Bot Detection Rules Overview
Important: Bot detection rule self-service management is a limited availability feature. Contact your F5 account team for information.
The F5 Distributed Cloud Console allows you to view and manage bot detection rules. A bot detection rule contains criteria that Bot Defense uses to determine whether a transaction is from a human or automated source.
You can choose to turn rules on and off depending on whether they correctly identify your traffic:
- When a rule is turned on, Bot Defense takes the mitigation action defined in the Bot Endpoint Policy for all traffic that the rule identifies as automation (bots).
- When a rule is turned off, the rule does not block traffic, even if the Bot Endpoint Policy has a mitigation action configured, and your traffic is allowed to continue to the origin.
When you first configure Bot Defense, F5 supplies you with a set of bot detection rules. A subset of rules is turned on by default. The remaining rules are turned off. Monitor your traffic for approximately two weeks to see how rules that are turned on affect your traffic. After this initial two weeks, you can begin to turn rules on and off to make changes to how Bot Defense handles your traffic.
Important: Bot Defense does not block traffic that you add to your Bot Allowlist Policy even when a bot detection rule determines the traffic is automated.
Use the Bot Policies page in the Distributed Cloud Console to turn rules on and off as necessary without contacting F5. For example, after you turn on bot detection rules, you might turn off a specific rule while you analyze potential false positive results.
You can use the Distributed Cloud Console to perform the following tasks:
- View information about specific bot detection rules.
- Use the Traffic Analyzer to model potential rule changes to see the impact of the change on your traffic.
- Deploy bot detection rules and view details of your current and past bot detection rule deployment actions.
- View information about previous changes to a specific bot detection rule.
- Discard unwanted bot detection rule deployment drafts.
- View information about new rules and updates to existing rules.
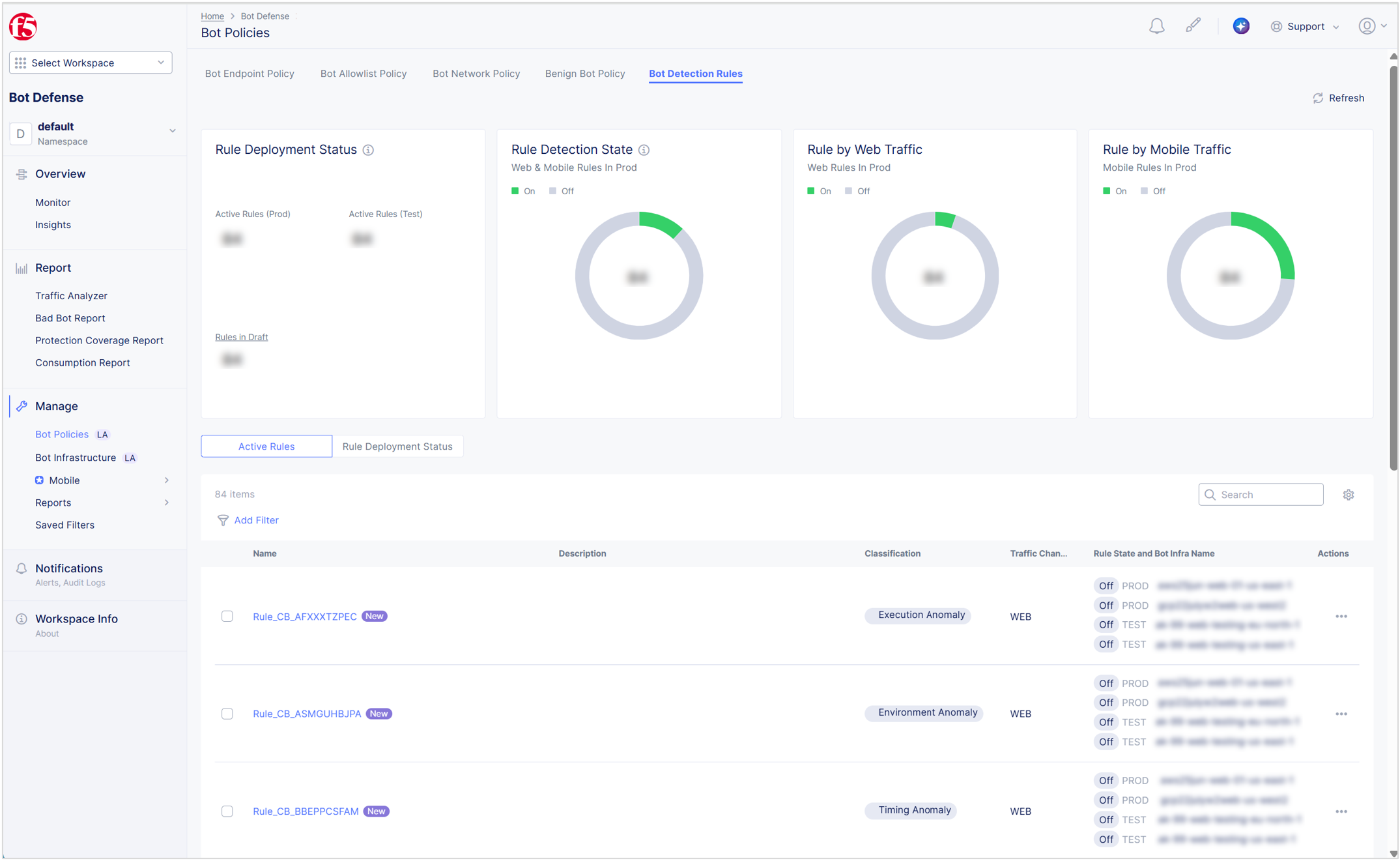
Figure: Manage Bot Detection Rules
Important: F5 recommends that you deploy each rule in a Test infrastructure before you deploy in your Production infrastructure.
