Service Mesh
F5® Distributed Cloud Mesh’s Service Mesh is a centrally managed globally distributed load balancer and proxy with service discovery, health checking, application micro-segmentation, and application policy providing the most advanced implementation of edge load-balancer with ingress/egress capability for any service mesh. Service discovery integrates with multiple registries like Kubernetes, Consul, or DNS along with health checking support for http/https, tcp, custom, etc. End-point health is distributed to all the sites where the virtual service is exposed using extensions to the BGP protocol and this provides us with valuable insight on how to globally distribute the load balancing function. Support for both TLS and mutual-TLS for authentication with policy-based authorization on the proxy provides the capability to enforce end-to-end security of application traffic. In addition, the proxy gives the ability to terminate user traffic in the F5 Distributed Cloud global network and use a persistent connection to serving end-points to accelerate and load balance to the most optimal end-point. It is “out-of-the-box” ready and accessible when F5 Distributed Cloud Node or Cluster is deployed.
If you are interested in further details of how the features described in this guide work, read more below in Concepts.
Introduction to F5 Distributed Cloud Mesh Service Mesh
With all the Node or Cluster deployments, you have the ability to leverage additional Distributed Cloud Mesh and Distributed Cloud App Stack services as a simple add-on. This section discusses specifically the Mesh's Service Mesh features.
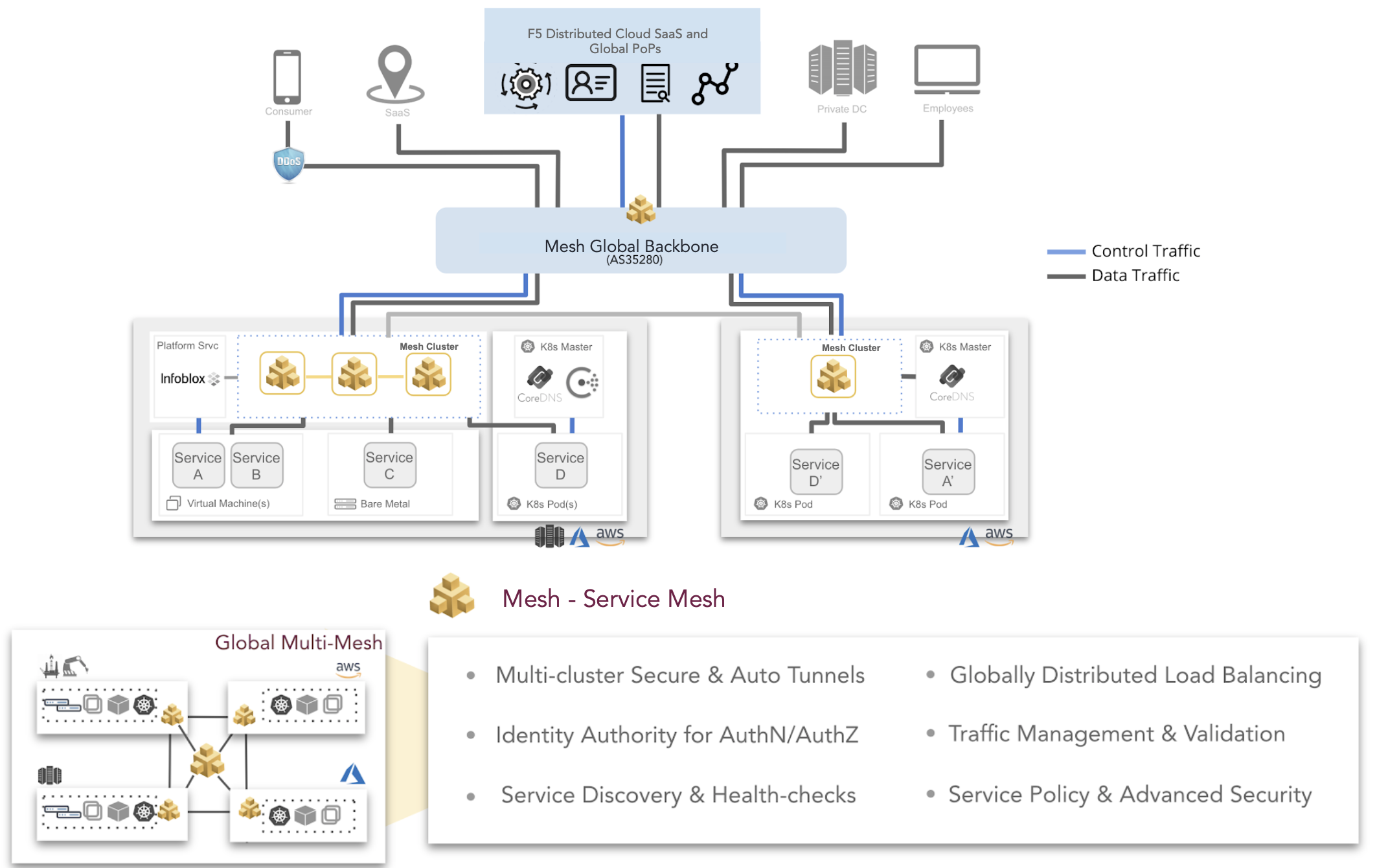
Figure: The Service Mesh Features
Service Mesh Features
-
Multi-cluster Secure & Auto Tunnels
- Mesh’s consolidated network and application software is a Cloud-native software stack that can be used to secure and connect Kubernetes clusters, Virtual Machines and BareMetal across multiple environments and networks. Using Mesh Secure Networking tunnels are automatically created between clusters either directly using full-mesh or indirectly via hub-spoke. Mesh Secure Backbone offerings further augment the security and connectivity of these clusters.
-
Identity Authority for AuthN/AuthZ
