Distributed Cloud Mesh
What is Distributed Cloud Mesh?
F5® Distributed Cloud Mesh is used to connect, secure, control and observe applications deployed within a single cloud location or applications distributed across multiple clouds and edge sites. Its unique proxy-based and zero-trust architecture significantly improves security as it provides application access without providing any network connectivity across clusters and sites. In addition, using our global network backbone, we are able to deliver deterministic, reliable, and secure connectivity across multi-cloud, edge, and to/from the Internet.

Figure: Highlevel View of Mesh Deployment
The SaaS-based service also reduces the complexity of managing and operating Mesh services deployed within a single cloud, across multiple cloud sites, or edge sites as customers don’t have to worry about doing lifecycle management of data, control and management plane. Since the policy and configuration are centralized, any change is reflected across the entire deployment. All logging and metrics are also centrally available for observability with API-based integrations to external tools like Datadog or Splunk from our centralized SaaS portal.
There are three modes of consuming Mesh services:
-
Customer Sites (cloud or edge) - deploy F5 Distributed Cloud Nodes that act as distributed data-plane nodes where you can selectively enable any or all Mesh services. These nodes are centrally managed through F5® Distributed Cloud Console for tasks like software lifecycle management (upgrades, patches, decommission...), service configuration, policy management, and observability.
-
F5 Distributed Cloud Global Infrastructure - the Mesh connectivity and security services can be enabled within our global network without affecting your cloud or edge site. In this case, the global infrastructure can be configured to act as a TCP, HTTP proxy, or API proxy with associated security services. In some scenarios, the customer can also use the backbone as a private IP network and connect their data centers or cloud locations.
-
Hybrid Deployment (customer site and global infrastructure) - deploy F5 Distributed Cloud Nodes within your cloud or edge site to automatically, securely, and redundantly connect directly to our global network at the nearest points of presence. This now provides you with a capability of a globally distributed service mesh by selectively enabling any or all Mesh services across all your sites and across our global network.
Mesh is designed to make it extremely easy for anyone to consume network and security service in the cloud, network, or edge without worrying about run-time and operations of a modern and hybrid environment.
Why use Mesh?
There are three reasons why we believe that you should consider using Mesh for your next deployment:
-
Service Mesh architecture for any application - Even though the term service mesh is often used in the context of microservices, there is no inherent reason why it cannot include monolithic application architectures also. Service mesh is a modern network concept that elevates the control and observability to the application layer and is a more suitable approach to networking as we move from static data-centers to dynamic multi-cloud and edge infrastructure. As a result, we believe that any application framework should be able to benefit from service mesh architecture as it delivers much richer functionality like include service discovery, load balancing, failure recovery, A/B and canary, end-to-end authentication, authorization, detailed metrics, and monitoring.
-
Simpler operations model - Since IT and DevOps teams have to support large hybrid applications (modern and monolithic) and multi-cloud deployments, it is becoming very challenging for them to integrate and operate multiple services and appliances for configuration, alerting, monitoring, and change management. They would rather prefer to use a modern connectivity and security solution with centralized management, distributed control plane that can scale with the number of deployments, and an integrated L3-L7 data-path. Mesh delivers all of this functionality for hybrid applications in any environment, enabling applications to securely connect with other internal applications, partner applications, SaaS applications, or be securely accessible from the public internet.
-
Global and high-performance network - Since no application is an island, it typically requires connectivity to other applications or access from users. Connecting application clusters across multiple cloud providers typically require traversing unreliable public internet or complexity of procuring and operating backbone networks. If there is a requirement to connect applications at the edge sites, it further complicates the situation with an additional layer of VPNs or SD-WAN. Also, if any of these applications need to be accessible from the public internet, there is even more complexity of providing high-quality access, DDoS and application-level attack protection, API acceleration, etc. The global backbone and its unique service mesh features that are distributed across customer sites and the global backbone solves all these problems for any environment.
Key Mesh Services
Mesh delivers a complete range of networking and security services that are typically required to connect and secure applications. Any combination of these services can be centrally deployed and operated using the Console and be seamlessly enabled across our global infrastructure or inside your cloud or edge site using F5 Distributed Cloud Nodes.
