View Bot Defense Standard Dashboards and Reports
F5 Distributed Cloud Bot Defense Standard includes multiple ways to view detailed information about the traffic that Bot Defense analyzes. Automated Threat Summaries deliver insights to you automatically each month, while a variety of dashboards provide you with instant, detailed access to analysis of your data.
Note: Bot Defense dashboard and report widgets display the message, "No Data" when there is no data to display. Make sure Bot Defense is configured correctly and that you select a time period for the dashboard or report for which you have collected data.
Automated Threat Summaries
Automated Threat Summaries are emailed reports that summarize your monthly network traffic and Bot Defense activity. Automated Threat Summaries include information about the percentage of your traffic that is automated, the numbers of good and bad bots detected, the number of human visitors to your protected applications and endpoints, and a breakdown of your overall web traffic that is analyzed by Bot Defense.
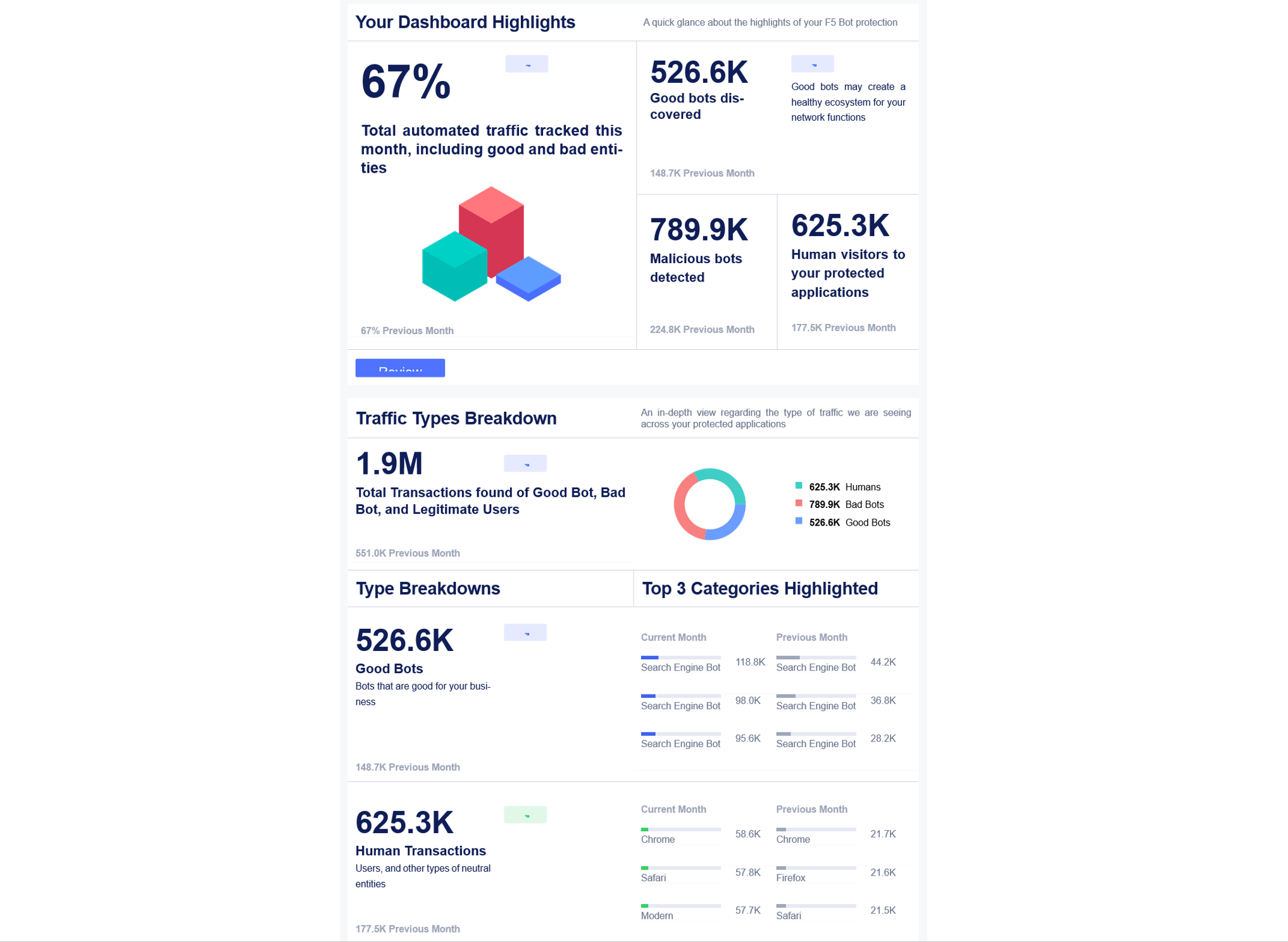
Figure: Automated Threat Summaries
To enable Automated Threat Summaries:
- From the Distributed Cloud Console Home page, select Bot Defense.
- From the Bot Defense navigation menu, select Manage > Reports > Reports Management and then select Add Report.
- Enter a Name for the report and then, from the Report Type drop-down menu, select Bot Defense.
- Select Add Item and then choose the User Group to which you want to send the report. If you need to create a new user group to receive the report, see Users.
- Select Add Report.
Bot Defense Dashboard
The Bot Defense dashboard is a snapshot of all human and bot activity in the web traffic analyzed by Bot Defense for a specified time period. You can view the Bot Defense dashboard in Bot Defense and also in Web App & API Protection:
To view in Bot Defense: In Bot Defense, from the navigation menu, select Overview > Monitor.
To view in Web App & API Protection:
- In Web App & API Protection, from the navigation menu, select Overview > Security.
- In the Delivery Resources widget, from the list of load balancers, select the name of the load balancer you want to view and then select Bot Defense.
- To view additional Bot Defense data for this specific load balancer, such as an overview of protected apps, human traffic by geographic region, an overview of specific bad bot events impacting your applications, and information about the intent of an attack, select View in Bot Defense.
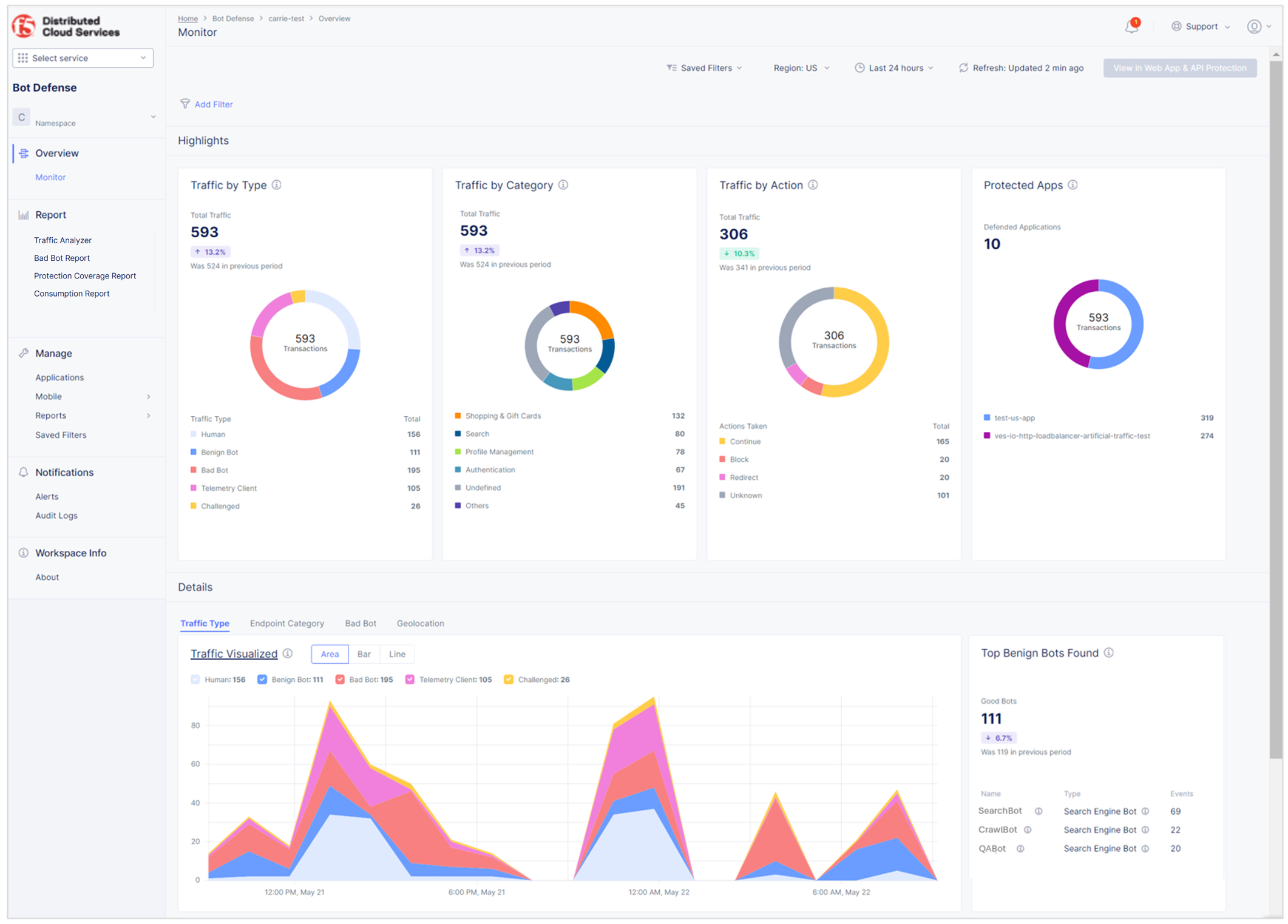
Figure: Bot Defense Dashboard
By default, the dashboard displays data from the last six hours. You can customize the time period and the region that displays. When you view the dashboard from Bot Defense, You can also save and share filters that you apply on the dashboard.
The Bot Defense dashboard includes the following information:
-
Traffic By Type: The total number of transactions in the selected time window categorized by the following traffic types:
- Human: Human or automated traffic that is evaluated but not blocked by Bot Defense.
- Benign Bot: Bots that are harmless or non-malicious, such as SEO bots or test tools.
- Bad Bot: Bots that are malicious, often causing harm to legitimate users, businesses, or organizations.
- Telemetry Client: Traffic that comes from loading the Bot Defense JavaScript in application pages or from configuration requests (fetches) from mobile applications integrated with the F5 Mobile SDK.
- Challenged: Traffic from challenges served to clients on protected GET transactions to determine if the clients are human or automated.
Hover over the donut graph for percentage information for each type of traffic.
-
Traffic by Category: The traffic detected for each endpoint category for the selected time-period. Hover over the donut chart to see percentage information for each category.
-
Traffic by Action: Total number of automated traffic events that reach your protected endpoints and how many times Bot Defense applied each mitigation action to these events. Hover over the donut chart to see percentage information. "Unknown" results display when your connector does not support reporting on the configured mitigation action. Make sure you are using the latest connector configuration.
-
Protected Apps: A breakdown of bad bot traffic by defended application. Hover over the donut chart to see percentage information.
Use the dashboard controls to view additional data.
Figure: Bot Defense Dashboard Tabs
Traffic Type
- Traffic Visualized: Total number of events impacting the applications you protect with Bot Defense over the specified time range as an area chart, bar graph or line graph. Hover over the charts for information about a specific time.
- Top Benign Bots Found: Top benign bots that are visiting your protected applications, including the name and type of bot and total events for each bot.
- Bot API Latency Across Top Protected Apps: Information about traffic latency measured between the top protected application and origin server, including average time, application name, latency per application, and number of transactions.
Endpoint Category
- Category Traffic Visualized: Shows the traffic detected per endpoint category for the time-period selected. Hover over the chart to see totals and percentages for a specific time.
- Top Endpoint Labels: Shows the top 10 endpoint labels on which traffic was detected, and the percentage of traffic detected on the endpoint label in relation to all traffic detected on your system.
- Top Visited Endpoints: Shows the five endpoints that are being attacked most frequently by bad bots. The table includes the host name, endpoint path, and number of malicious requests in the selected time period.
Bad Bot
- Actions Breakdown: A time series chart for mitigated and flagged bad bot events across all protected endpoints displayed as an area chart, bar chart or line graph.
- Top Actions: The number of events to which each mitigation action was applied.
- Top Sources of Bad Bot Traffic: Bad bot traffic analysis by source type, including number of events, IP address and geolocation. Display by Source IP, ASN or User Agent.
- Threat Type: An overview of bad bot traffic by threat type over a selected time period. View as an area or line chart. Hover over the charts to see the number and percentage of each type of attack for a specific time.
- Top Threat Types: An overview of bad bot traffic by threat type listed in descending order.
- Top 5 Sources of Threat Types: A list of the top five sources of each bad bot attack type. Information includes source IP address, autonomous system number (ASN), geolocation, number of events from each source and the percentage of the total for that attack type attributed to the source.
Geolocation
- Traffic from Humans: A map that shows where your human traffic comes from. Hover over each country for additional information about your traffic.
When you filter the Bot Defense dashboard by a single load balancer, select View in Web App & API Protection to view the Load Balancer Bot Defense dashboard for that load balancer.
Figure: View in Web App & API Protection
Traffic Analyzer
The Traffic Analyzer report provides detailed insight into human, benign bot (good bot), bad bot and other traffic on the HTTP load balancer. View traffic as a bar chart or an area chart. Hover over the charts to view traffic totals for specific times.
To view the Traffic Analyzer, in Bot Defense, from the navigation menu, select Report > Traffic Analyzer.
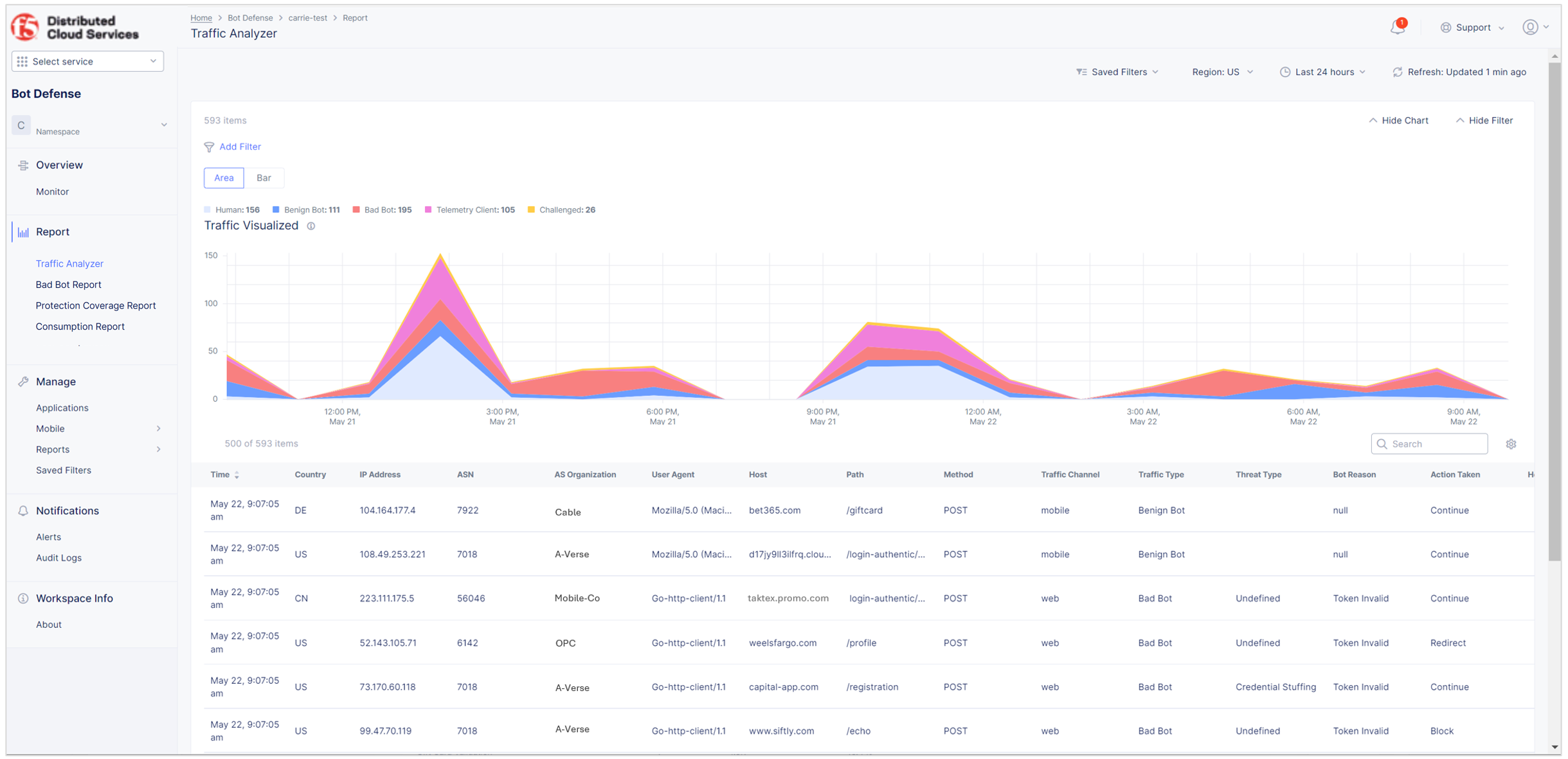
Figure: Traffic Analyzer
In addition to the chart showing transactions per minute for a specified time window, you can also:
- View details about every HTTP request sent through Bot Defense.
- Use the time range drop-down menu or select a specific time in the chart and drag your cursor to another time to display specific time periods. By default, the report displays data from the last six hours.
- Select the region for which information displays.
- Save and share filters that you apply to the report.
- Reorder columns by dragging a column to the left or to the right.
Transaction Detail Panel
The Traffic Analyzer Transaction Detail panel provides information about individual transactions and information about why Bot Defense determined that a transaction was from an automated source.
Select an entry in the Time column to display the Transaction Detail panel.
You can optionally export a JSON file that contains the transactions details so you can share the data for offline analysis.

Figure: Download JSON File
The panel contains the following information:
| Name | Description |
|---|---|
| Information Fields | |
| Time | The date and time of the request. |
| SDK Version | For mobile traffic, the version of the SDK used with the targeted application. |
| IP Fields | |
| IP Address | The IP address where the request originated. |
| ASN | The autonomous system number of the IP address where the request originated. |
| AS Organization | Name of the organization associated with the ASN. |
| Country | The country of origin. |
| Method and URL Fields | |
| Method | The type of HTTP request. |
| Host | The host where the request originated. |
| Path | The path to the flow specified in the request. |
| Referer | The web page where the request originated. |
| Traffic Channel | The type of traffic (web or mobile). |
| Inference Fields | |
| Is Attack | If Bot Defense determined this to be an attack (True or False) |
| Bot Reason | The reason that Bot Defense determined the request was an automated attack. |
| Traffic Type | Whether the traffic was bot or human. |
| Threat Type | Type of attack based on OWASP attack types, for example, scraping, carding, denial of inventory, credential stuffing and account creation. |
| Action Taken | The mitigation action taken by Bot Defense (Continue, Block, Redirect). Bot Defense only applies mitigation actions to automated traffic. When the traffic type is "Human," the "Action Taken" displays as "Not Applicable." |
| Data Labels & Cluster | |
| Flow | The endpoint label assigned to the flow. |
| Agent | Indicates if the client is a legitimate user, illegitimate (failed to provide valid telemetry), on trusted allowlist (for example, your internal users), or on an untrusted allowlist (for example, third parties that you allow to access the application without valid telemetry). |
| Protected Application | The name you assigned to the load balancer, CDN or other application that you added to Bot Defense when you configured your protected endpoints. |
| Latency Fields | |
| Inference Response Latency | The time Bot Defense takes to process transactions and provide inference. |
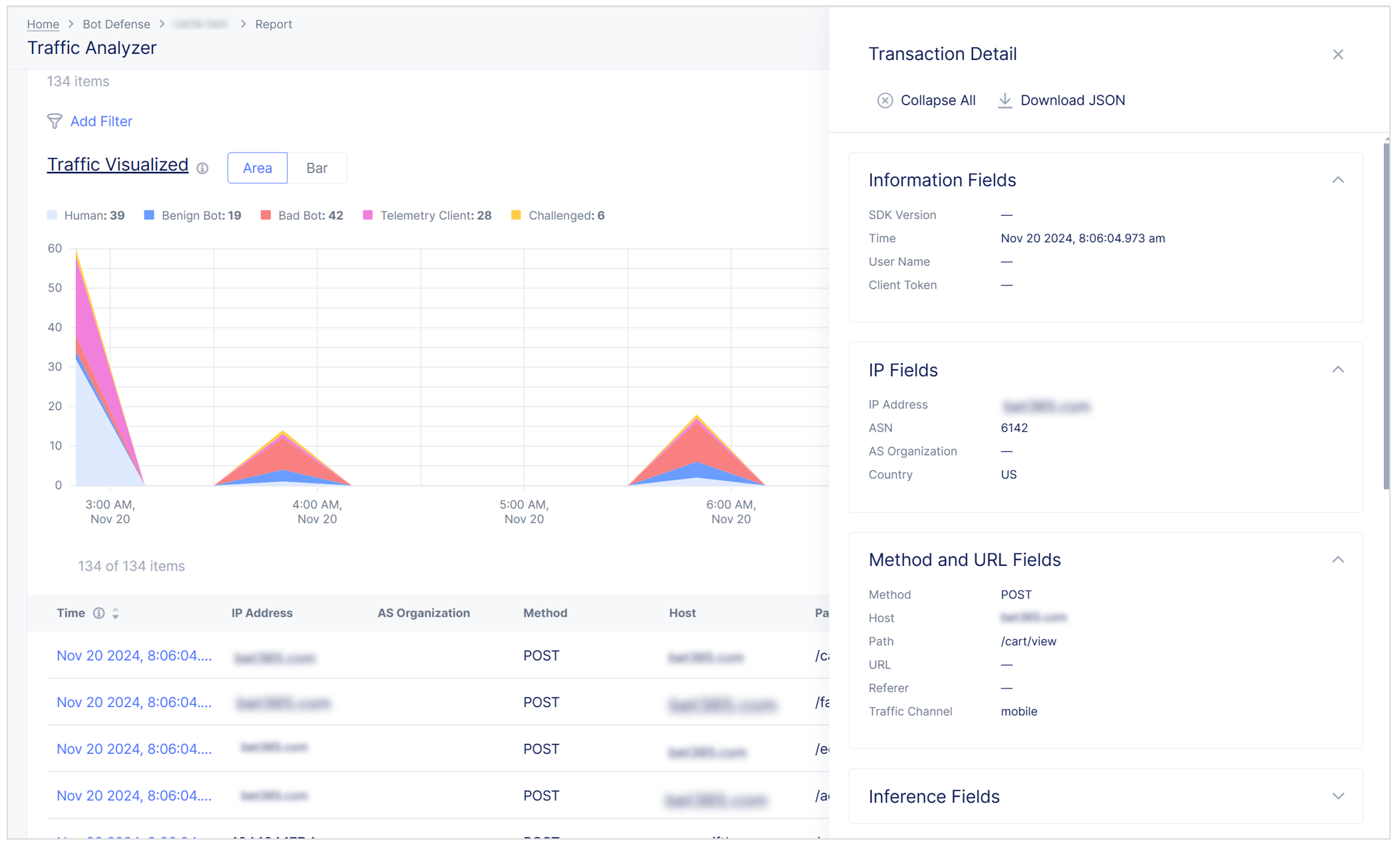
Figure: Transaction Detail
Forensics Panel
The Traffic Analyzer Forensics panel displays the top results for four configurable transaction characteristics captured by Bot Defense, such as top IP addresses from which automated traffic is sent, top traffic type and top mitigation actions taken by Bot Defense.