- For applications using secrets (i.e. TLS/mTLS certs, passwords, tokens, etc.), F5 Distriubuted Cloud provides a tenant-specific CA and PKI infrastructure for managing secrets, while providing a mechanism (Blindfold) to store secrets in a centralized control plane without worrying about system compromise. Using the policy framework AuthZ/AuthN can be applied at network or API levels.
-
Service Discovery & Health-checks
- Service endpoints are discovered and globally available and reachable to all Virtual Hosts on Mesh locations. Service discovery integrations supported today include DNS, Kubernetes, and Hashicorp Consul. All discovered or configured endpoints and VIPs are automatically probed for explicit (configured) or implicit (i..e latency, error rate, response times, etc.) health checks. The global visibility of endpoints and availability allow for optimized load balancing of clients to services.
-
Globally Distributed Load Balancing
- In addition to Mesh Global Load Balancing, since the proxy is distributed and the health of all the endpoints is available across multiple sites, the routing and traffic control decision can be made based on the actual health of the individual endpoints across all the sites and not just the proxies front-ending the endpoints. This is especially useful for high traffic web-services.
-
Traffic Management & Testing
- In additional to GSLB traffic management functionality, rich HTTP/HTTPS routing functionality is available. Matching on parameters such as URLs, headers, query parameters, HTTP methods, etc. are available. Customization to matching is also available using F5 Distriubuted Cloud’s Programmable v8 engine. Routing options based on matched criteria include send a direct response, change of protocol, add/remove headers, timeouts/retries, send to WAF (Web Application Firewall), endpoint selection/grouping, etc. These are building blocks to Application-specific testing A/B testing, canary, staging rollouts, etc.
-
Service Policy & Advanced Security
- Application microsegmentation per virtualhost and services in a namespace using an intent based service policy (L7), enabling enhanced Application Security matching with regex-based label selectors, client IP or ASN lists, actions of allowing, deny (with future options to rate-limit or custom using Java v8 chrome engine).
Concepts
The following concepts are used for Service Mesh features. Click on each one to learn more: