Configure Rate Limiting per User
Objective
This guide provides instructions on how to configure rate limiting per user based on the user identification in the F5® Distributed Cloud Console. This limits the number of API requests from user per a time period set by configuration. The rate limiting per user is applied on the Distributed Cloud virtual host. For more information, see Rate Limiting Based on User Identification.
Using the instructions provided in this guide, you can configure a set of user identification rules, create rate limiters, and apply them to a HTTP load balancer or virtual host.
Prerequisites
The following prerequisites apply:
-
An F5 Distributed Cloud Account. If you do not have an account, see Getting Started with Console.
-
F5 Distributed Cloud Services virtual host providing front end for your application.
- Note: See Create and Advertise a Virtual Host for instructions on configuring virtual host.
Configuration
Enabling rate limiting for your virtual host or load balancer requires you to create rate limiting with optional user identification rules and applying to the virtual host or load balancer. The following image illustrates the sequence of enabling rate user identification:
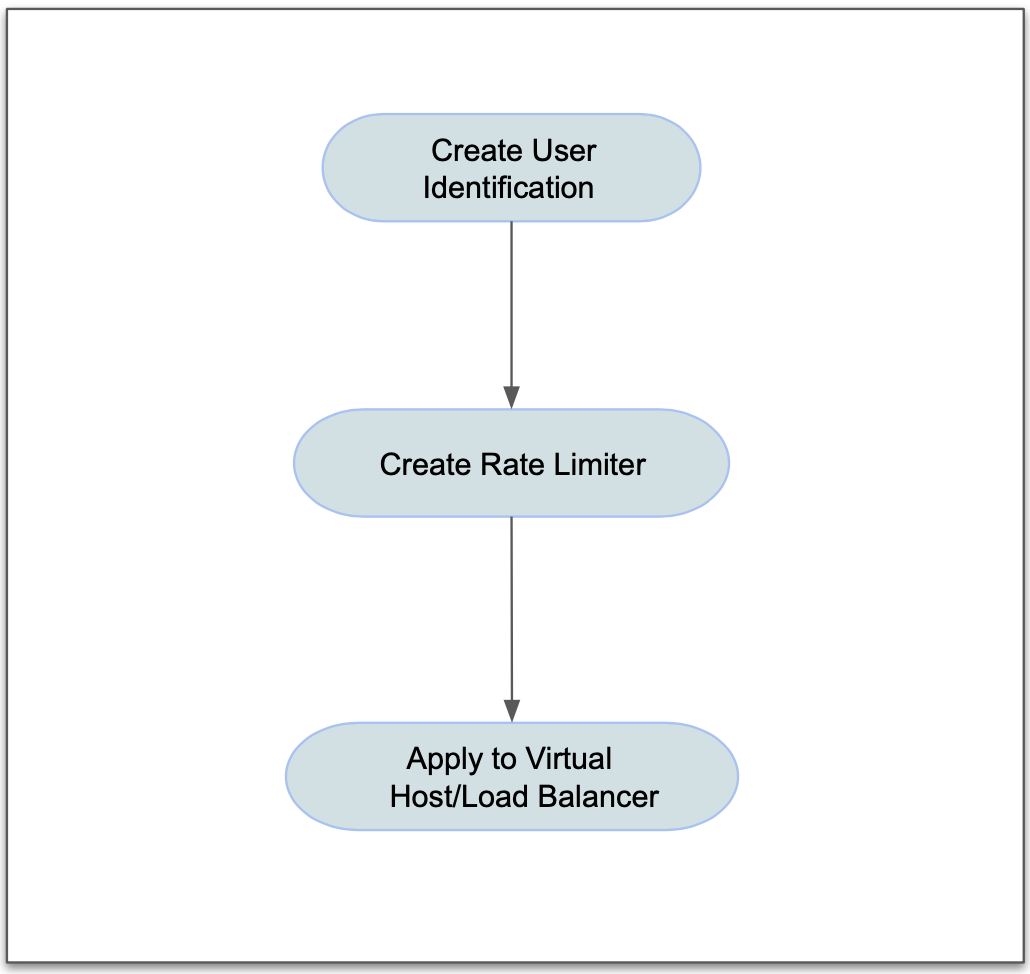
Figure:Sequence For Rate Limiting Based on User Identification
Configuration Sequence
Enabling rate limiting based on user identification can be performed in the following two ways:
- Using the HTTP load balancer wizard.
- Using the individual wizards for the user identification, rate limiter, and virtual host.
Enabling rate limiting based on user identification requires you to perform the following sequence of actions.
| Phase | Description |
|---|---|
| Create User Identification | Create user identification with rules defining what are evaluated for identification. |
| Create Rate Limiter | Create rate limiter and optionally apply user identifier. |
| Apply Rate Limiter to Virtual Host | Create a Fast ACL set with the created Fast ACL. |
Note: When using the HTTP load balancer wizard, creation of user identification and rate limiter are part of the wizard itself.
Enable Rate Limit
Step 1: Navigate to the HTTP Load Balancers page.
- Select the
Multi-Cloud App Connectservice. - Select the desired namespace from the
Namespacedrop-down menu. - Navigate to
Manage->Load Balancers->HTTP Load Balancers.