From the Traffic Analyzer, select Forensics to display the Forensics panel.

Figure: Forensics Panel
You can edit each section of the Forensics panel to display the data you want to see.
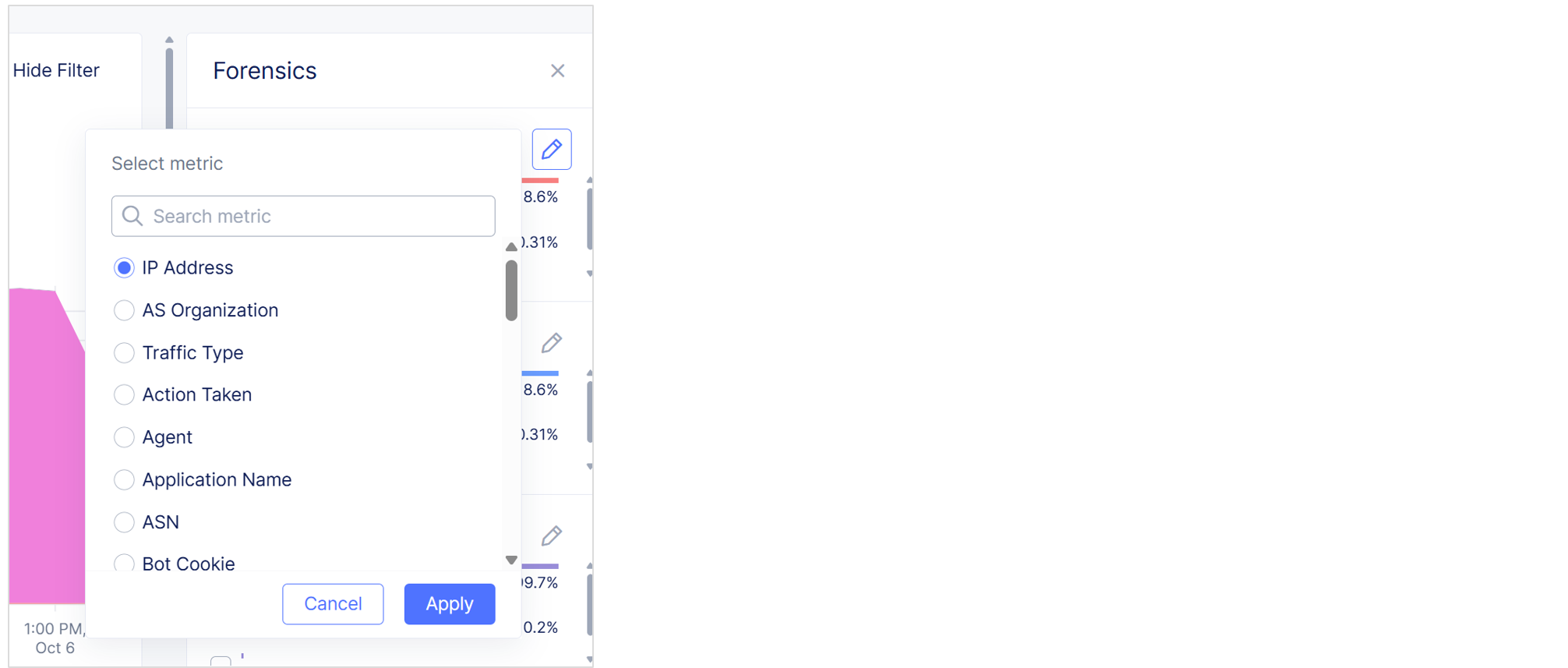
Figure: Edit the Forensics Panel
Select the checkbox next to a result in the Forensics panel to filter the data displayed in the Traffic Analyzer by that result. For example, filter Top Traffic Type so that only traffic from bad bots is displayed and then filter Top IP Address so that the Traffic Analyzer only displays traffic from a specific IP address. Select Apply to apply the filters you select.
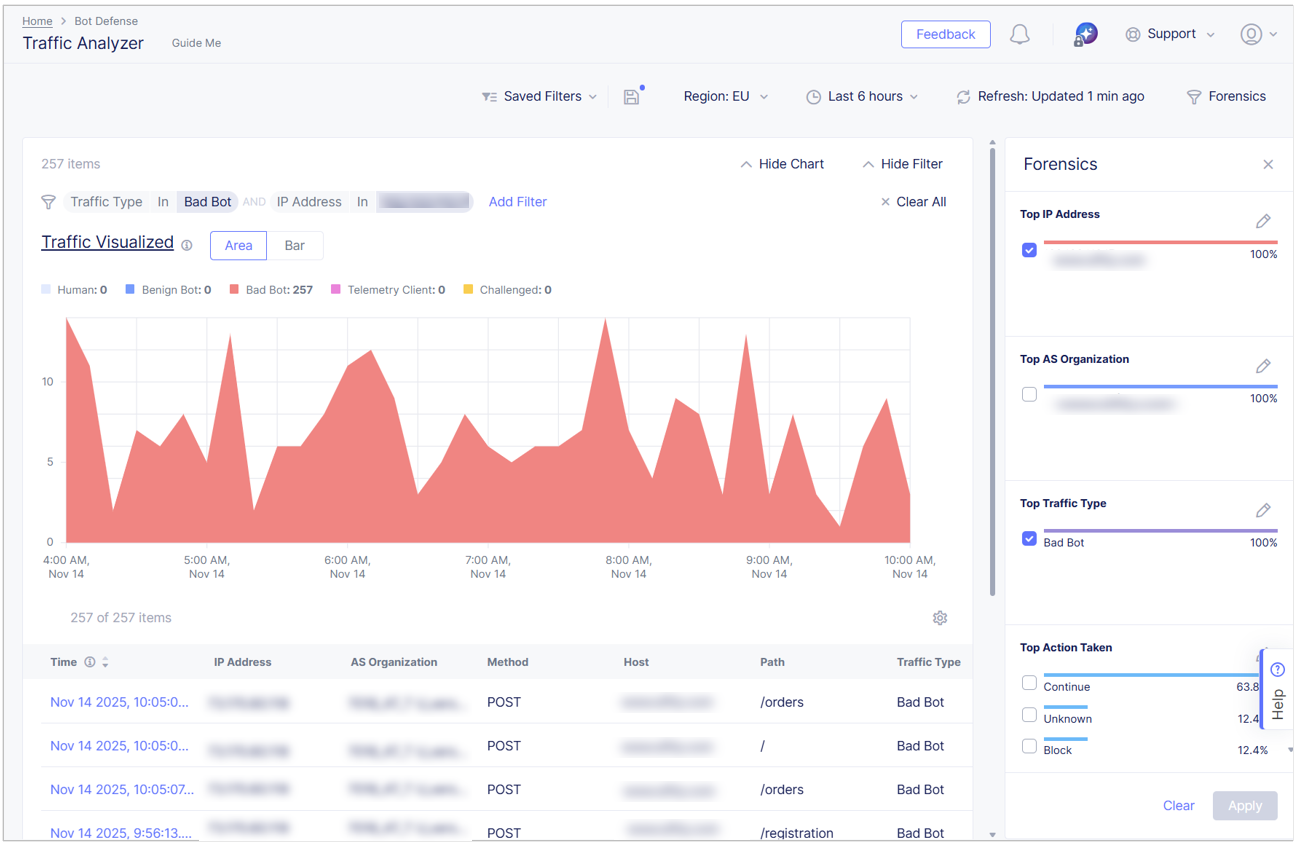
Figure: Filter by Forensics Panel Data
Select Clear All to clear Forensics panel filters.
Bad Bot Report
The Bad Bot Report provides information about malicious automation in your web traffic.
To view the Bad Bot Report, in Bot Defense, from the navigation menu, select Report > Bad Bot Report.
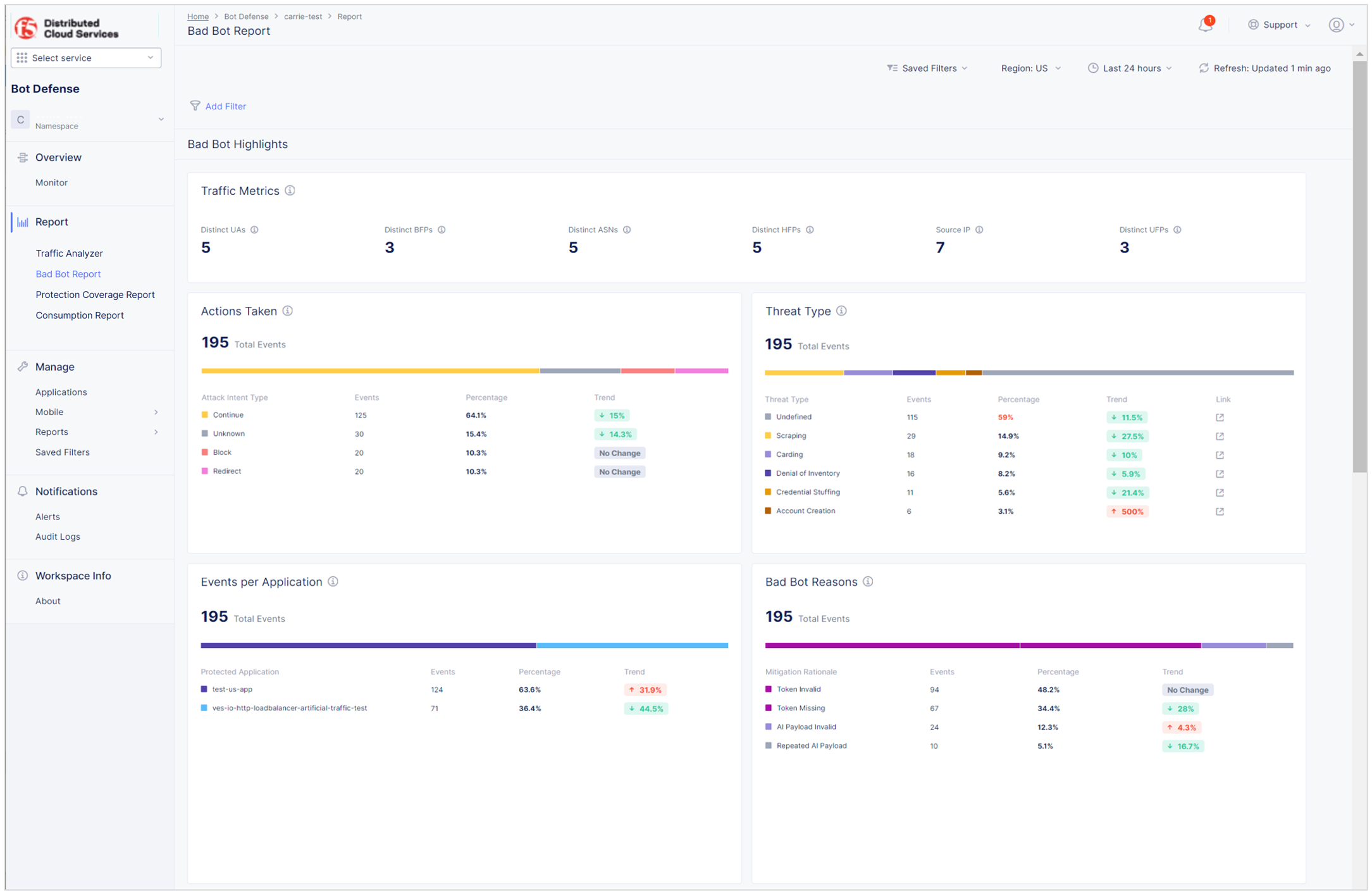
Figure: Bad Bot Report
By default, the report displays data from the last six hours. You can customize the time period and the region that displays. You can also save and share filters that you apply to the dashboard.
The Bad Bot Report includes the following information:
- Traffic Metrics: An overview of the different characteristics of the bad bot traffic that Bot Defense has detected across your protected applications and endpoints.
- Actions Taken: The number of events to which each mitigation action was applied, including percentage information.
- Threat Type: An overview of bad bot threat traffic based on key OWASP attack types to help you see how attackers are targeting your endpoints.
- Events per Application: The number of bad bot events grouped by application. Hover over the chart for totals and percentages for each application.
- Bad Bot Reasons: The top reasons why Bot Defense associated an event with a bad bot, including the number of events for each reason code and percentage, to help you understand how bad bots are attacking your endpoints.
- Bad Bot Traffic: An overview of bad bot traffic by threat type over a period of time.
- Bad Bot Events per Application: An overview of bad bot events that occurred on each protected application. View data as an area chart, bar chart or line graph. Hover over the charts for event totals and percentages on each application at a specific time.
- Bad Bot Traffic Breakdown: An overview of bad bot events impacting your applications across the specified time range. View data as an area chart, bar chart or line graph. Hover over the charts for totals and percentages for a specific time. You can also view bad bot events organized by operating system (OS), browser, user agent (UA), autonomous system number (ASN) or IP address. Explore and investigate detailed event data, including threat types and reason code information. Expand each row to reveal additional total and percentage information. Use Search to find specific events.
- Endpoints with Bad Bot Traffic: An overview of bad bots attacking your protected endpoints.
Protection Coverage Report
The Protection Coverage Report provides information about your protected applications and endpoints and the traffic accessing them.
To view the protection coverage report, in Bot Defense, from the navigation menu, select Report > Protection Coverage Report.
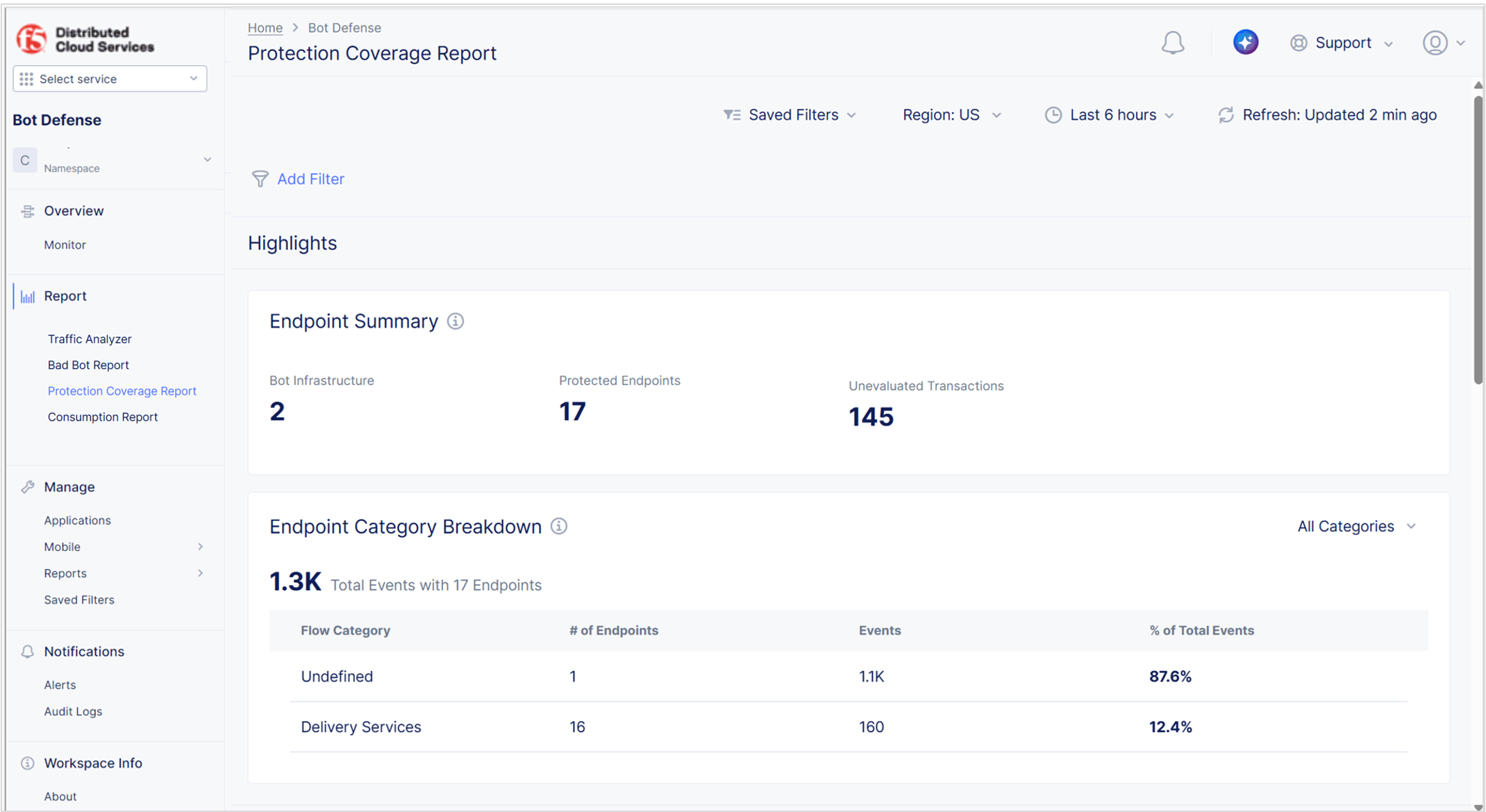
Figure: Protection Coverage Report
By default, the report displays data from the last six hours. You can customize the time period and the region that displays. You can also save and share filters that you apply to the dashboard.
The Protection Coverage Report includes the following information:
- Endpoint Summary: A summary of your protected applications and endpoints during your selected time period.
- Endpoints Category Breakdown: An overview of traffic passing through your secured endpoints. Use the drop-down menu to display data for specific flow categories and associated flow labels.
- Protected Traffic Flow: A visual representation of all traffic visiting your protected endpoints.
- All Protected Endpoints: Information about all of your endpoints that are protected by Bot Defense, including domain, associated application, number of events that took place on the endpoint, and percentage of your total traffic that passed through the endpoint.
Consumption Report
The Consumption Report lets you see how many transactions Bot Defense has processed for the past year.
To view the Consumption Report, in Bot Defense, from the navigation menu, select Report > Consumption Report.
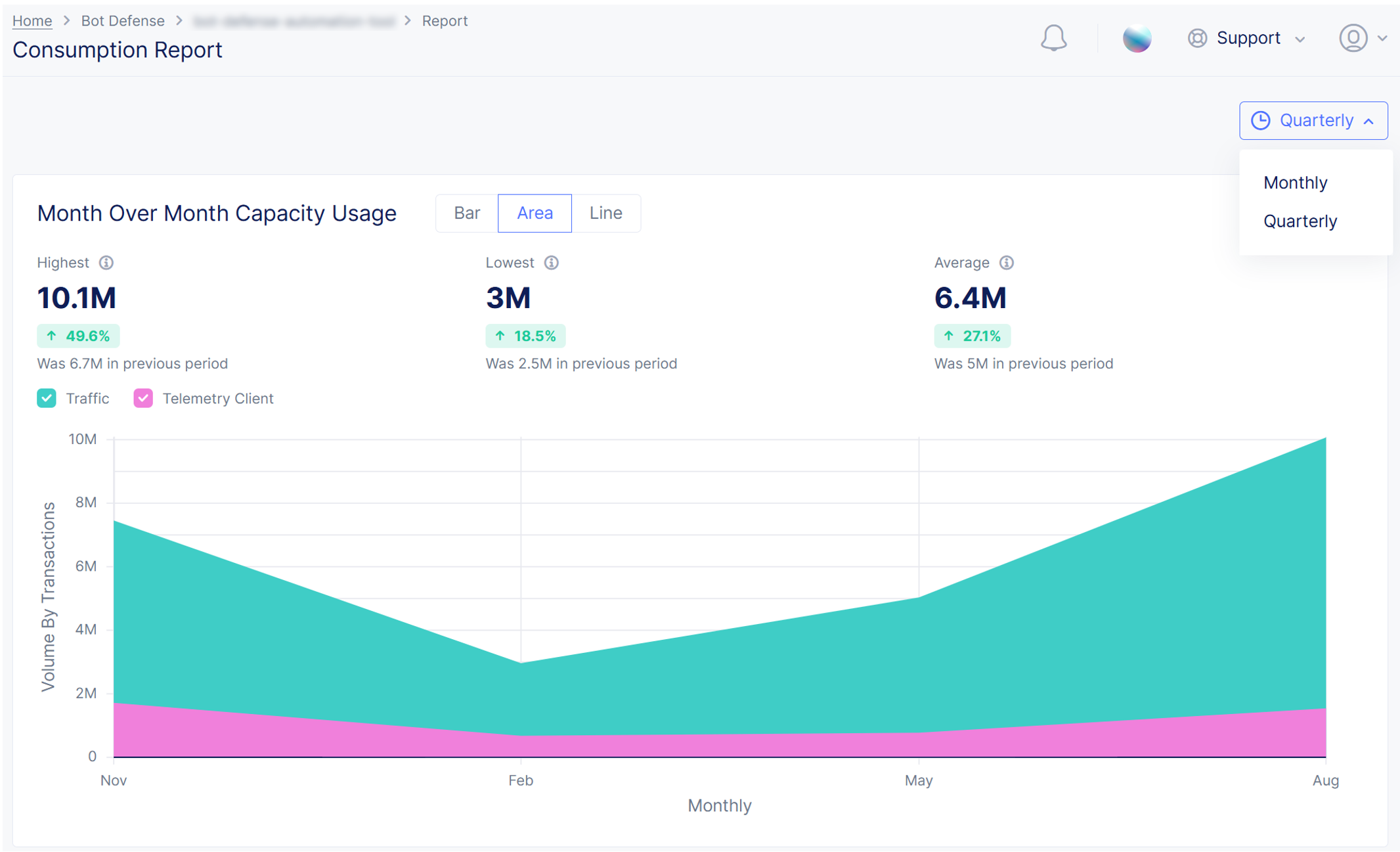
Figure: Consumption Report
This report displays the following information by month or by quarter:
- Traffic: All the traffic on the customer’s web applications that are monitored by Bot Defense.
- Telemetry Client: Traffic that comes from loading the Bot Defense JavaScript in application pages or from configuration requests (fetches) from mobile applications integrated with the F5 Distributed Cloud Mobile SDK.
The report displays data for the past year, starting from a year previous to the current month until the previous month. For example, if the current month is December 2022, data is presented from December 2021-November 2022. Hover over the chart to see information for a given month or quarter.
The following summary data for the previous 24 months is displayed at the top of the report:
- Highest: The highest number of transactions monitored in a given month in the past year, compared with the highest number of transactions monitored in a given month in the previous year.
- Lowest: The lowest number of transactions monitored in a given month in the past year, compared with the lowest number of transactions monitored in a given month in the previous year.
- Average: The monthly average number of transactions monitored in the past year, compared with the monthly average number of transactions monitored in the previous year.
You can display data as either a bar chart, area chart or line chart. Hover over the charts to see data from specific months.
Use the drop-down menu to switch between Monthly and Quarterly views.
Figure: Quarterly or Monthly View Controls
Save and Manage Dashboard Filters
The Bot Defense Dashboard (Monitor), Traffic Analyzer report, Bad Bot report, and Protection Coverage Report allow you to apply one or more filters to view specific subsets of information. Report filtering allows you to:
- Apply and save filters.
- View past dashboard filter combinations.
- Share your saved filters with other users.
