Credentials
Objective
This guide provides instructions on how to generate various credentials related to F5® Distributed Cloud Services from the platform.
F5® Distributed Cloud Console provides two types of credentials:
-
My Credentials: Are generated and used for different authentication and authorization purposes while accessing F5® Distributed Cloud Services APIs or deploying apps using F5® Distributed Cloud Services vK8s. -
Service Credentials: Are generated by administrators to create custom service roles that are associated with service users.
Note: The
My Credentialsinherit the roles of the users. In case of service credentials, you can assign specific roles to the service user.
Using the instructions provided in this guide, you can create various types of credentials and download them for using in API requests.
Prerequisites
The following prerequisites apply:
-
A valid F5 Distributed Cloud Console Account is required. If you do not have an account, see Getting Started with Console.
-
A single-node or multi-node F5® Distributed Cloud Services site in case of application deployment. If you do not have a site, visit Site Management.
My Credentials
My Credentials options can be generated and downloaded from the Console:
-
API Tokens: The tokens are used in site deployment, and also for the authorization in the API requests.
-
API Certificates: These certificates are used in API requests.
Note: All certificates follow x.509 standard.
- vK8s KubeConfig: These are the vK8s KubeConfigs for deploying your applications using F5® Distributed Cloud Services vK8s.
Note: You can use either API certificate or API token for authenticating. It is recommended to use API certificates as they offer more robust security via Mutual TLS (mTLS) authentication. The API tokens are used with one-way TLS authentication.
Generate API Certificate for My Credentials
Features can be viewed, and managed in multiple services.
This example shows Credentials setup in Administration.
Step 1: Open F5® Distributed Cloud Console > select Create Credentials.
- Open
F5® Distributed Cloud Consolehomepage, selectAdministrationbox.
Note: Homepage is role based, and your homepage may look different due to your role customization. Select
All Workspacesdrop-down menu to discover all options. Customize Settings:Administration>Personal Management>My Account>Edit work domain & skillsbutton >Advancedbox > checkWork Domainboxes >Save changesbutton.
Figure: Homepage
Note: Confirm
Namespacefeature is in correct namespace, drop-down selector located in upper-left corner. Not available in all services.
-
Select
Personal Managementin left column menu > selectCredentials. -
Select
+ Add Credentialsbutton.
Note: If options are not showing available, select
Showlink inAdvanced nav options visiblein bottom left corner. If needed, selectHideto minimize options from Advanced nav options mode.
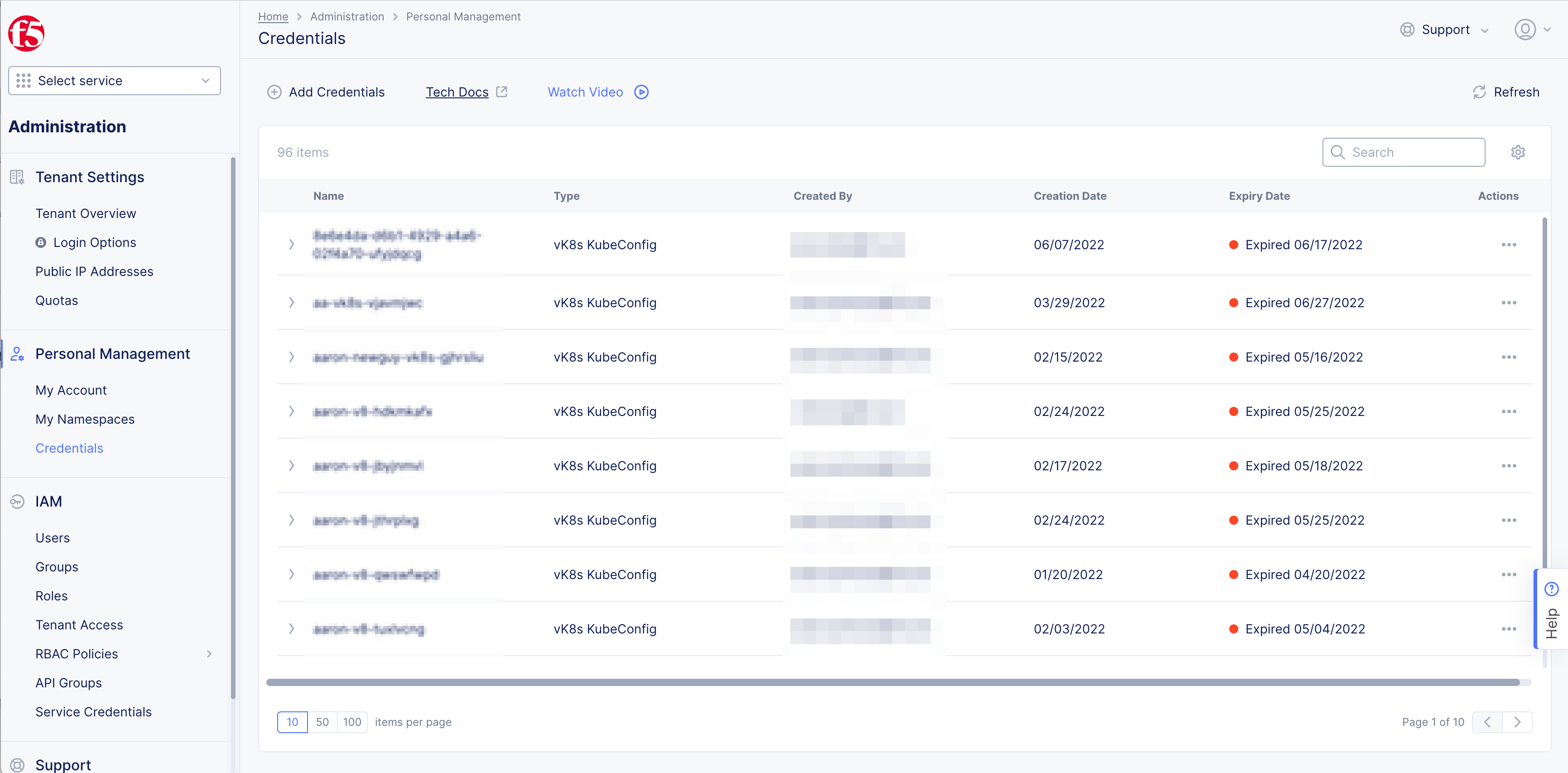
Figure: Create Credentials
Step 2: Setup Credential.
-
Enter
Namefor your certificate. -
Select
API CertificateinCredential type. -
Enter
Password>Confirm Password. -
Select
Expiry datein calendar drop-down.