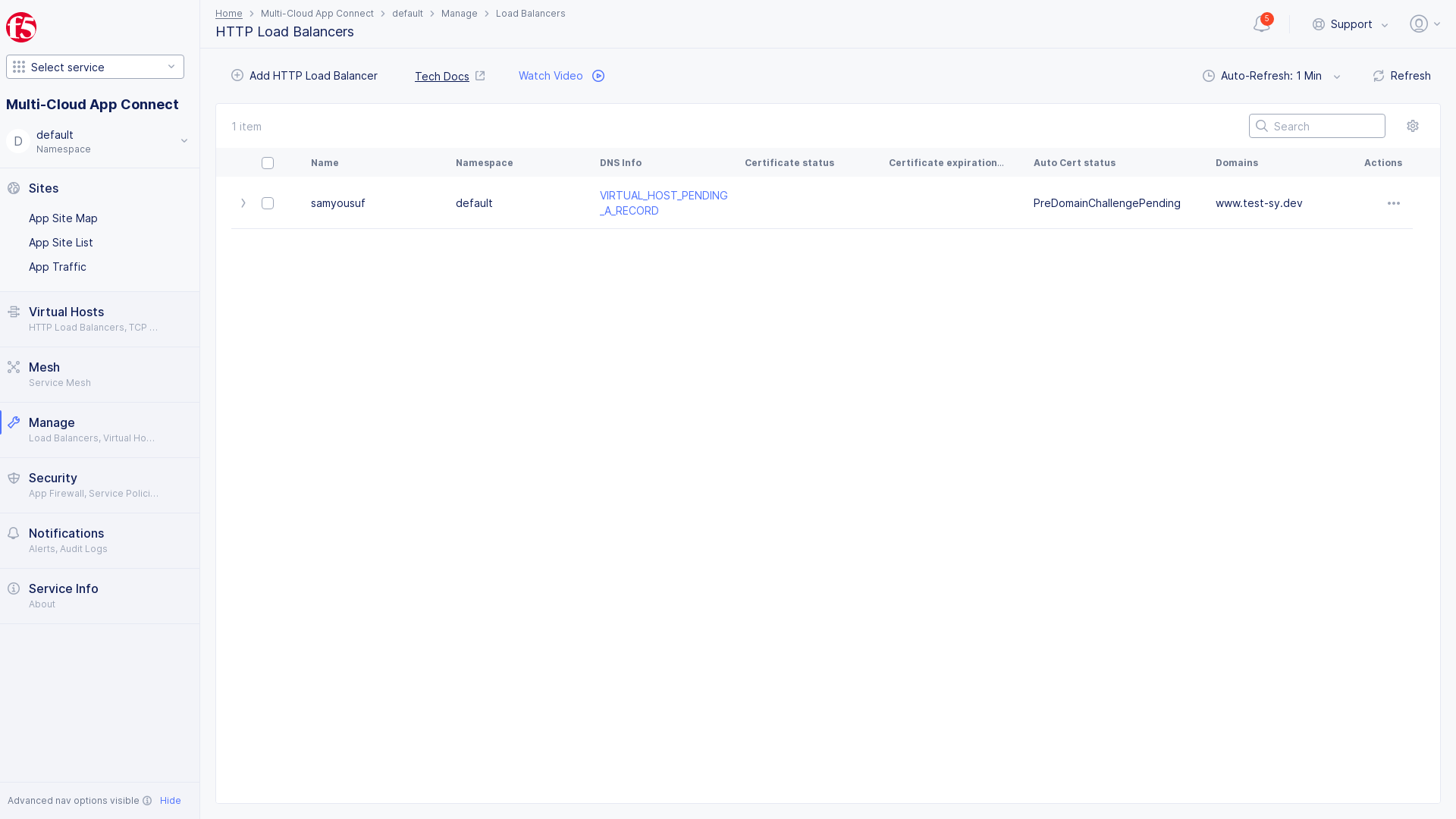
Figure: Load Balancers
Step 2: Start creating a user identifier for rate limiting.
- Select
...->Manage Configurationand then selectEdit Configurationin the upper right corner to open to your load balancer's configuration edit form. - Scroll down to the
Common Security Controlssection. - In the
User Identifierfield, selectUser Identification Policy. - In the
User Identification Policyfield, select an existing user policy or selectAdd Itemto create a new one.
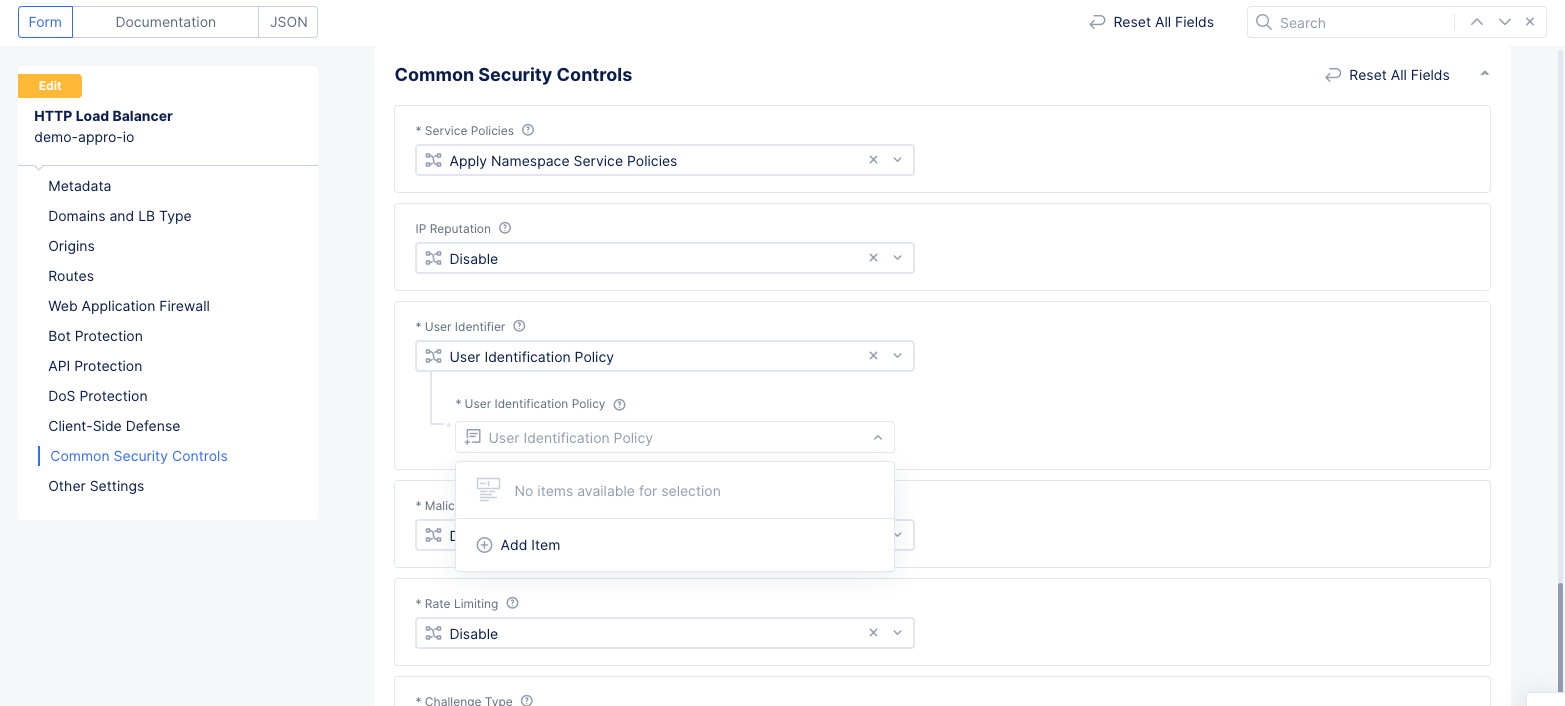
Figure: HTTP Load Balancer Security Configuration
This example shows creating new user identification rule.