- View filters saved by other users.
To apply a filter to a report:
- Open a report and select Add Filter.
- From the drop-down menu, select a filter option.
- Select an operator, such as In, Includes, Does Not Include, Match Regex, Starts With, and so on.
- Select Apply.
For example, to add a filter that displays only automated transactions where the Bot Reason is Token Missing:
Select Add Filter. From the drop-down menu, select Bot Reason, select In, select Token Missing and select Apply.
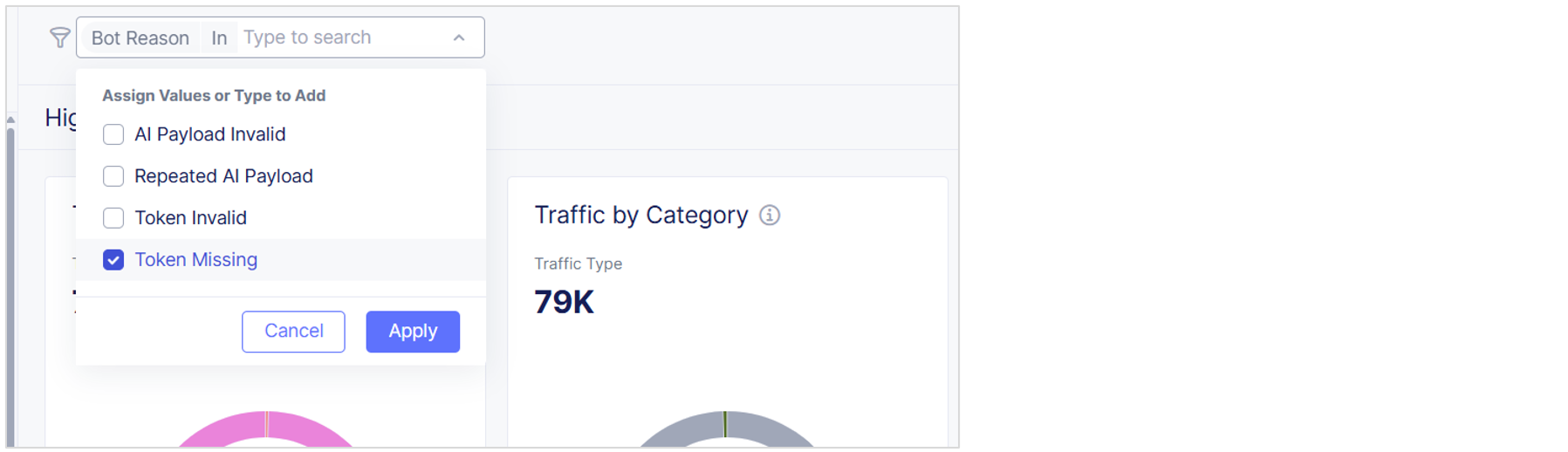
Figure: Filter Example
The following filters are available. Note that not all filters are available in all reports.
| Filter | Description |
|---|---|
| Action Taken | The mitigation action taken by Bot Defense (Continue, Block, Redirect). Bot Defense only applies mitigation actions to automated traffic. When the traffic type is "Human," the "Action Taken" displays as "Not Applicable." |
| Agent | Indicates if the client is a legitimate user, illegitimate (failed to provide valid telemetry), on trusted allowlist (for example, your internal users), or on an untrusted allowlist (for example, third parties that you allow to access the application without valid telemetry). |
| AS Organization | Name of the organization associated with the ASN. |
| ASN | The autonomous system number of the IP address where the request originated. |
| Bot Reason | The reason that Bot Defense determined the request was an automated attack. |
| Country | The country of origin. |
| Flow | The endpoint label assigned to the flow. |
| Host | The host where the request originated. |
| IP Address | The IP address where the request originated. |
| Is Attack | If Bot Defense determined this to be an attack (True or False). |
| Method | The type of HTTP request. |
| Path | The path to the flow specified in the request. |
| Protected Application | The name you assigned to the load balancer, CDN or other application that you added to Bot Defense when you configured your protected endpoints. |
| Referer | The web page where the request originated. |
| SDK Version | For mobile traffic, the version of the SDK used with the targeted application. |
| Threat Type | Type of attack based on OWASP attack types, for example, scraping, carding, denial of inventory, credential stuffing and account creation. |
| Traffic Channel | The type of traffic (web or mobile). |
| Traffic Type | Whether the traffic was human, benign bot, bad bot, telemetry client or challenged. |
Save a Dashboard Filter
-
Use the Add Filter option to filter the data displayed by your report.
-
After you set a new filter that you want to save, select the Save Filters icon.

Figure: Save filters icon
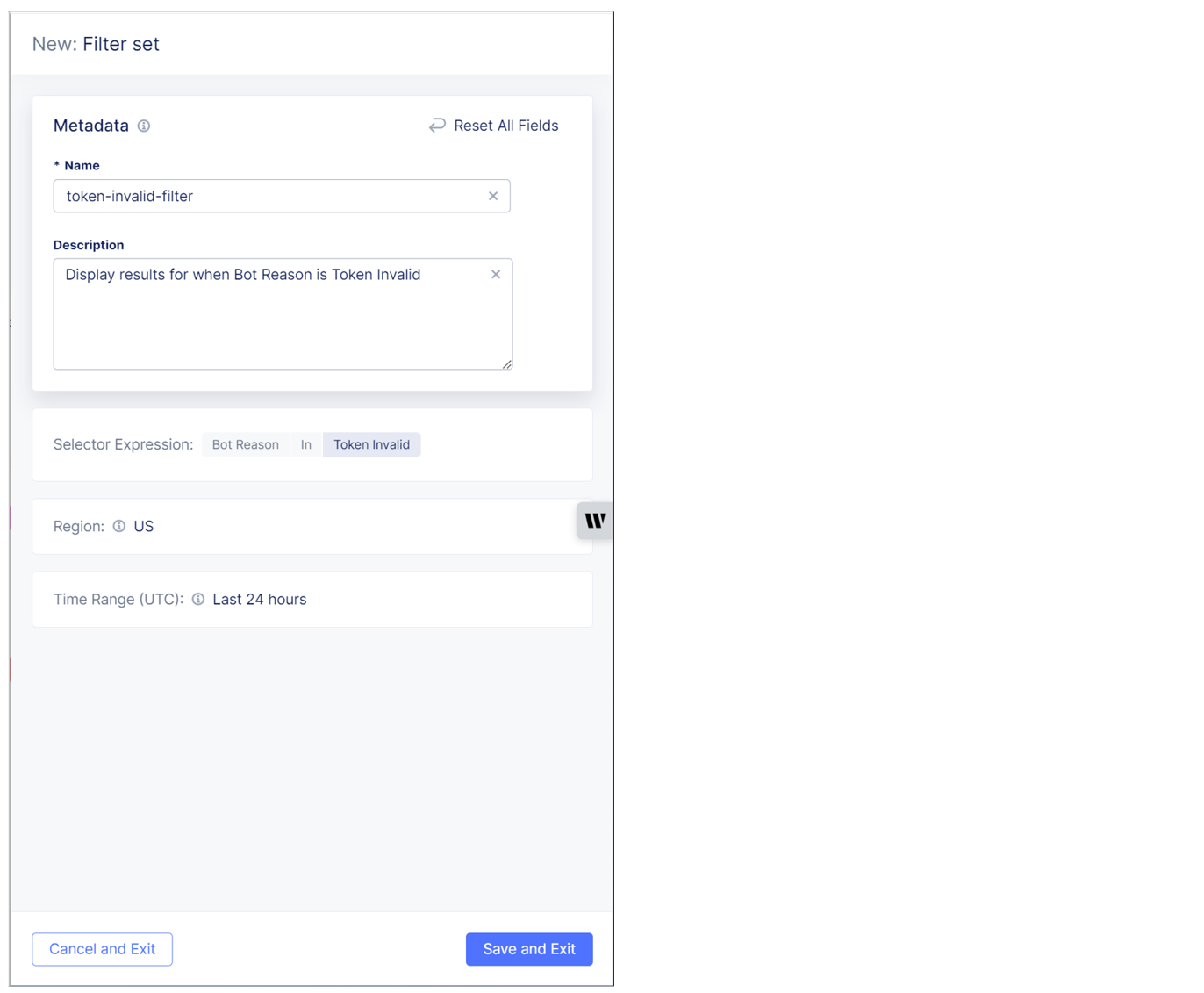
-
Enter a Name and Description for the filter and then select Save Filter.

Figure: Name and Description fields
The newly saved filter is available from the Saved Filters list to view and share with other administrators.

Figure: Saved filters
View Saved Filters
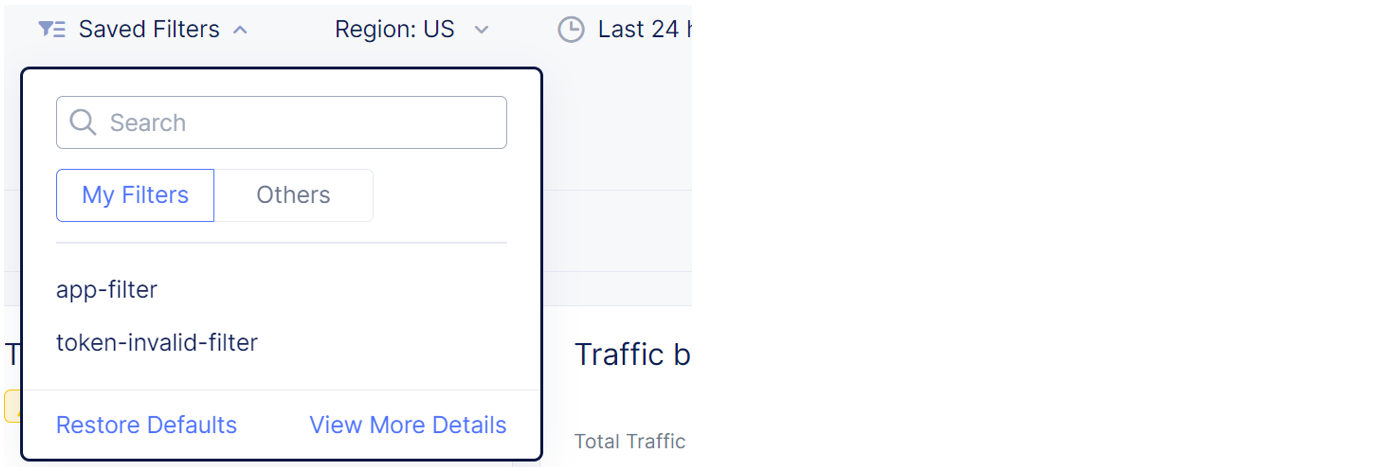
To view a previously saved filter, select Saved Filters and then select a filter from the list.
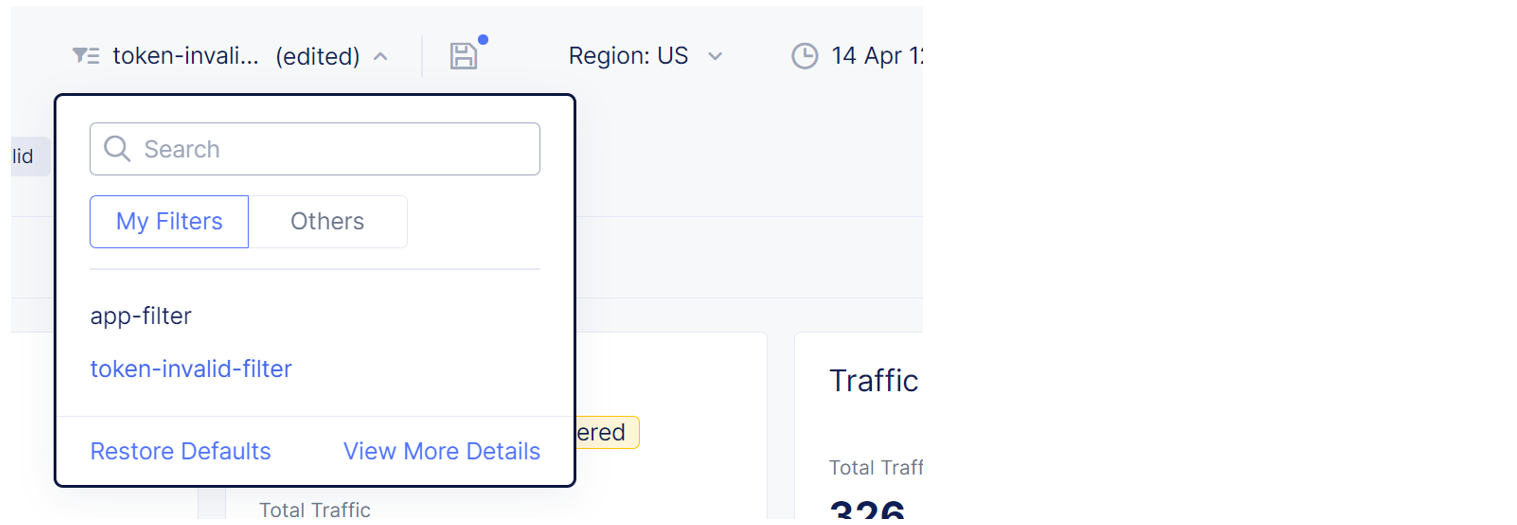
Figure: View saved filters
Note: Filters with custom date ranges older than 30 days expire and cannot be used.
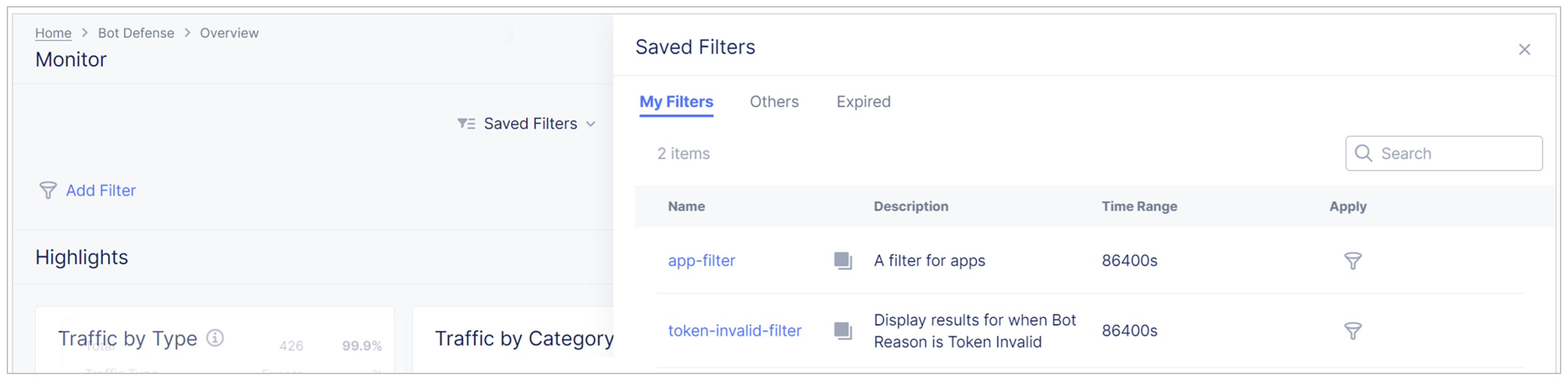
You can also view filters saved by other users.
-
On the dashboard or report that you want to view, select Saved Filters.
-
Select View More Details.
-
Select Others and then select a filter from the list to view the filter.

Figure: View other users' filters
Share a Saved Filter
- From the Bot Defense navigation panel, select Manage > Saved Filters.
- From the Saved Filters list, select the name of the filter you want to share.
- Select Copy URL and provide the URL another administrator to enable them to view your filter.