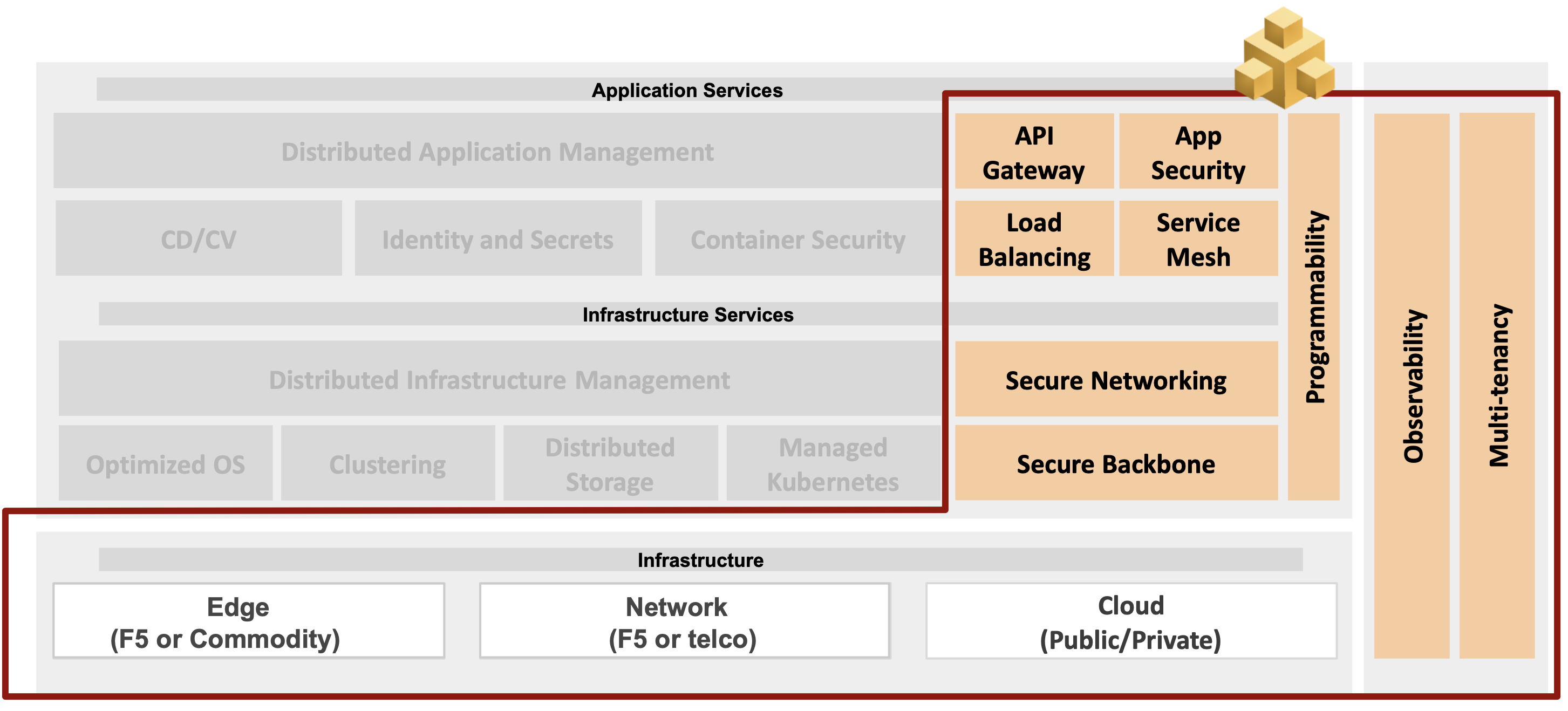
Figure: Mesh Services
-
Secure Backbone - The points of presence (PoPs) are interconnected using a multi-terabit capacity dedicated and redundant private backbone for maximum performance. These PoPs are densely peered and also connected with multiple transit provider connections to achieve very high-quality internet access to the applications and for consumers to the applications. We also directly connect to multiple cloud providers from these locations to provide a reliable and predictable experience across cloud providers. Using BGP and advanced traffic engineering, we are able to provide granular SLAs for any customer that wants high performance global private network without the complexity of procuring and operating a global network. In addition to connectivity service, the customer can selectively enable infrastructure protection features like DDoS, L3 firewall, and anomaly detection to completely offload their DMZ appliances from their cloud to our network using private network hand-off or securely tunneled using node in their site.
-
Secure Networking - Using an industry-proven network stack with most advanced BGP implementation, we are able to provide full-mesh or hub-and-spoke connectivity across cloud or edge sites. The nodes automatically create secure IPsec/SSL tunnels with each other if they have direct IP reachability or securely connect to multiple nearest global PoPs. Using application or policy-based routing, traffic can be load balanced for optimal performance across this network. In addition, you can enable a network firewall and forward proxy capabilities to control and filter traffic to and from the applications.
-
Load Balancing and Service Mesh - Service discovery, health checking, distributed proxy, application micro-segmentation, and application policy provides the most advanced implementation of edge load-balancer with ingress/egress capability for any service mesh. Service discovery integrates with multiple registries like Kubernetes, Consul, or DNS along with health checking support for HTTP, TCP, custom, and so on. End-point health is distributed to all the sites where the virtual service is exposed using our extensions to the BGP protocol and this provides us with valuable insight on how to globally distribute the load balancing function. Support for both TLS and mutual-TLS for authentication with policy-based authorization on the proxy provides the capability to enforce end to end security of application traffic. In addition, the proxy gives the ability to terminate user traffic in the global network and use a persistent connection to serving end-points to accelerate and load balance to most optimal end-point.