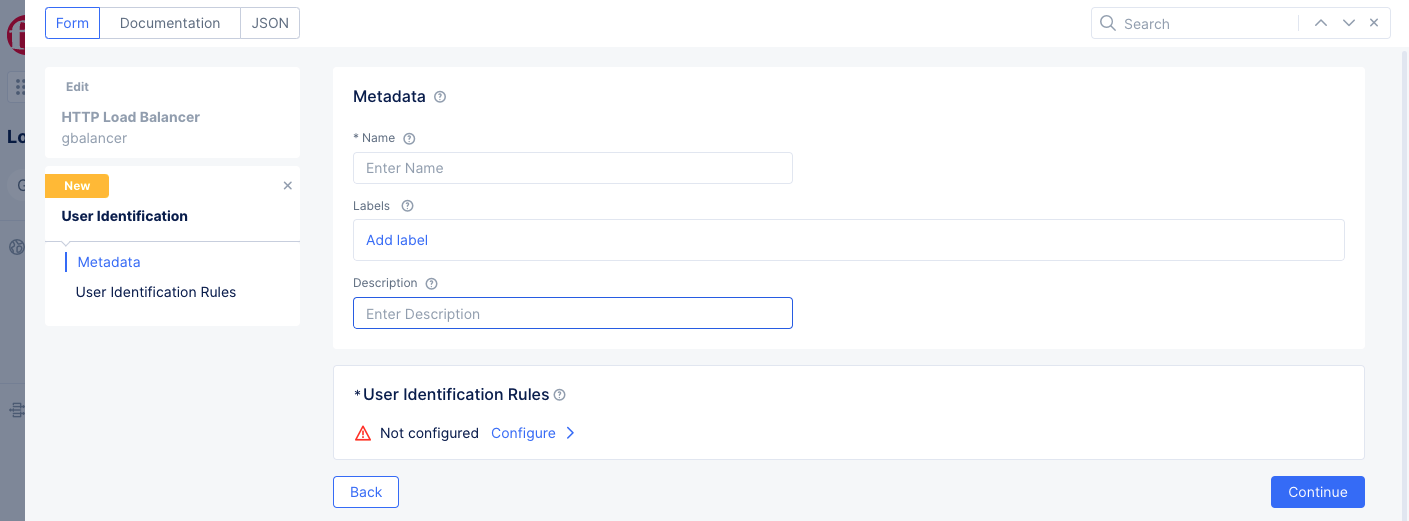
Figure: Create User Identification
- Enter a name for the user identification policy in the
Metadatasection. - In the
User Identification Rulessection, selectConfigureto build a list of user identification rules. - Select
Add Itemto create a rule.
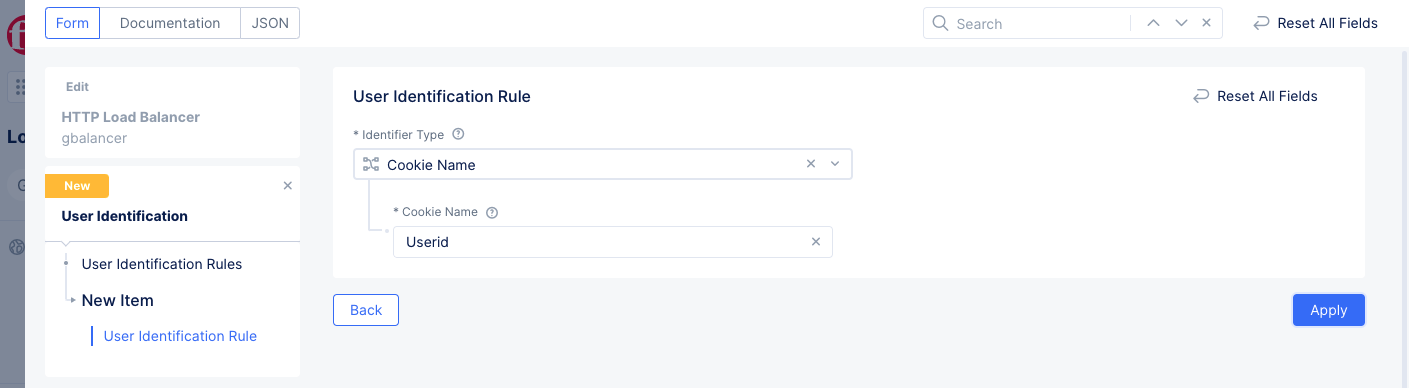
Figure: Create User Identification Rule
- Select an identifier type from the drop-down list in the
Identifier Typefield and enter a value for that identifier in the field enabled as appropriate for your identifier type selection. For example, selectCookie Nameas the identifier type and setUseridas the identifier. - Select
Applyto add the new rule to your rules list.
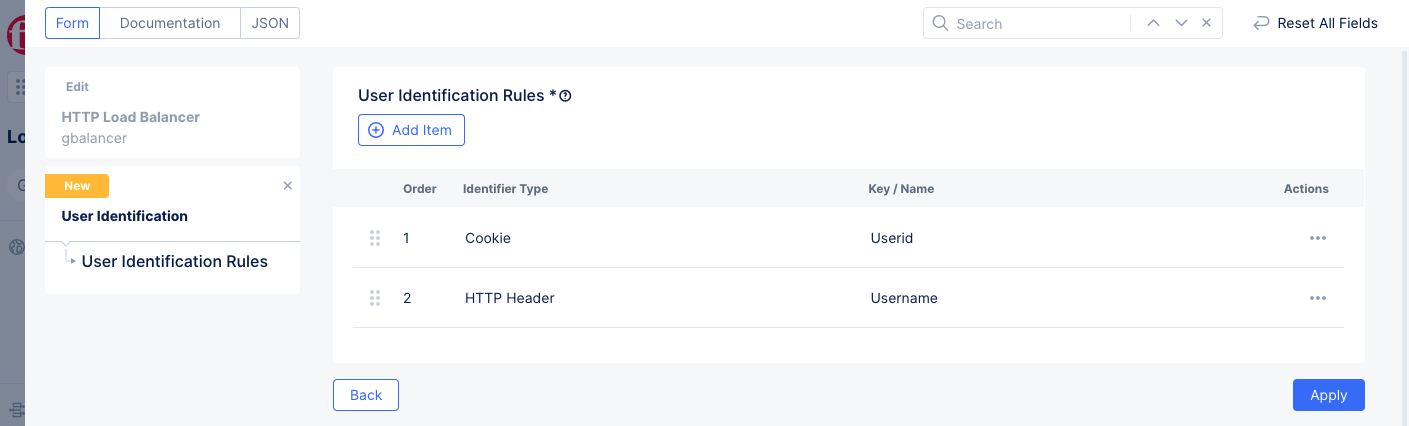
Figure: User Identification Rule List
- Optionally select
Add Itemto add more rules to your list. - Select
Applyto complete your list. - Select
Continueto save your rule list into your load balancer configuration.
Step 3: Enable rate limiting and set the limiter values.