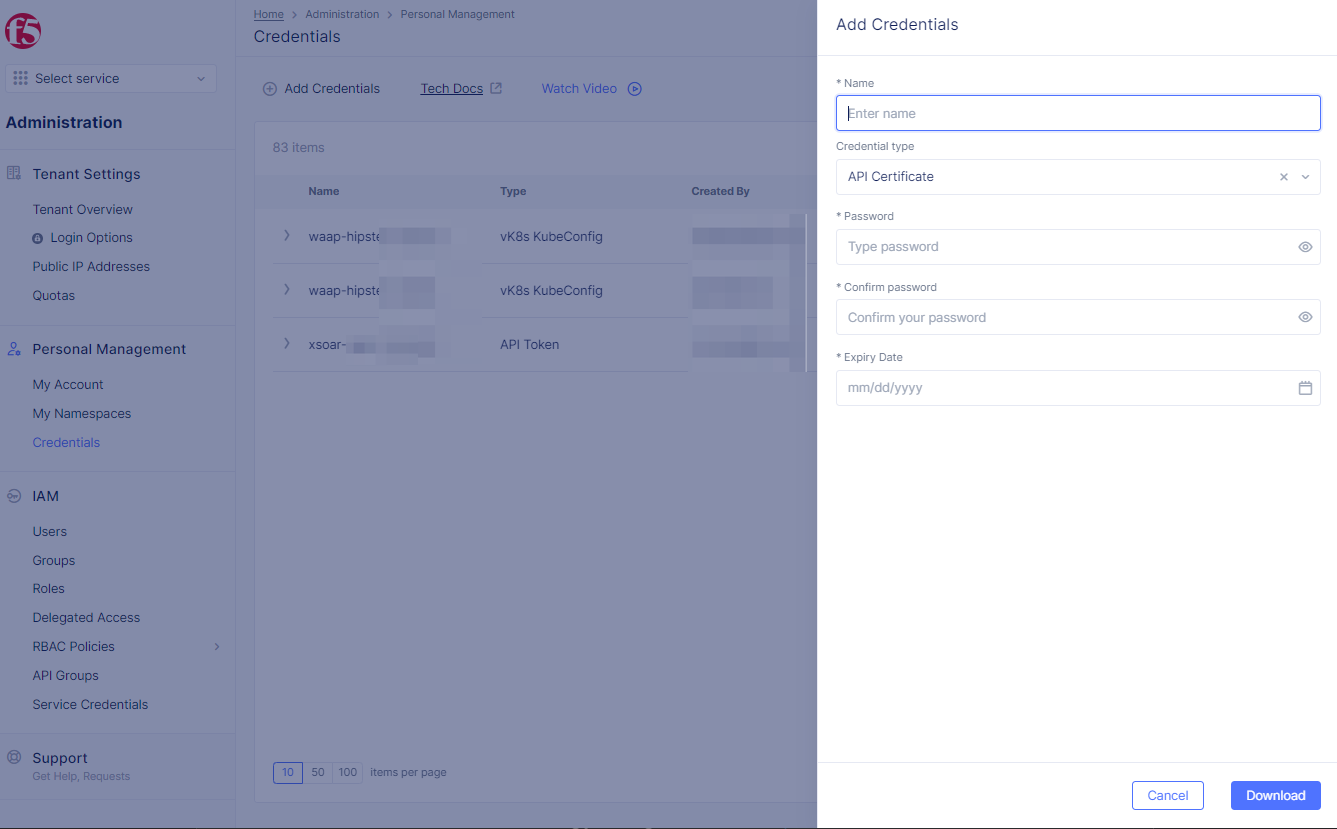
Figure: Add Credentials
Step 3: Generate and download certificate.
- Select
Downloadto generate certificate in.p12file format.
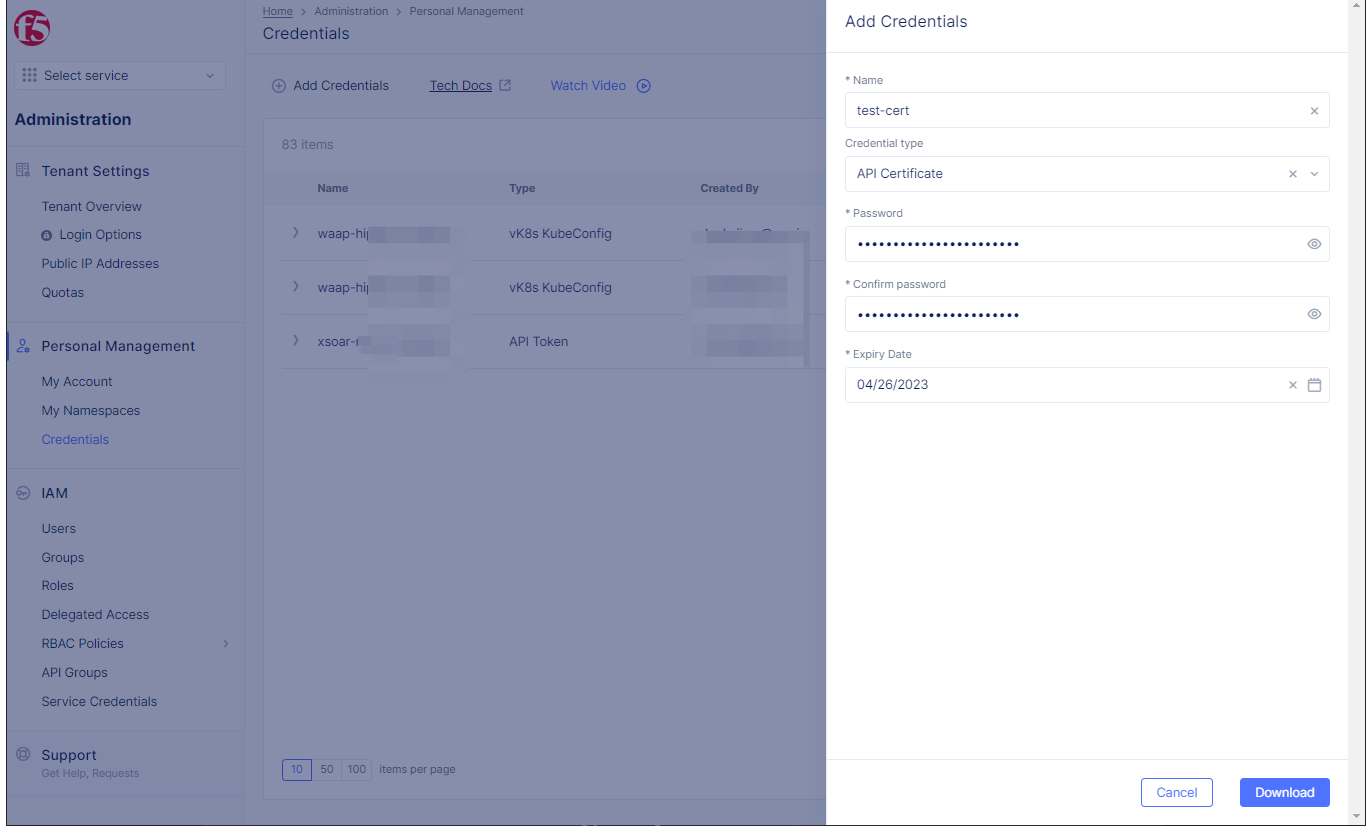
Figure: Create API Certificate
Note: The maximum allowed expiry date for users is set by the tenant administrator. The system allows the administrator to set a maximum expiry of 365 days. The default expiry is 90 days.
Credentialwill appear inCredentialspage if created.
Note: Reference date confirms correct Credential.
After generating, you can use the certificate in API request.
Sample API request to delete a namespace:
curl -k -X POST --cert-type P12 --cert ~/Downloads/<api-creds>.p12:<password> https://tenant>.console.ves.volterra.io/api/web/namespaces/<namespace>/cascade_delete -v
Note: It is recommended to specify the full path to certificate.
Generate Kubeconfig for My Credentials
Step 1: Open F5® Distributed Cloud Console > select Create Credentials.
- Open
F5® Distributed Cloud Consolehomepage, selectAdministrationbox.

Figure: Homepage
- Select
Personal Managementin left column menu > selectCredentials>+ Add Credentials.