-
API Proxy - High performance, extensible, and distributed functionality allows the handling of a large number of transactions per second. The solution provides the capability for authentication using client certificates and the ability to route and load-balance based on APIs along with the traffic control capabilities like canary, rate-limiting, fault-injection, etc.
-
App Security - Integrated application security and AI inference engine in the data-plane provides the capability to perform intrusion and anomaly detection based on models that are computed and distributed from our centralized SaaS-based service. The solution uses a combination of algorithmic, signature-based, reputation database, and machine learning techniques to identify application and API level attacks and provide a holistic next-generation application firewall. The machine learning engine automatically determines all the API endpoints that are being accessed for any virtual service and that can be used to define policies for application micro-segmentation. F5 Distributed Cloud Services also provides the capability of managed PKI identities to applications that can be used for application to application and developer to application authentication and policy-based authorization.
-
Observability - Very detailed metrics, logs, requests, notifications are centrally collected from every node in the system to provide rich observability across network, application, and security stack. These metrics are used to provide a complete view into service connectivity, what APIs and applications are being accessed in the system, what is the probability distribution function of an API access, as well as the ability to easily debug and trace issues. Our centralized SaaS-based service can also be used to integrate logs and metrics with external performance management systems, like Datadog, Splunk, and more.
-
Multi-tenancy - the entire system was built from the ground-up for multi-tenancy with complete isolation of the network across tenants. The global infrastructure is high performance and able to serve a very large number of tenants and users because it does not need to instantiate a separate software instance for every tenant while guaranteeing isolation of traffic using VRFs - a technique that has been employed in telecom networks for over two decades but rarely used in a proxy or load-balancer data path.
Each of these features can be used individually as needed by the customer, or they can be used in combination to provide a full connectivity and security solution for distributed applications.
Example Use Cases for Mesh
Mesh has been built in such a way that it can be deployed in different ways to solve many use-cases:
-
App & Network Services Consolidation in one or more clusters within public or private cloud. Use the SaaS to deploy the nodes within your site and use Console to enable Mesh features for a fully consolidated network, application connectivity, and security solution. This brings all the modern network and security capabilities to legacy and modern applications.
-
Secure Kubernetes Gateway in a single cluster within public cloud, private cloud, or edge site. Use the SaaS to deploy the node in any site to act as ingress as well as egress gateway for your Kubernetes cluster to deliver enterprise-grade security. All inbound and outbound traffic can be enabled with rich security services offered by the Mesh. In addition, using our global backbone with comprehensive security and reliability services, this cluster can now be used to serve traffic from the public internet.
-
Multi-cluster Secure Mesh to deliver service mesh capability across multiple clusters deployed across cloud regions and/or cloud providers. Use the SaaS to deploy the nodes within each site, and they will automatically and redundantly connect to our global backbone. Mesh will create a service mesh across each of these clusters and provide the capability of cross-cluster routing, VPNs, service discovery, health checks, API routing, application security, unified policy, and observability.
-
Application Security and reliability from the public Internet - applications that are exposed and accessible from the public internet require many network and security services, like anycast, global load balancing, and DDoS protection to ensure that they are reliable for the consumers and secure against attacks. Mesh can be used to deliver all of these services by simply exposing your origin server across our global network.
-
Application Acceleration - for applications that are accessible over the public internet, it is highly desirable to improve performance by using techniques like edge TLS termination as well as API processing closer to the client while keeping a persistent TLS connection to the origin servers. By using the SaaS to deploy the nodes in your public or private cloud sites that host your origin servers and using our unique distributed gateway capabilities of Mesh, you can terminate client connections in our global network and deliver APIs from the most optimal origin server (rather than the most optimal load-balancer).
-
Secure Cloud Network with DMZ provides a global private network for the customer across multi-cloud and edge with DMZ-as-a-service. As the complexity and performance requirements of enterprise network increases with the adoption of multi-cloud and edge, it is desirable to create a global high-performance network across these sites. It is also desirable to move the DMZ from a few central points (that act as choke points) to be distributed within this global network. Mesh allows customers to create a global private network using a combination of techniques - private network hand-off or the nodes to tunnel from their sites into this network. All the application connectivity and security services can then be selectively enabled on this network to have a distributed DMZ-as-a-service.
-
Secure Edge Gateway - to deliver network and security services across multiple edge sites. Deploy the node within each site, and they will automatically and redundantly connect to our global backbone using IPsec or SSL VPN. In addition, Mesh services -- routing, network security, network security, service discovery, health checks, API routing, application security, unified policy, and observability -- can be enabled across all of these sites and managed as a fleet.