-
Scroll down to the
Rate Limitingfield (a little below theUser Identifiersection) and selectCustom Rate Limiting Parameters. -
Select
View Configuration. -
Enter the maximum number of requests per unit in the
Numberfield. -
Enter a unit of time in the
Per Periodfield. Supported units areSeconds,Minutes, andHours. -
Enter the number of periods to apply the rate. As an example, If you enter [1,
Seconds, 60] or [1,Minutes, 1] for [Number of Requests, Per Period, Periods] both would be the same as 1 request per minute. -
Optionally enter a value for the
Burst Multiplierfield, which indicates how many times a user can hit the requests/unit limit.
The following example sets 15 requests per second as the rate limit. A user who exceeds that would be blocked until the rate drops below the limit.
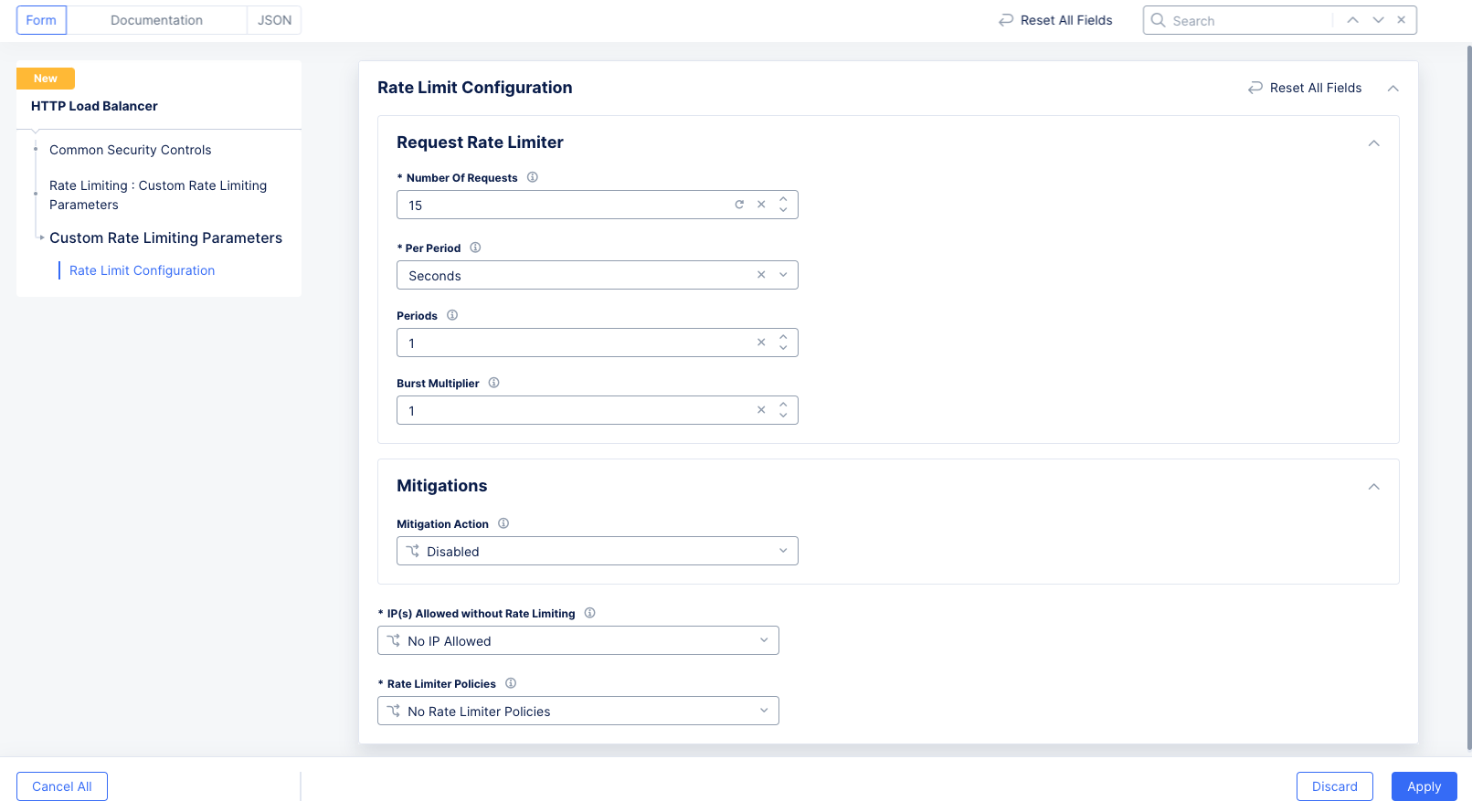
Figure: Rate Limit Example for Load Balancer
Step 4: Optionally create a mitigation.
Select Block from the Mitigation Action drop-down menu if you want a user to be blocked for all requests for some time after exceeding the rate limit.
- Select a duration unit (
Seconds,Minutes, andHours). - Enter a duration value.
Note: The maximum blocking time is 48 hours.
The following example would block all requests from a user who exceeded the rate limit for 5 minutes regardless of how the request rate changes during the 5 minute mitigation period.
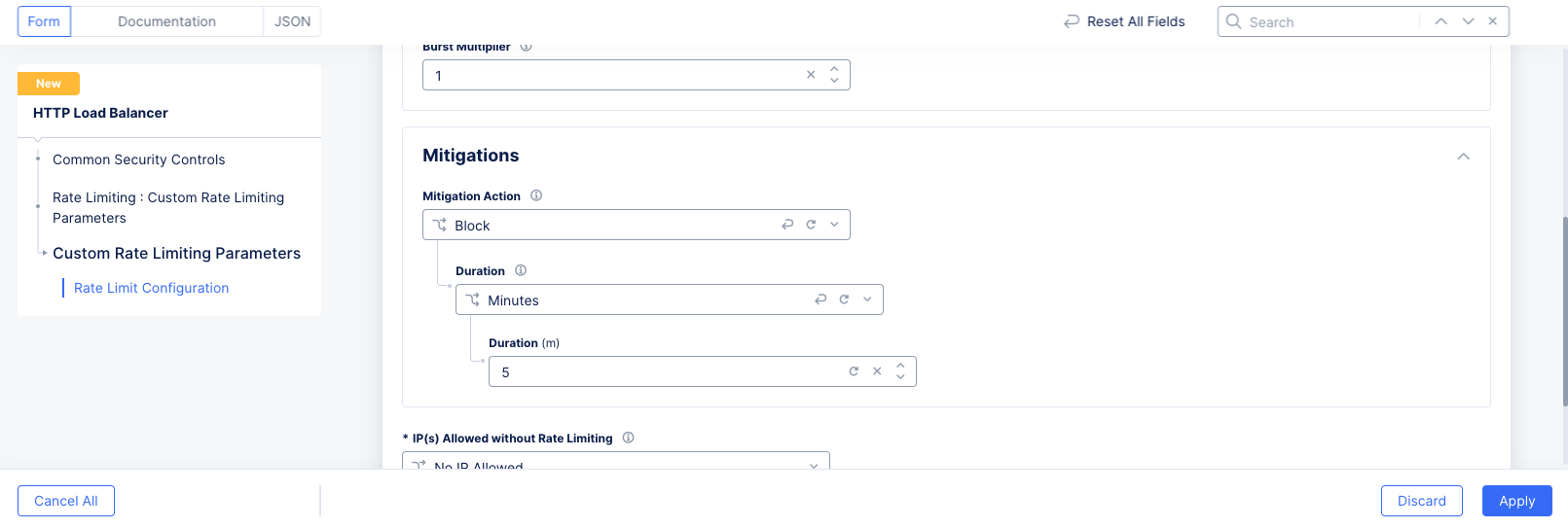
Figure: Rate Limit Mitigation Example for Load Balancer
Step 5: Specify IP prefixes for exempting from the rate limiting.