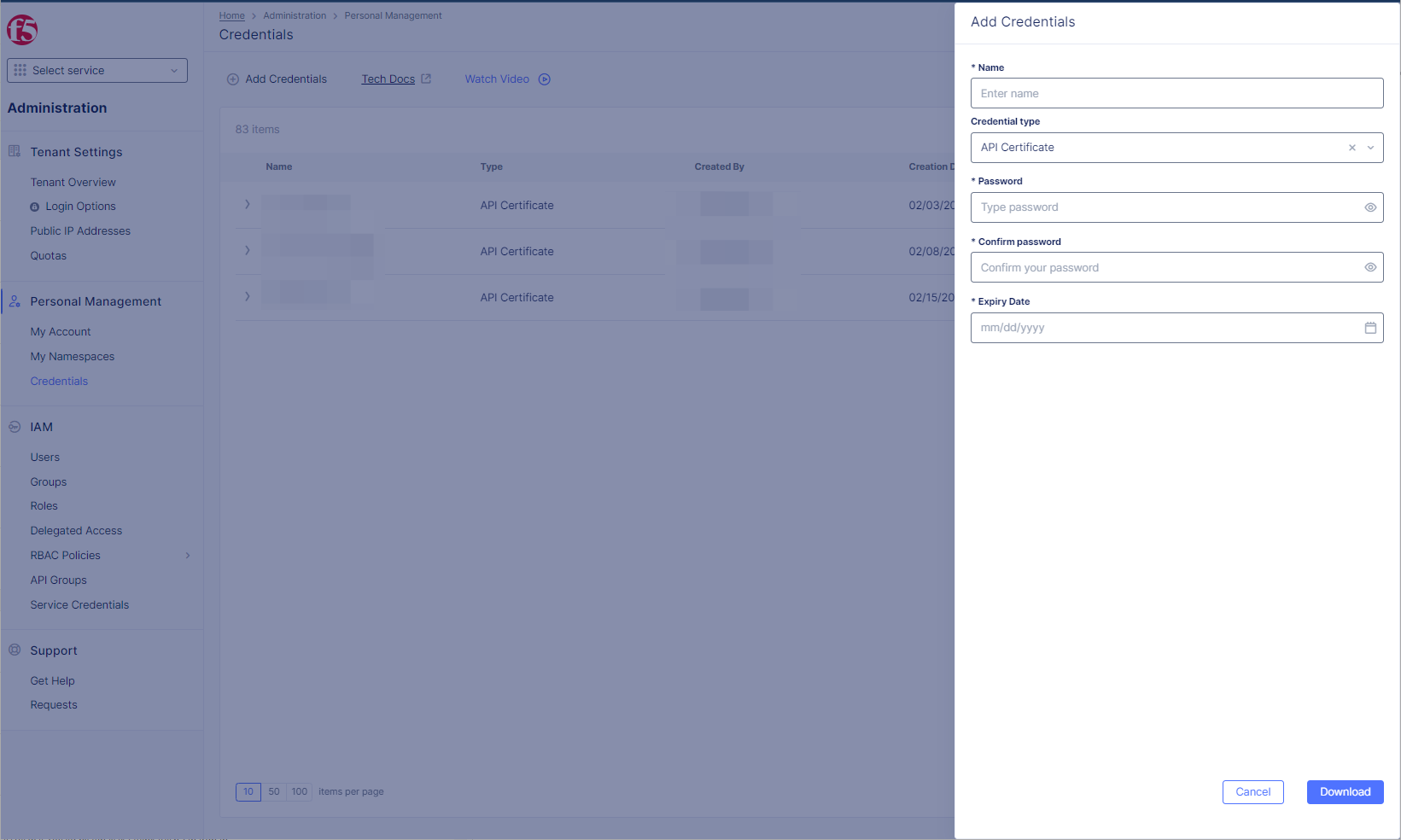
Figure: Create Credentials
Step 2: Setup Credential type.
-
Enter
Namefor your certificate. -
Select
vK8s KubeConfiginCredential typedrop-down menu. -
Select
Sitein drop-down menu. -
Select
Namespaceoption in drop-down menu. -
Select
vK8s cluster nameoption in drop-down menu. -
Select
Expiry datefrom calendar drop-down.
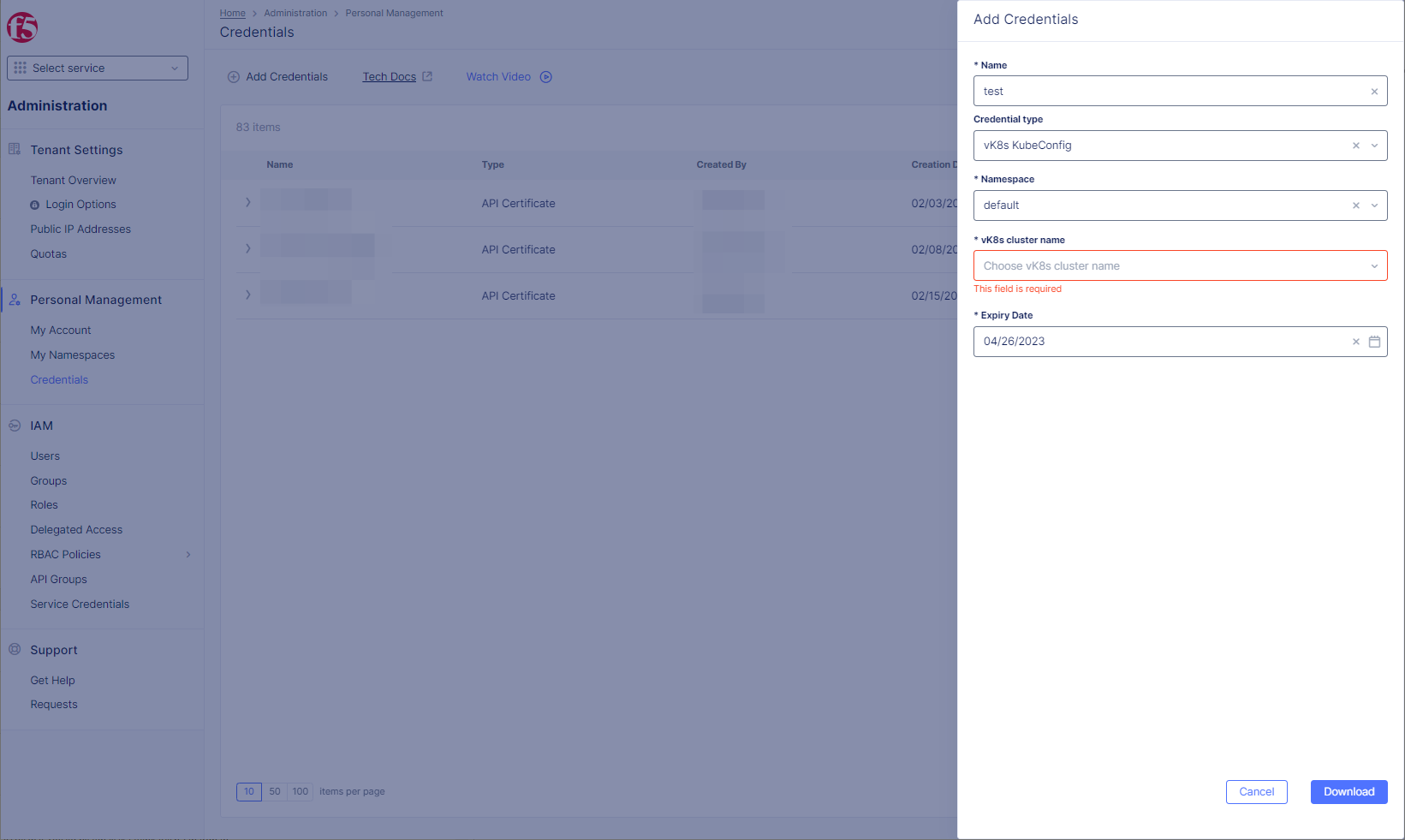
Figure: Create vK8s KubeConfig
Step 3: Generate and download vK8s KubeConfig Certificate.
- Select
Downloadbutton to generate and download vK8s KubeConfig certificate file.
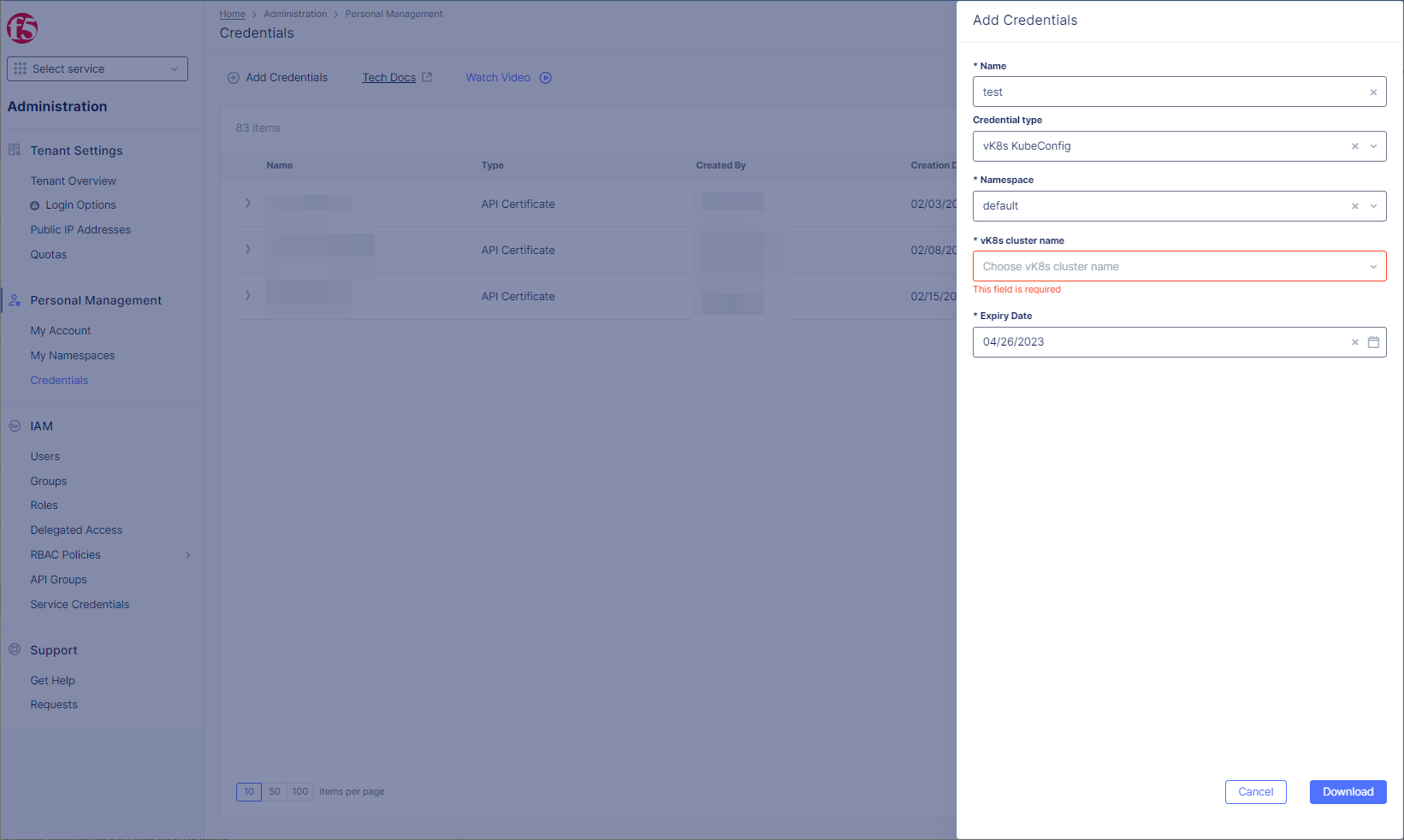
Figure: Generate and download vK8s KubeConfig Certificate
Note: The maximum allowed expiry date for users is set by the tenant administrator. The system allows the administrator to set a maximum expiry of 365 days. The default expiry is 90 days.
- Use in deployments after generating.
The following is a sample kubectl request to view the configuration:
kubectl config --kubeconfig=<kubeconfig-file> view
Generate API Tokens for My Credentials
Step 1: Create Credentials in F5® Distributed Cloud Console.
- Open
F5® Distributed Cloud Consolehomepage, selectAdministrationbox.

Figure: Homepage
- Select
Personal Managementin left column menu > selectCredentials>+ Add Credentials.
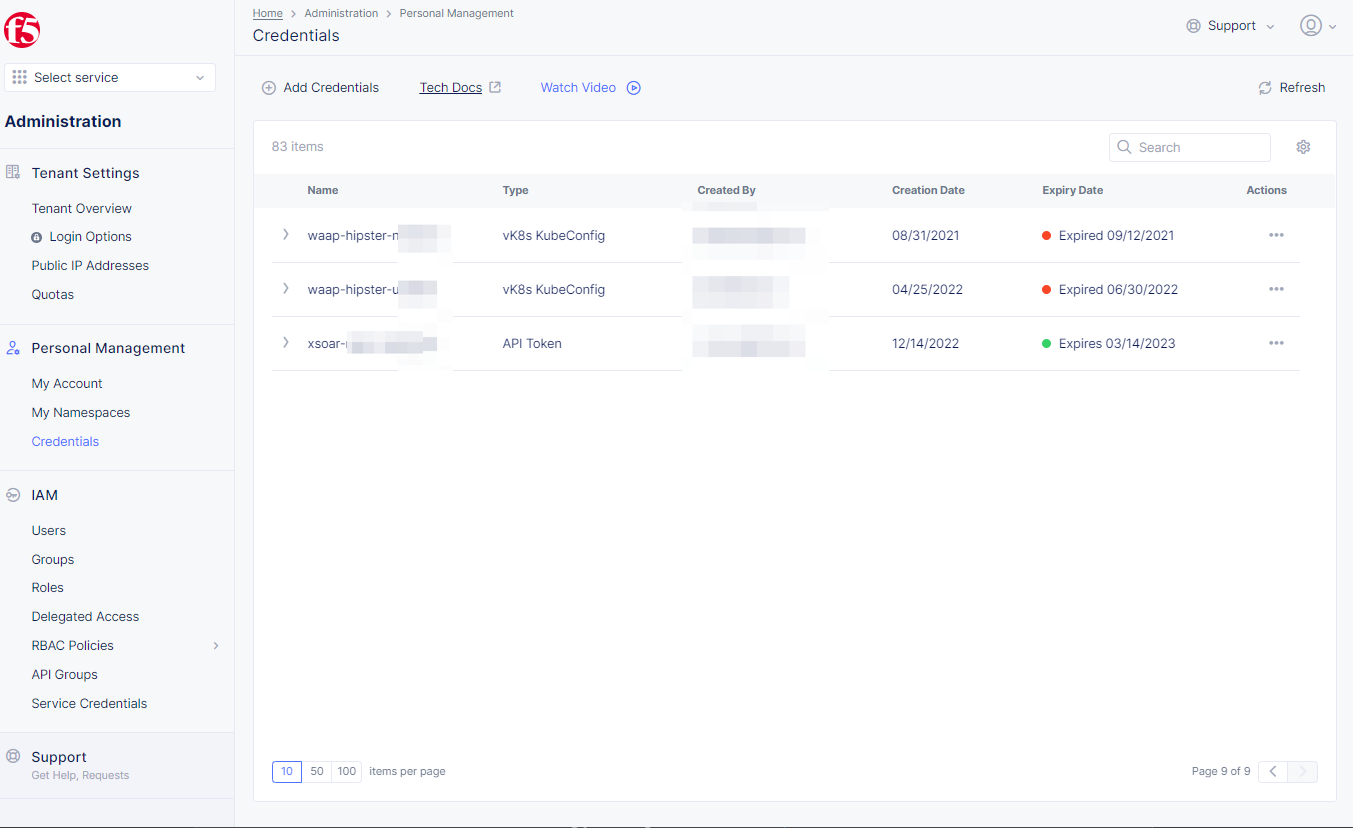
Figure: Create Credentials
Step 2: Setup Credential type.
-
Enter
Name. -
Select
API TokeninCredential typedrop-down menu. -
Select
Expiry datefrom calendar drop-down.
Step 3: Create API Token.
- Select
Generatebutton.
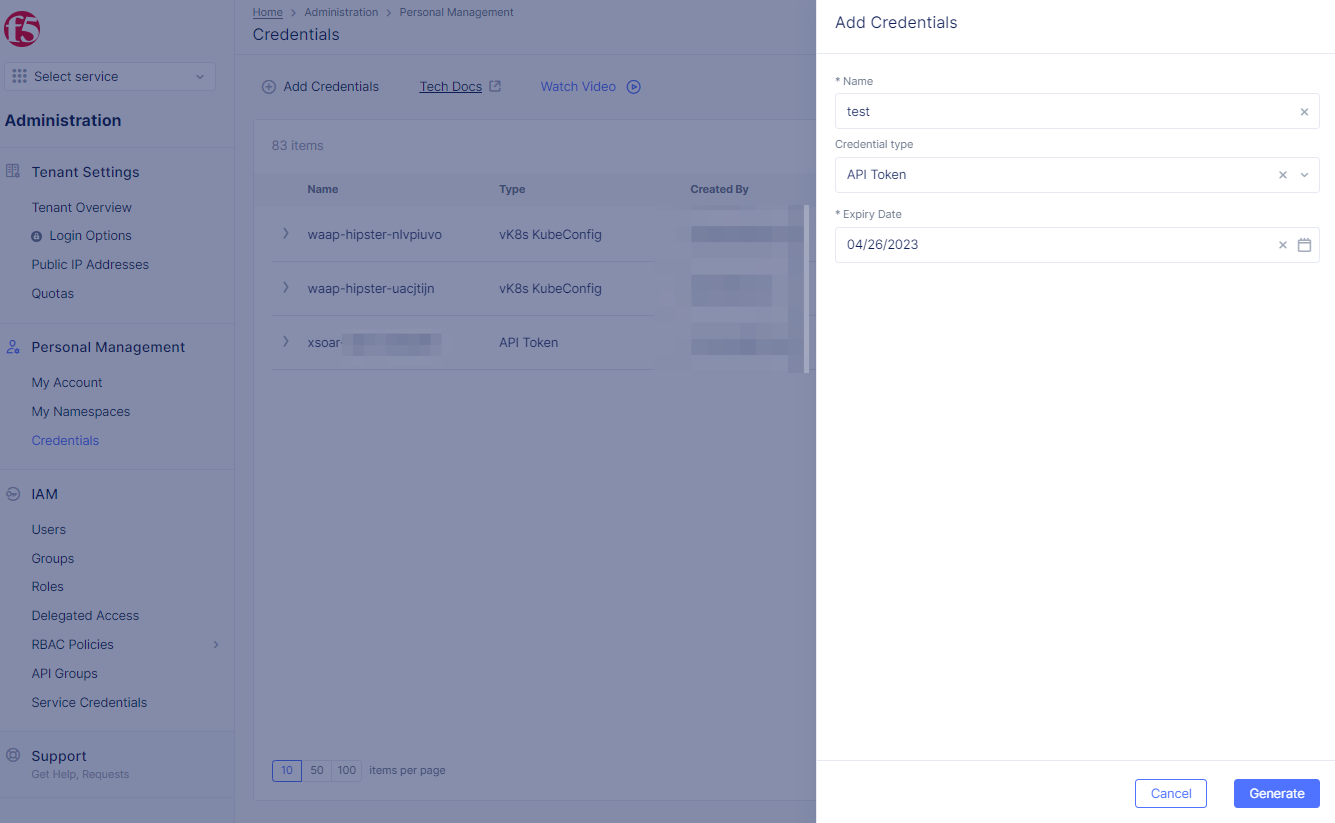
Figure: Add Credentials
Note: The maximum allowed expiry date for users is set by the tenant administrator. The system allows the administrator to set a maximum expiry of 365 days. The default expiry is 90 days.
Step 4: Obtain API Token.
-
Select
Copybutton to copy API token. -
Select
Donebutton to exit pop-up window.
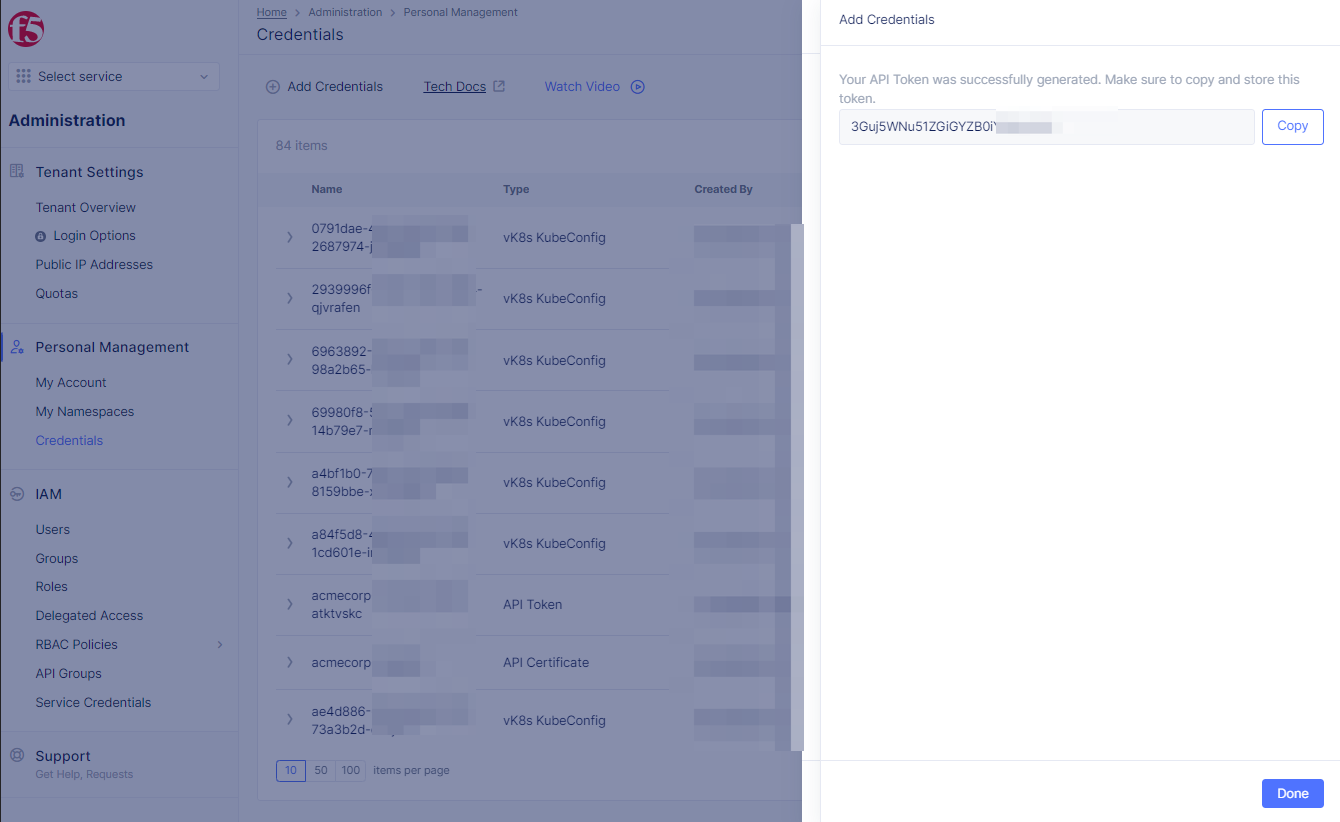
Figure: Add Credentials
After generating, you can use it in API request with the authorization header.
The following is a sample API request:
curl -k -X GET https://<tenant>.console.ves.volterra.io/api/web/namespaces -H 'Authorization: APIToken <token value>'
Note: All API access with the token will have the same RBAC assigned to the user who created the token.
Revoke API Credentials for My Credentials
You can force an API credentials object to be expired before it's configured or before the default expiry time.
Revoke API credentials instructions:
Step 1: Open Credentials in F5® Distributed Cloud Console.
- Open
F5® Distributed Cloud Consolehomepage, selectAdministrationbox.

Figure: Homepage
- Select
Personal Managementin left column menu > selectCredentials.
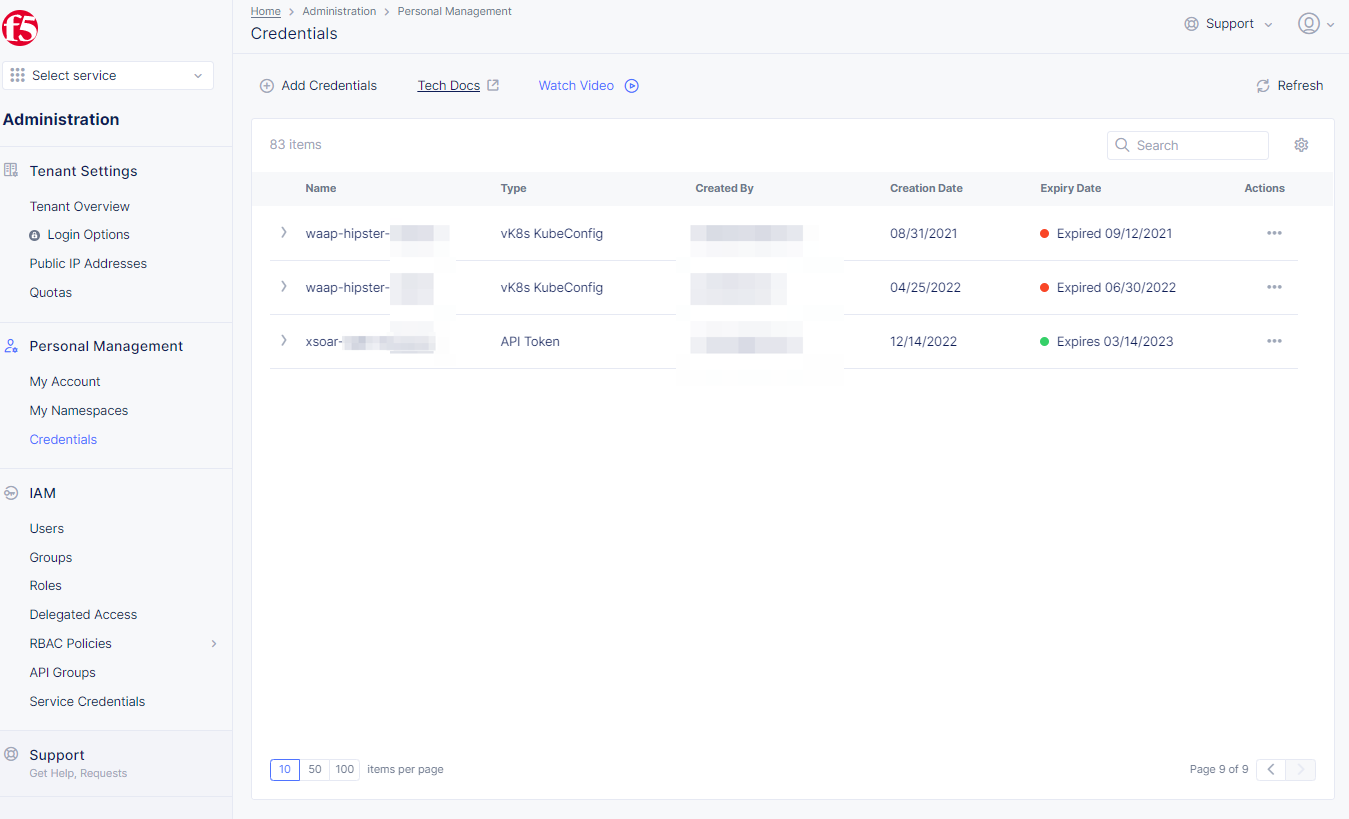
Figure: Credentials
Step 2: Perform revoke operation for an existing credential object.
-
API Token: Select...inActionscolumn, selectForce Expiryto revokeAPI Token. -
API Certificate: Select...inActionscolumn, selectDeleteto revokeAPI Certificate.
Note: All certificates follow x.509 standard.
vK8s KubeConfig Credential: Select...inActionscolumn, selectDeleteto revokevK8s KubeConfig Credential.
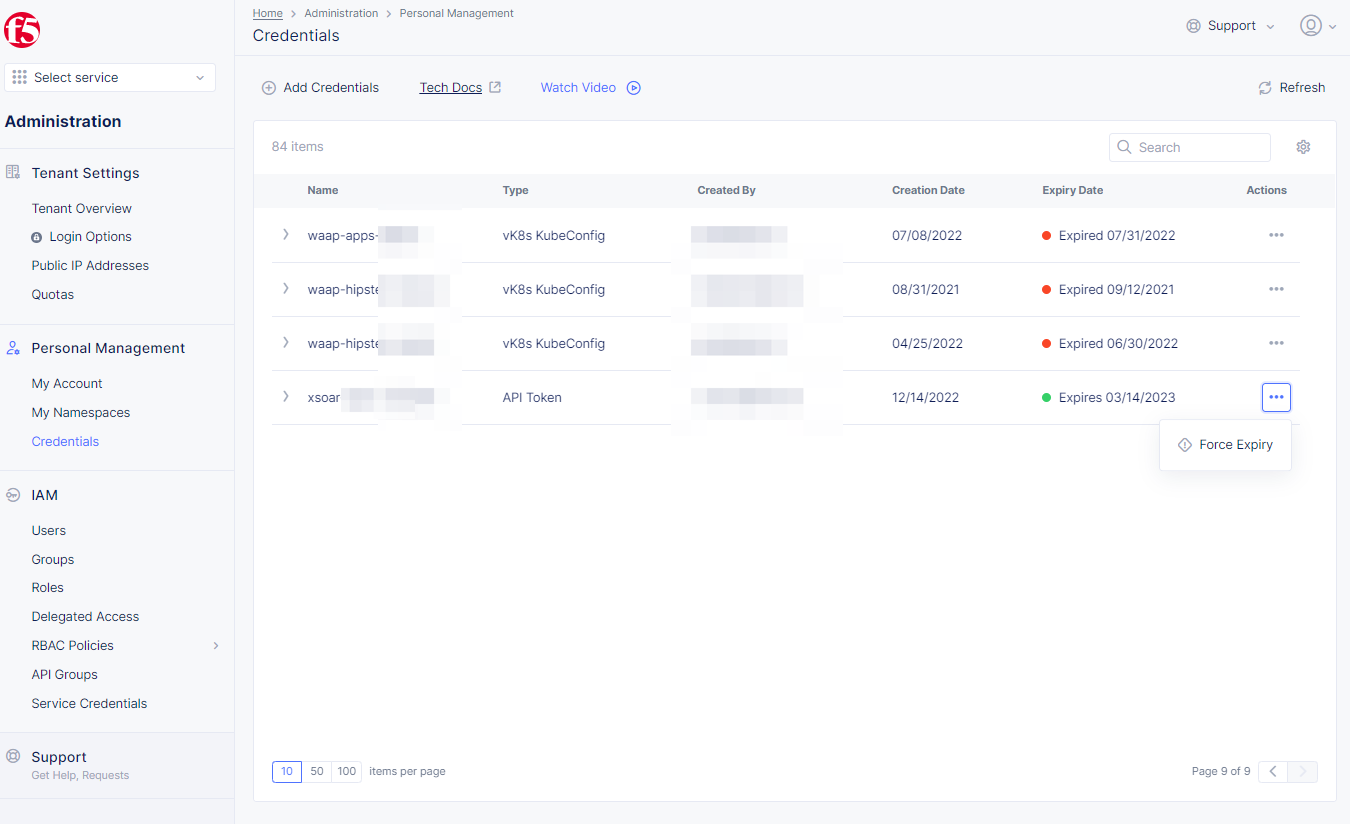
Figure: API Token Force Expiry Option
Step 3: Complete revoke operation.
- In case of
API Token, selectForce Expiryin the confirmation window to cause API credential object expiry.
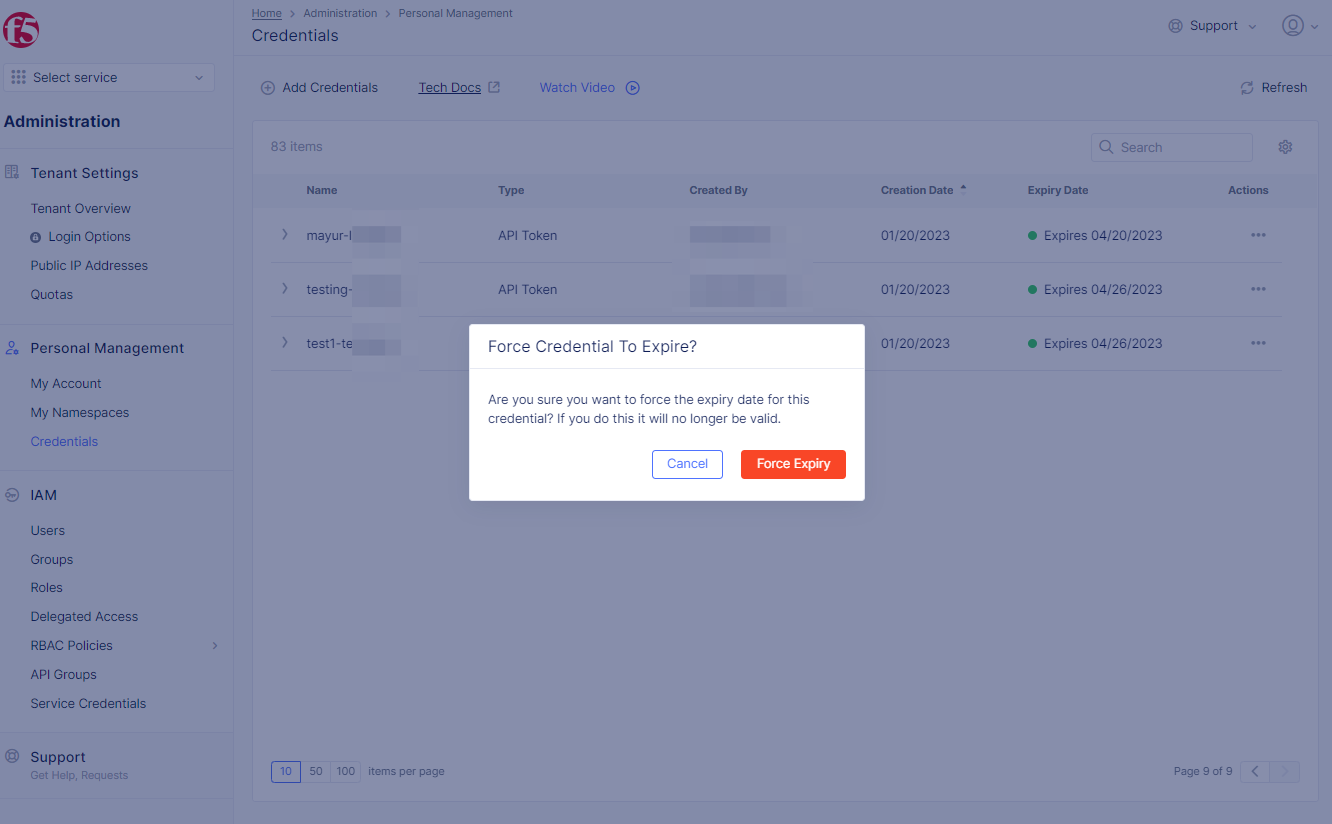
Figure: API Token Force Expiry Confirmation
Note: You can renew or delete an expired credential. Select
...>Renewagainst expired credential from the list of credentials to renew it. Set an expiry date, and selectRenew Credentialin the confirmation box. Select...>Deleteagainst expired credential from the list of credentials to delete it. SelectDeletein the confirmation box.
- In case of API certificates or vK8s KubeConfigs, select
Deletein the confirmation window. This forces the expiry for the object and also deletes it from the F5 system.
Service Credentials
Service credentials can be created by administrators. These credentials are assigned roles that provide API access to F5 Distributed Cloud Services.
Note: When you add API Tokens or API Certificate service credentials to a user group that you use for Delegated Access or for a Managed Service Provider (MSP) access mapping, you can also use those service credentials in the mapped managed tenant or the MSP child tenant.
Generate API Certificate for Service Credentials
Step 1: Open F5® Distributed Cloud Console > select Service Credentials.
-
Open
F5® Distributed Cloud Consolehomepage, selectAdministrationbox. -
Select
IAMin left-menus > selectService Credentials> select+ Add Service Credentials.
- Select
+ Create service credentialsbutton.
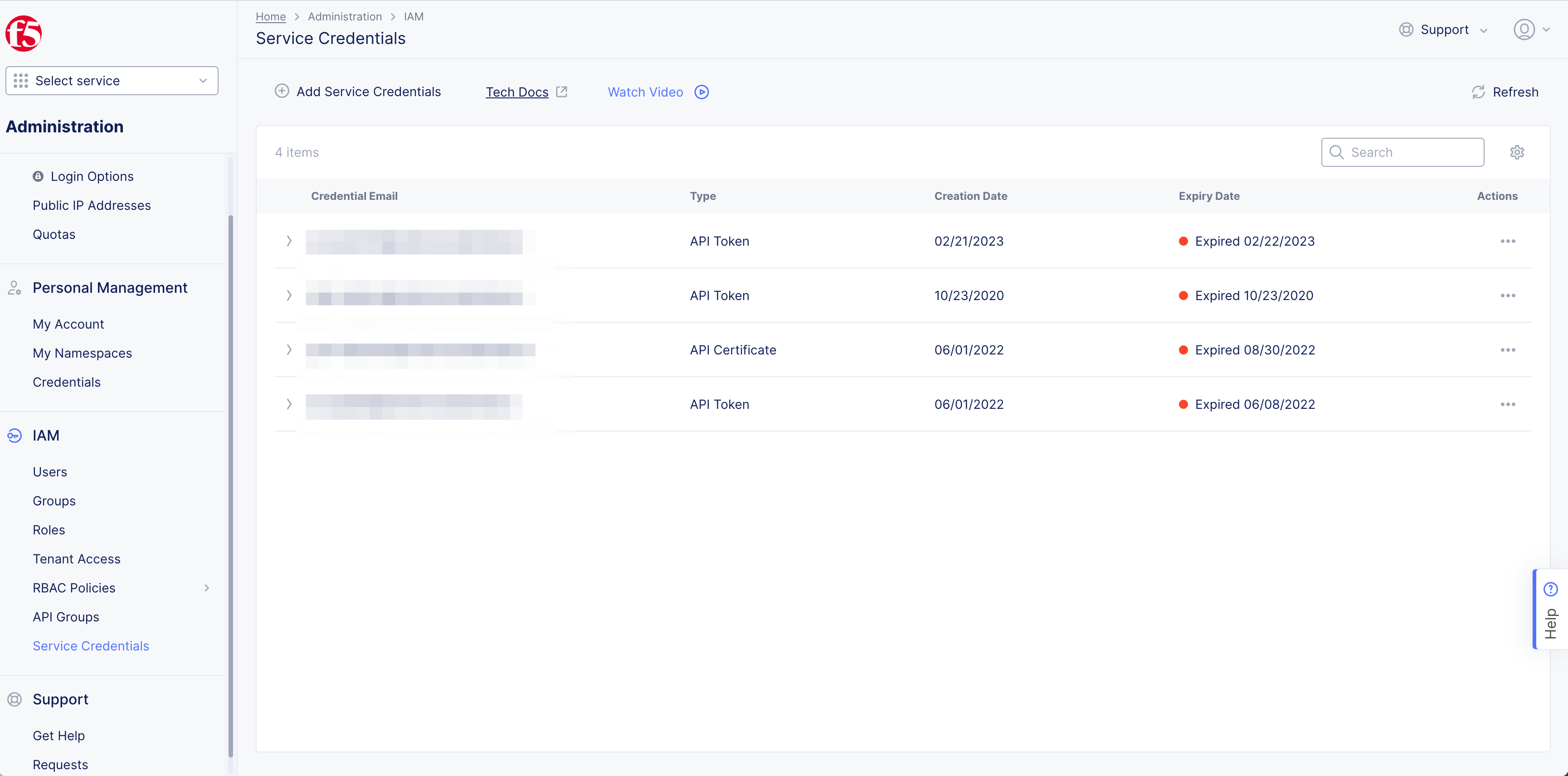
Figure: Open Service Credentials
Step 2: Setup Credential type.
