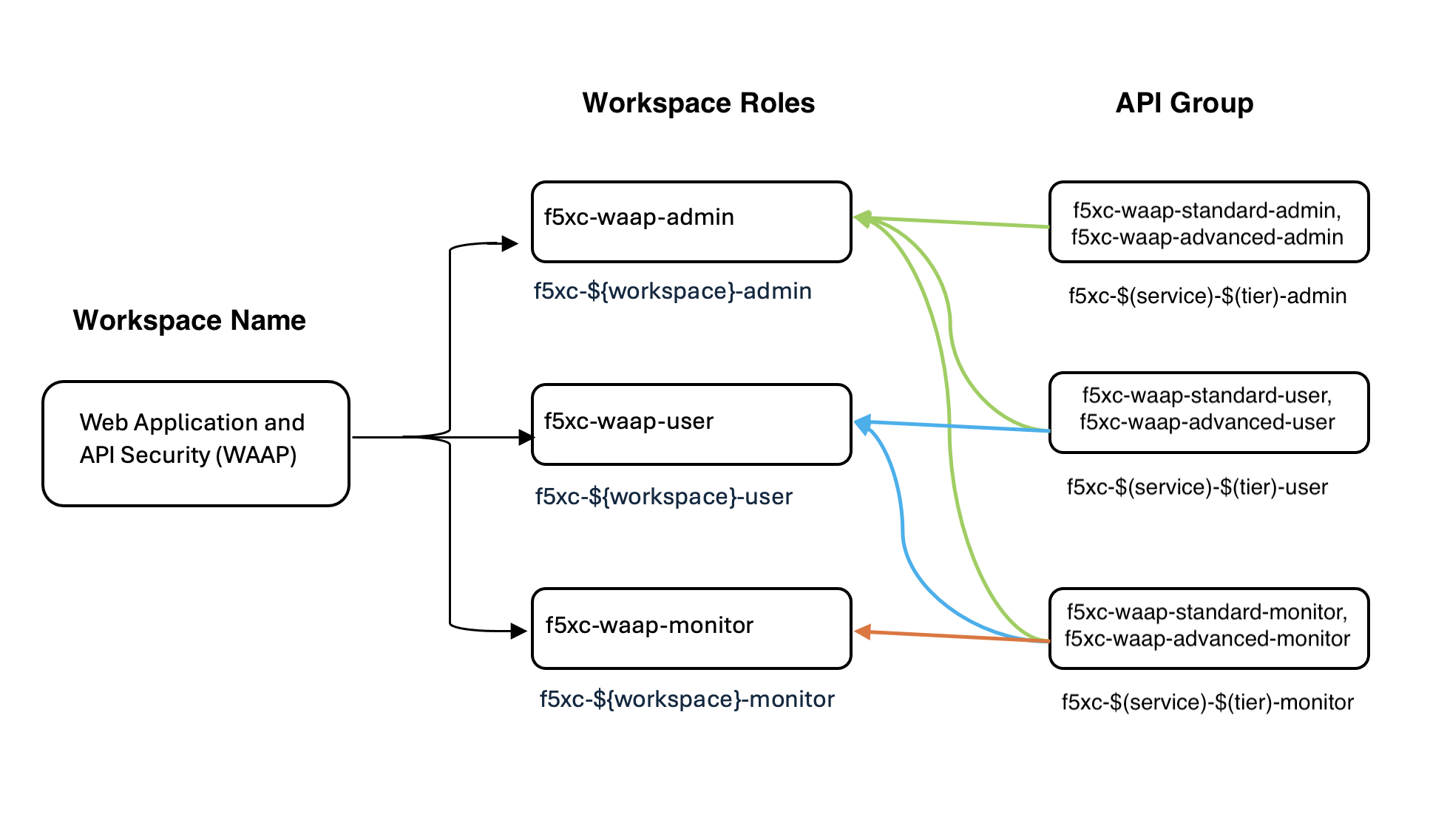
Figure: Workspace Role Concept Chart
-
Role: each default role starts with
f5xcas prefix, describes theworkspacethe role is effective for, and theRBAC level(admin/user/monitor) given on the workspace. Workspace is each tile we see in the console homepage. Roles are named by workspace and RBAC level. -
API group: each API group starts with f5xc as prefix, then service name, then tier if applicable, then RBAC level. See API Groups for more details.
Utility Roles
There are additional utility roles which also start with f5xc- and control important utility functions. Refer to the View Role Permission and API Groups section to review their permissions and allowed API groups before use.
For example, f5xc-console-admin role provides all console admin-level permissions. This role (for system namespace) can be applied for a system admin who can add, edit or delete users and service credentials and view billing, but is not allowed to have tenant owner-exclusive permissions to set login options, tenant settings or delete tenant.
Legacy Roles
Note: Please note that the legacy roles will be gradually replaced by the new roles over several upcoming releases. Once replaced, you will see users previously with legacy roles having the new default workspace roles instead, allowing for granular visibility and control. No further customer action is required.
ves-io-: The F5 Distributed Cloud platform provides a set of predefined roles for user access control. These roles are readily available upon initial console access for all tenants. Be aware that a subset of these roles are legacy roles, identifiable by the prefix "ves-io". For example, the Default Role is ves-io-default-role.
Types of Legacy Roles:
- ves-io-default-role: Only allows for console access but does not allow the user to access any workspaces. Users invited to a tenant, but not assigned any Roles will be given this Role.
- ves-io-monitor-role: Has read only access to assigned namespaces
- ves-io-power-developer-role: Read and write permissions to assigned namespaces. This Role is special in that it also has read permissions to the billing and user management functions in the console.
- ves-io-billing-role: Role specific to the billing admin functions.
- ves-io-uam-admin-role: Role specific to user management, allowing tenant admins to restrict these areas to specific users.
- ves-io-admin-role: Provides full permissions to all APIs to assigned namespaces
Note: The default Role only allows for console access but does not allow the user to access any workspaces. A user must be granted additional permissions to access workspaces.
Related Guides
To understand more about Roles, API Groups and Permissions refer to the Manage Roles document.