By default, rate limiting applies to all IPs. Optionally, select Ip Allowed List or Ip Allowed using Ip Prefix Set(s) for the Ip(s) Allowed without Rate Limiting drop-down field and perform one of the following:
-
Add IP prefixes if you selected
Ip Allowed List. UseAdd itemto add more prefixes. -
If you selected
Ip Allowed using Ip Prefix Set(s), select an existing IP prefix set. If no IP prefix sets are listed, selectAdd Itemin the drop-down list to create a new prefix set.
This example adds the IP prefixes using the Ip Allowed List option.
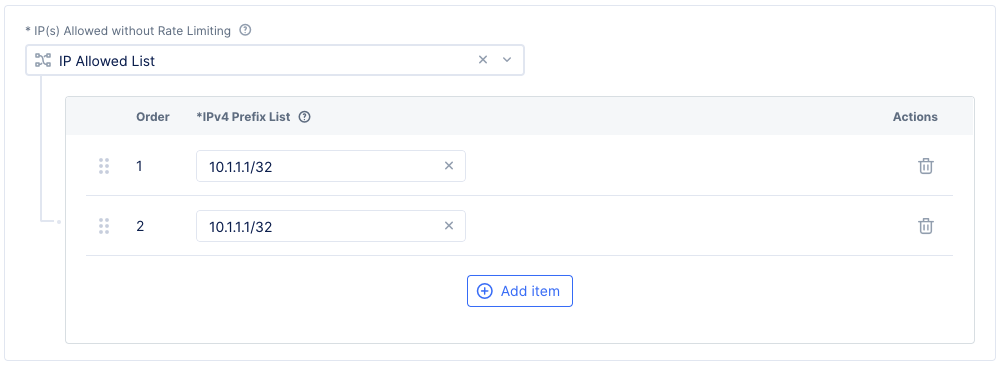
Figure: Rate Limiter Configuration
Note: Performing this step enables the system to exempt rate limiting for requests from specified IP prefixes.
Step 6: Specify rate limiter policies.
By default, there are no rate limiting policies (An IP Allowed List is an implicit policy, if specified). Optionally, select Rate Limiter Policies to create an ordered list of policies. (If an IP Allowed List was specified in the previous step, it is effectively the first ordered policy).
- Select an existing policy from the drop-down list or choose
Add Itemfrom that list.
For a new policy, continue with the rest of the actions in this step.
- Enter the policy name and optionally labels and a description.
- Select
Configurein theRulessection to view theRuleslist. - Select
Add Itemto add a rule. - Enter a name for the rule
- Select
Configurein theRule Specificationfield.
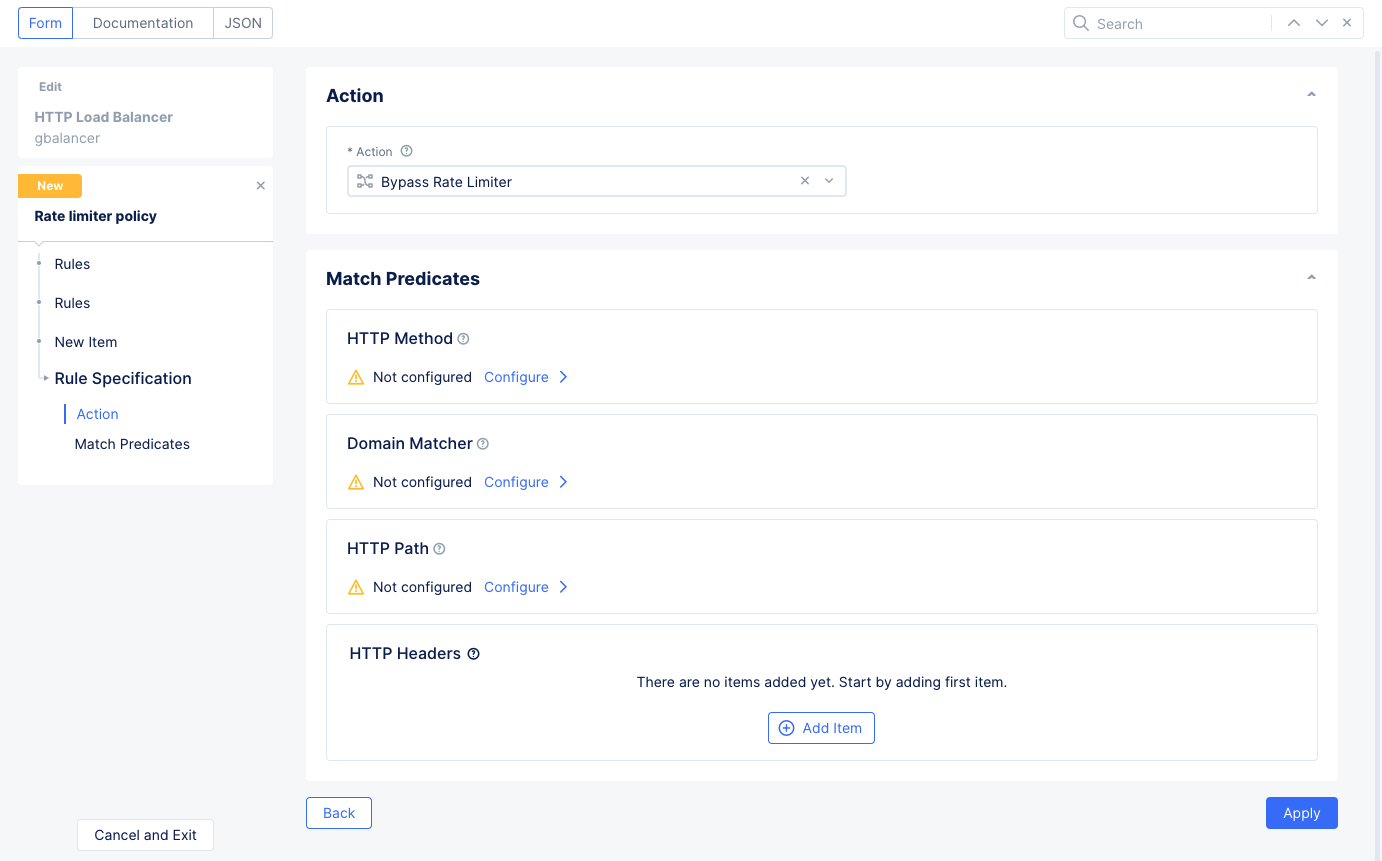
Figure: Rate Limiter Rule Specification
-
Choose an
Actionto take for this rule if the request matches the predicates specified below:Bypass Rate Limiter: Exclude this request from the HTTP rate limiter.Apply Rate Limiter: The HTTP rate limiter applies to this request.Apply Custom Rate Limiter: Apply a custom rate limiter to this request, which you will select or create as part of this option.
-
Configure one or more
Match Predicates:HTTP Method: Matches against the HTTP method(s) you specify (e.g., GET, PUT, and HEAD).Domain Matcher: Matches against the domain(s) you specify, either by exact match or by regex.HTTP Path: Matches against the path portion of the request, either by prefix value, exact value, or regex value.HTTP Headers: Matches against a list of header names that are either present, not present, or contain specified values.
-
Select
Applyto save the rate limiter rule specification. -
Select
Applyto save the rate limiter rule. -
Select
Applyto save the rate limiter rules list. -
Select
Continueto save the rate limiter policy.
Step 7: Complete enabling the rate limiting for the load balancer.
- Select
Applyto create and add the rate limiter to the load balancer. This also returns to the load balancer configuration page. - Select
Save and Exitto create or update the load balancer and enable the rate limiting.
Note: The following apply:
- The rate limit is always evaluated before any configured network security policy sets.
- Evaluation of the configured network policy set is done only if the request is under limit set by the rate limit.
- A service policy rule is automatically created for each HTTP load balancer that has rate limiting enabled and a rate limiter object is also automatically created.
- An IP Prefix set is automatically created if the rate limiting configuration has an allowed IP list.
- Policy rule uses virtual host and IP matcher as match predicates.
- The rate limiter is applied as an action in the service policy rule.
Enable Rate Limit Using Constituent Component Wizards
The constituent components of rate limiting functionality are user identification, rate limiter, and virtual host/load balancer. Perform the instructions provided in the following chapters to configure the constituent components.
Create User Identification
A user identification specifies the list of rules defining the identifier types and their values. The system determines the user identity based on these rules and uses the rate limiter to limit the requests accordingly.
Note: Configure user identifier is optional as the system treats client IP address as the default user identifier.
Step 1: Log into the F5 Distributed Cloud Console and navigate to user identity creation.
- Select the
Multi-Cloud App Connectservice. - Select the desired namespace from the
Namespacedrop-down menu. - Navigate to
Security->Shared Objects->User Identification.
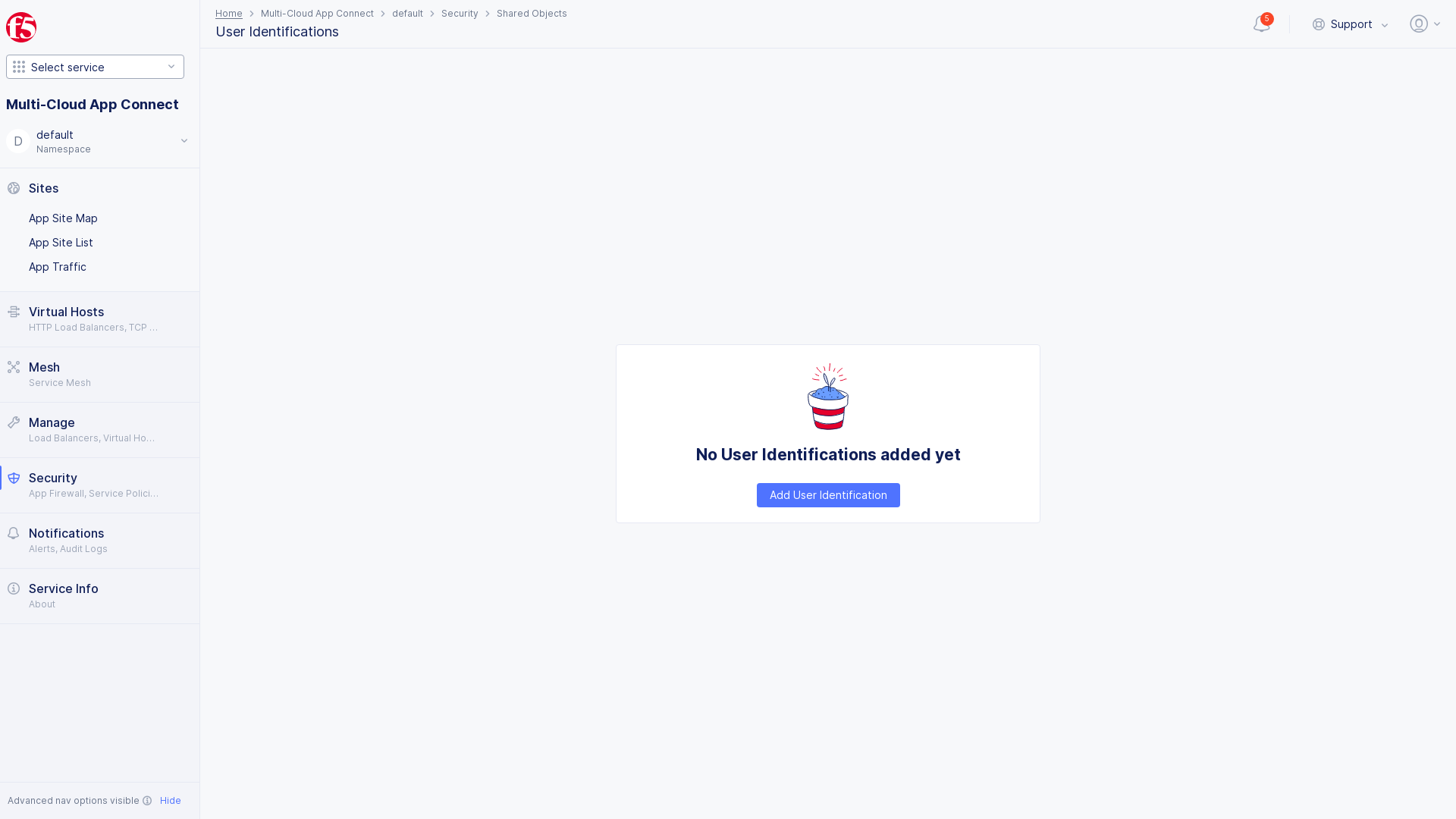
Figure: Navigate to User Identification Creation
Step 2: Configure identification rules
- Select
Add User Identification. The user identification creation form opens. - Enter a name for this user identification and optionally labels and a description.
- In the
User Identification Rulessection, selectConfigureto create a rules list. - Select
Add Itemto create the first rule in the list. - Select an option from the drop-down list for the
Identifier Typefield and enter an associated value for the selected option, if required. - Select
Applyto save the rule to the rules list. - Use the
Add Itembutton to add more rules, if necessary. - When finished adding rules, select
Applyto save the rule list.
This example shows adding cookie name and HTTP header name as identifiers.
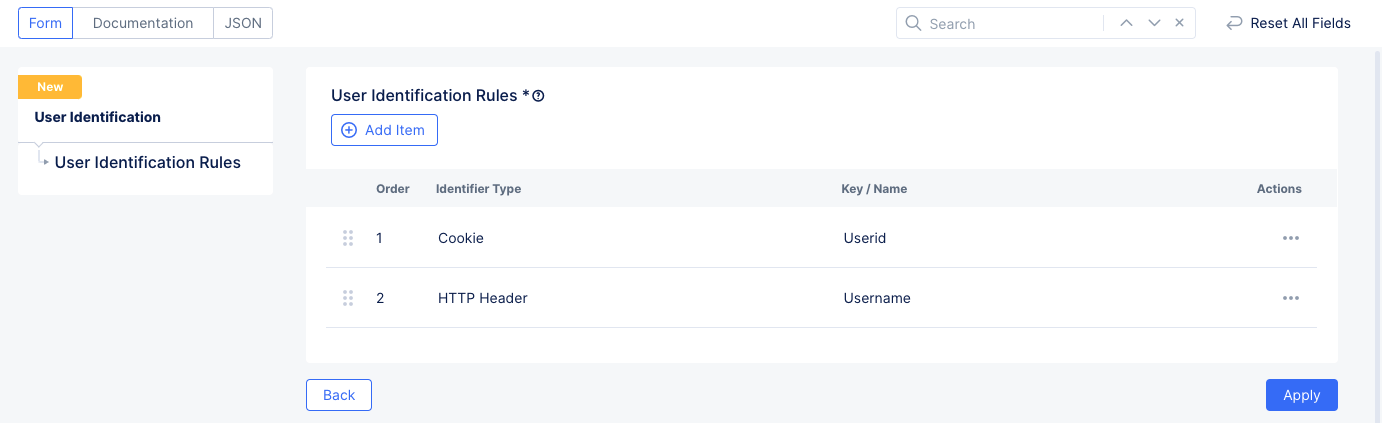
Figure: User Identification Rules
Step 3: Complete creating user identification
Select Save and Exit to create the user identification object.
Create Rate Limiter
A rate limiter specifies the limit for an API request per second or minute and optionally specifies the user identification rules to determine to which API request this limit is applied.
Perform the following to create rate limiter:
Step 1: Log into the Console and navigate to rate limiters section.
- Select the
Shared Configurationservice. - Select the desired namespace from the
Namespacedrop-down menu. - Navigate to
Security->Shared Objects->Rate Limiters. - Select
Add Rate Limiter. The rate limiter creation form opens.
Step 2: Set rate limit configuration.
-
Enter a name and optionally set labels and add a description.
-
Select
View Configurationin theRate Limit Valuessection. -
Enter the maximum number of requests per unit in the
Numberfield. The maximum allowed number is 8192. -
Enter a unit of time in the
Per Periodfield. Supported units areSeconds,Minutes, andHours. -
Enter the number of periods to apply the rate. As an example, If you enter [1,
Seconds, 60] or [1,Minutes, 1] for [Number of Requests, Per Period, Periods] both would be the same as 1 request per minute. -
Enter a multiplier value in the
Burst Multiplierfield. The burst multiplier is the maximum burst of requests allowed, expressed as a multiple of the rate. -
Optionally select
Blockfrom theMitigation Actiondrop-down menu if you want a user to be blocked for all requests for some time after exceeding the rate limit.- Select a duration unit (
Seconds,Minutes, andHours). - Enter a duration value.
- Select a duration unit (
-
Select
Applyto save the rate limits.
The following example sets 5 requests per 2 seconds as the rate limit. A user that exceeds that limit will be blocked for 30 seconds regardless of how the request rate changes during the 30 second mitigation period.
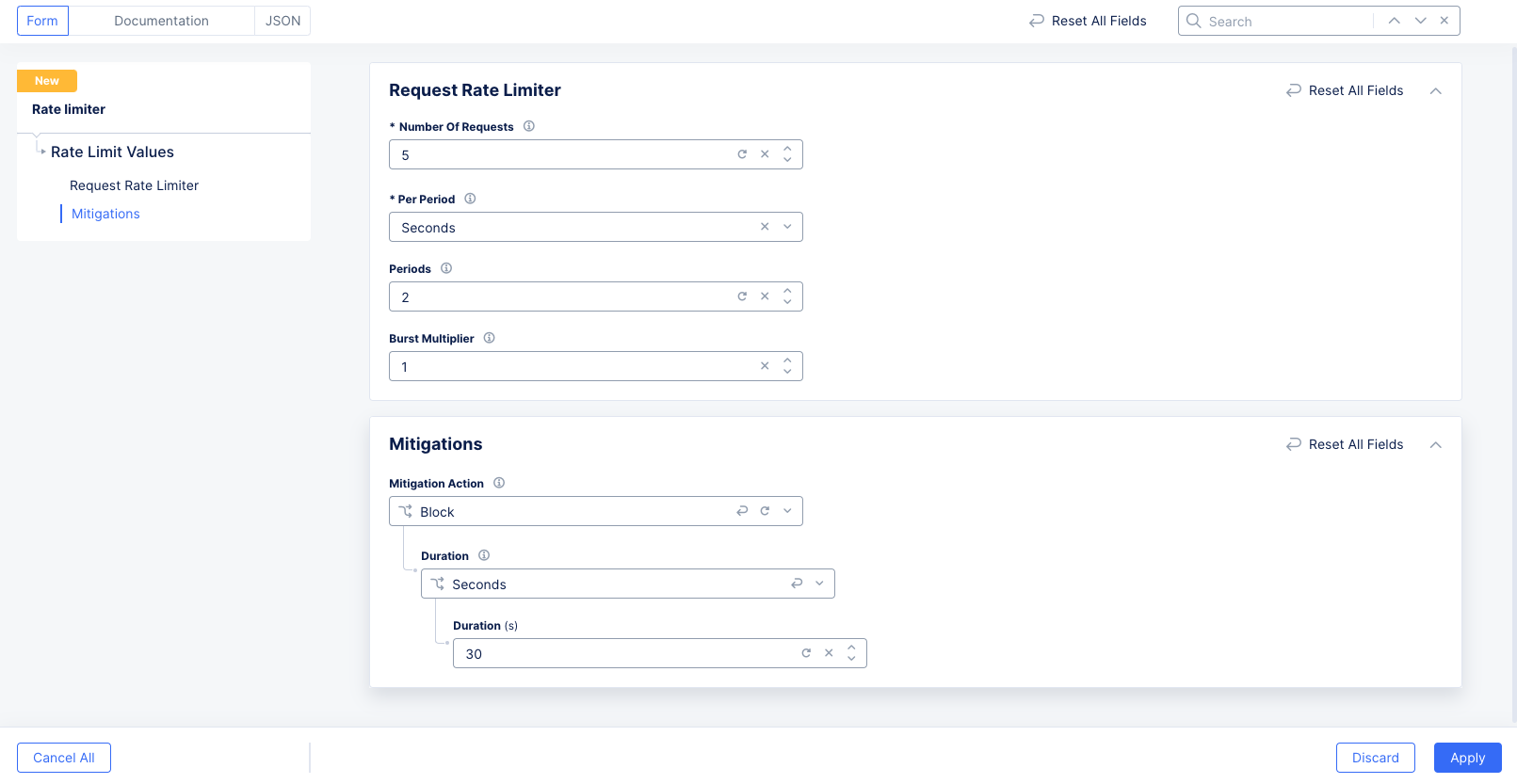
Figure: Rate Limits
- Select
Select user identificationin theUser Identification Policysection and select a user identification.