F5 periodically releases new bot detection rules in response to new and evolving threats. When F5 deploys new rules, they are set to Off. Make sure to thoroughly test new rules in your Test infrastructure before you deploy them in a Production infrastructure. F5 provides release notes that provide information about the new rules. For information, see View Rule Updates.
Important: In rare situations, such as an attack that targets a major global vulnerability, F5 might deploy a new rule set to On. Whenever rules are enabled, the decision whether or not to block bots is based on your Endpoint Policy configuration. If your mitigation is set to Continue, Bot Defense does not block traffic.
Most bot detection rules operate independently. That is, each rule looks at different characteristics of your traffic and generally do not depend on or build on other rules.
If you have multiple infrastructures, when you set a rule to On, the bot detection rule is turned on for all infrastructures of the same environment type (Production or Testing) in the same cluster group that process the same type of traffic (Web or Mobile). Likewise, if you set a rule to Off, the rule is turned off on all infrastructures of the same environment type in the same cluster group that process that same traffic type. For information about cluster groups, see View Rule Details.
Bot Detection Rules Best Practices
F5 Recommends that you adhere to the following best practices:
- Not all bot detection rules are appropriate or necessary for all environments. Use the Traffic Analyzer to look at the traffic captured by each rule to determine if the rule correctly identifies automated traffic, or if it incorrectly identifies legitimate traffic as automation.
- Use the Traffic Analyzer to model rule changes before making a change in your Test infrastructure.
- Only enable bot detection rules in your Production infrastructure after you have thoroughly tested the rule and evaluated the impact of the rule on the traffic in your Test infrastructure.
- If a rule does not currently capture any traffic, you should proactively enable the rule so that it captures future traffic. For example, a rule may not capture traffic until a specific automated attack occurs. If the rule is enabled, then the rule begins capturing attack traffic immediately when the attack begins.
- F5 recommends that you choose a sampling of traffic captured by bot detection rules and check the traffic against your own internal logging tools or other systems and data to help confirm that the rules correctly identified the traffic. You can use this same process if you think a bot detection rule identified traffic as automation that you think might be legitimate human traffic.
Bot Detection Rule Classifications
Each bot detection rule is assigned a rule classifications. Classifications identify traffic types targeted by a bot detection rule.
| Classification | Description |
|---|---|
| Automation Framework | For direct detections of common automation frameworks such as Puppeteer, Headless Chrome, and Selenium. |
| Behavioral Anomaly | Includes detections derived from unrealistic or improbable user behavior. |
| Environment Anomaly | Includes browser spoofing and virtualization, as well as cases where an attacker has taken steps to obscure device properties. For SDK integrations, this classification may also include rooted and jailbroken devices or app execution on emulators or simulators. |
| Execution Anomaly | Includes detections where an attacker has taken steps to interfere with or manipulate the Bot Defense JavaScript or SDK. |
| Timing Anomaly | Includes detections for improbable or impossible sequences. |
View Rule Updates
When necessary, F5 adds new bot detection rules or updates existing rules to address evolving automated threats. When F5 adds a new bot detection rule, an alert is displayed in the Distributed Cloud Console.

Figure: New Rule Alert
Select the alert to open the Alerts panel. From the Alerts panel, you can open the Bot Detection Rule Updates report.
The Bot Detection Rule Updates report displays a list of recent bot detection rule updates, including when an update was deployed, the infrastructures where the update was deployed and the infrastructure traffic type (Web, Mobile or Both). You can also download release notes that provide additional details about the changes to the bot detection rules.
The following steps explain how to directly access the Bot Detection Updates Report:
-
From the Bot Defense navigation panel, select Manage > Reports > Bot Detection Rule Updates. The list of updates displays.
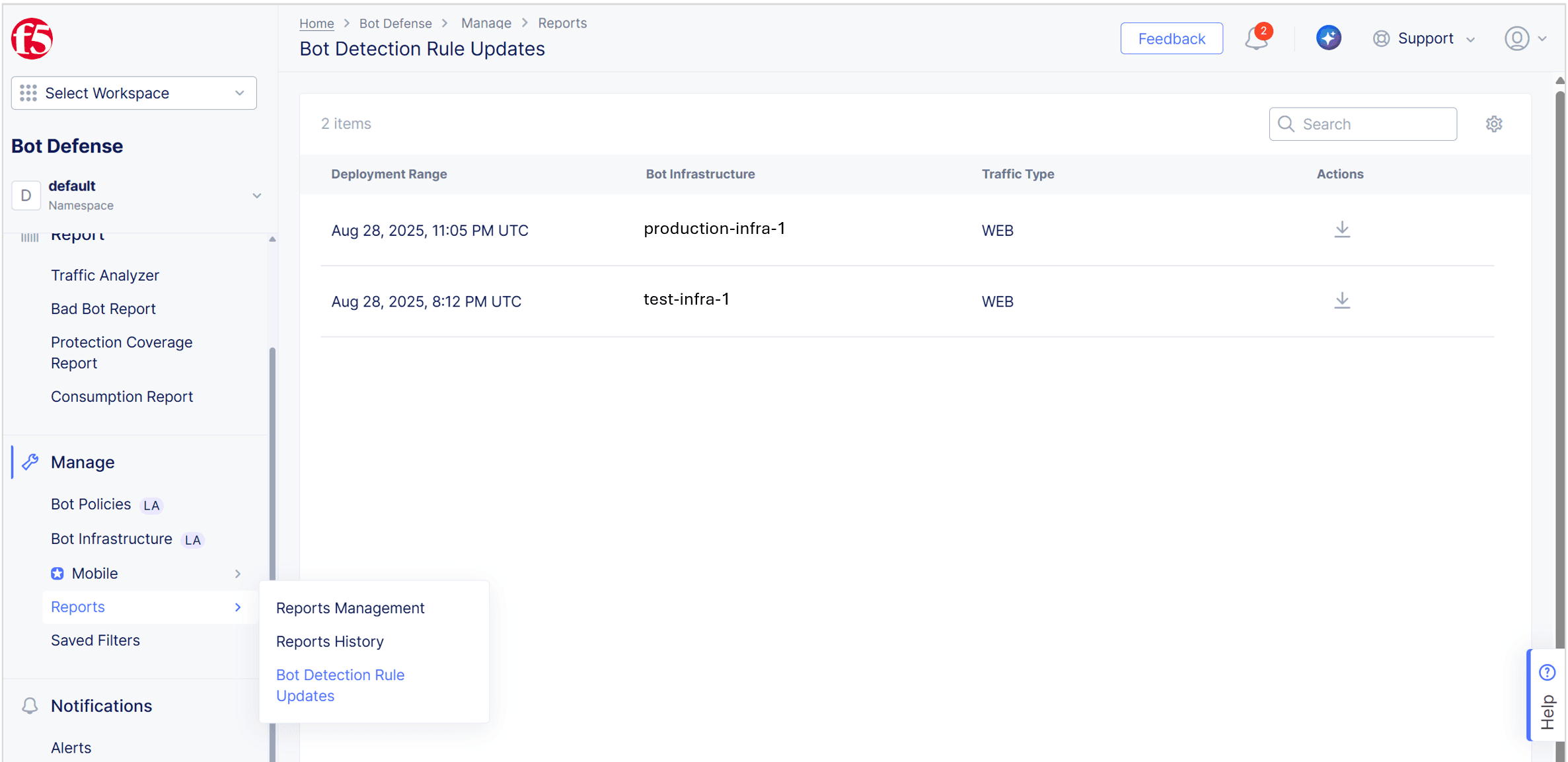
Figure: Bot Detection Updates
-
To download the release notes for a bot detection rule update, from the Actions column, select Download Report.
Bot Detection Update Release Notes contain the following information:
- New Rules: A list of new bot detection rules added to your infrastructure that Bot Defense uses to detect automation, including rule name and version, rule type, description, classifications and expected outcome of the rule.
- Updated Rules: A list of updates to existing bot detection rules, including rule name and version, rule type, description, classifications and expected outcome of the rule.
- Deprecated Rules: A list of bot detection rules that Bot Defense no longer uses to detect automation. Deprecated rules are no longer visible in the list of bot detection rules in Bot Defense and are removed from any completed or in-progress rule deployments in your Bot Defense infrastructures.