Step 3: Complete rate limiter creation.
Select Add Rate Limiter to create the rate limiter object.
Add Rate Limiter to Virtual Host
This example shows how to apply rate limiting to a virtual host that is already created. However, you can also apply the rate limiting while creating a virtual host.
Note: For virtual host setup instructions, see Create and Advertise a Virtual Host.
Perform the following to apply a rate limiter to a virtual host:
Step 1: Navigate to virtual host configuration section.
- Select the
Multi-Cloud App Connectservice. - Select the desired namespace from the
Namespacedrop-down menu. - Navigate to
Virtual Host->HTP Load Balancers. - Select
...->Manage Configurationand then selectEdit Configurationin the upper right corner to open the virtual host configuration edit form.
Step 2: Apply rate limiters to the virtual host.
-
Scroll down to the
Rate Limitingsection in theCommon Security Controlssection. -
Using the
Rate Limitingfield, selectCustom Rate Limiting Parameters. -
In the
Custom Rate Limiting Parameterssection, selectView Configuration. -
Enter the maximum number of requests per unit in the
Numberfield. -
Select a unit for the
Per Periodfield in theRequest Rate Limitersection. -
Optionally enter a value for the
Burst Multiplierfield, which indicates how many times a user can hit the requests/unit limit. -
Optionally allow some IPs to bypass rate limits
- Select
IP Allowed Listin theIP(s) Allowed without Rate Limitingfield. - Enter a prefix that will not be rate limited. Use the
Add Itembutton to add more IP prefixes.
- Select
-
Optionally create different rules for specific HTTP methods, domains, HTTP paths, HTTP headers, or a combination of these.
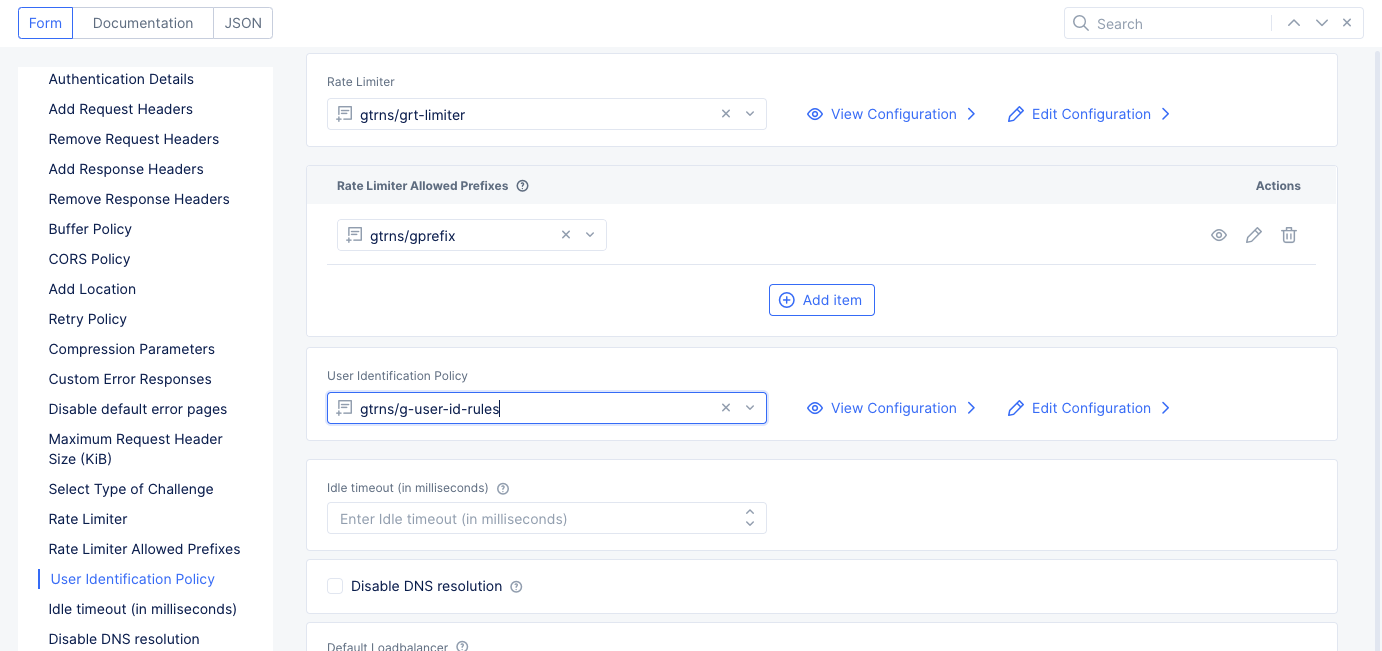
Figure: Apply Rate Limiting to Virtual Host
Note: This example sets 15 requests per second with 3 bursts allowed as the rate limit. Requests coming from 10.1.1.3/32 bypass rate limiting. There are no special rules for requests with specific parameters.
Step 3: Complete enabling the rate liming for virtual host.
Select Save and Exit to enable the rate limiting.