-
Enter
NameinCredential Emailbox to generate unique email name,name@volterracredentials.io. -
Select
API CertificateinCredential typedrop-down menu. -
Enter
Password>Confirm Password. -
Select
Expiry datefrom calendar drop-down. -
Optionally select
Assign Service Credential to Group. Select the groups to which you want to add the service credential and then selectAssign to Group.Note: You can also assign service credentials to user groups when you enable SCIM.
-
Optionally: Select
Assign roles and namespacesto open pop-up window.-
Select
Namespacedrop-down option.-
all application namespaces -
shared -
system -
default -
your custom namespace, Example:aatw
-
-
Select
Make Admincheckbox to grant the admin role. -
Select
Roleboxes to select a role from the displayed options.
Note: You can add more roles using the
+ Add another role.- Select
Add rolesbutton.
-
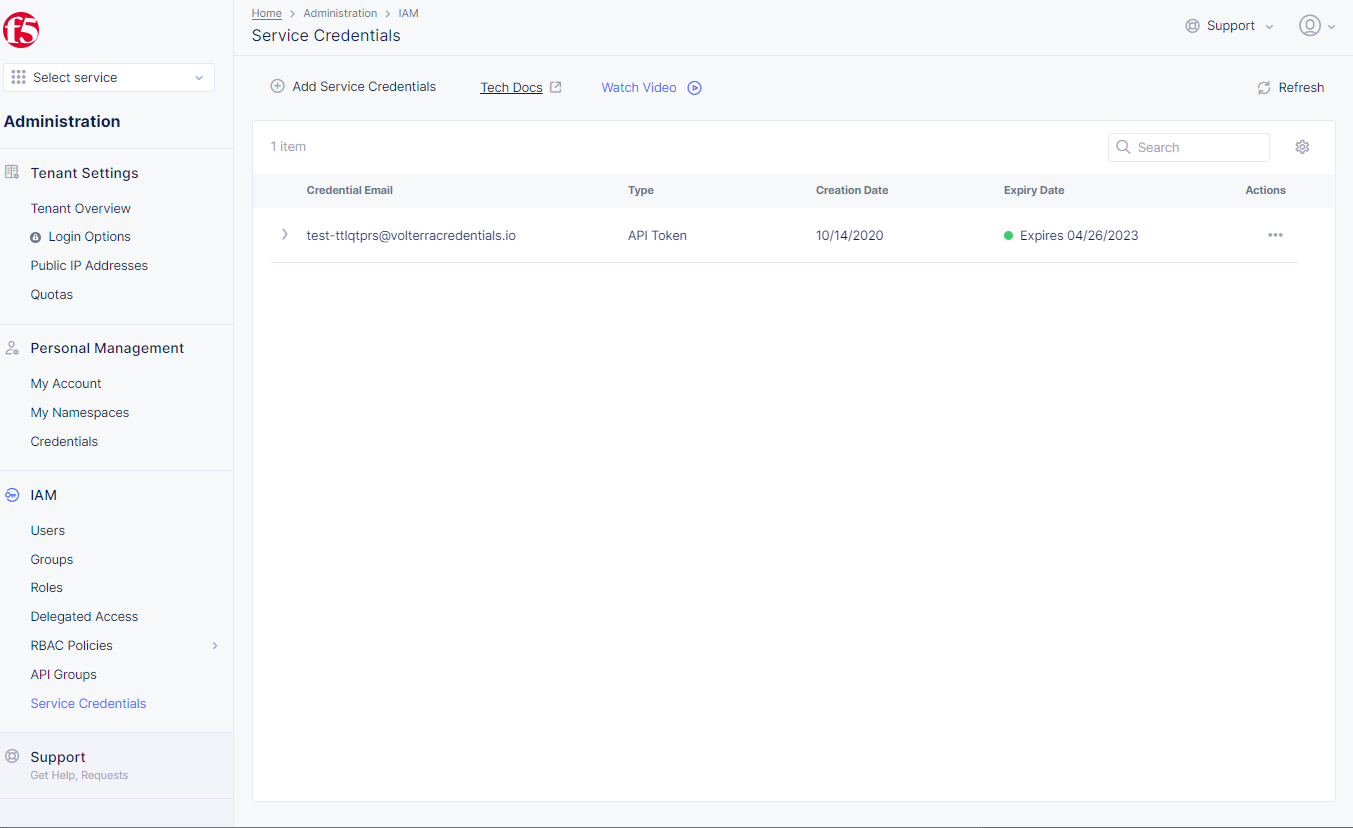
Figure: Open Service Credentials
Step 3: Generate and download certificate.
Select Download button to download the certificate in .p12 file format.
Note: The maximum allowed expiry date for users is set by the tenant administrator. The system allows the administrator to set a maximum expiry of 365 days. The default expiry is 90 days.
Generate Kubeconfig for Service Credentials
Step 1: Start creating credentials in F5® Distributed Cloud Console.
- Open
F5® Distributed Cloud Consolehomepage, selectAdministrationbox.

Figure: Homepage
- Select
IAM, selectService Credentials> select+ Add Service Credentials.

Figure: Credentials
Step 2: Setup Credential type.
-
Enter
NameinCredential Emailbox to generate unique email name,name@volterracredentials.io. -
Select
vK8s KubeConfiginCredential typedrop-down menu. -
Select
Sitein drop-down menu.
-
Select
Expiry datefrom calendar drop-down. -
Optionally select
Assign Service Credential to Group. Select the groups to which you want to add the service credential and then selectAssign to Group.Note: You can also assign service credentials to user groups when you enable SCIM.
-
Optionally: Select
Assign roles and namespacesto open pop-up window.-
Select
Namespacedrop-down option.-
all application namespaces -
shared -
system -
default -
your custom namespace, Example:aatw
-
-
Select
Make Admincheckbox to grant the admin role. -
Select
Roleboxes to select a role from the displayed options.
Note: You can add more roles using the
+ Add another role.- Select
Add rolesbutton.
-
Step 3: Create and download vK8s KubeConfig.
Select Download button.
Note: The maximum allowed expiry date for users is set by the tenant administrator. The system allows the administrator to set a maximum expiry of 365 days. The default expiry is 90 days.
Generate API Token for Service Credentials
Step 1: Start credential creation in F5® Distributed Cloud Console.
- Open
F5® Distributed Cloud Consolehomepage, selectAdministrationbox.

Figure: Homepage
- Select
IAM, selectService Credentials> select+ Add Service Credentials.
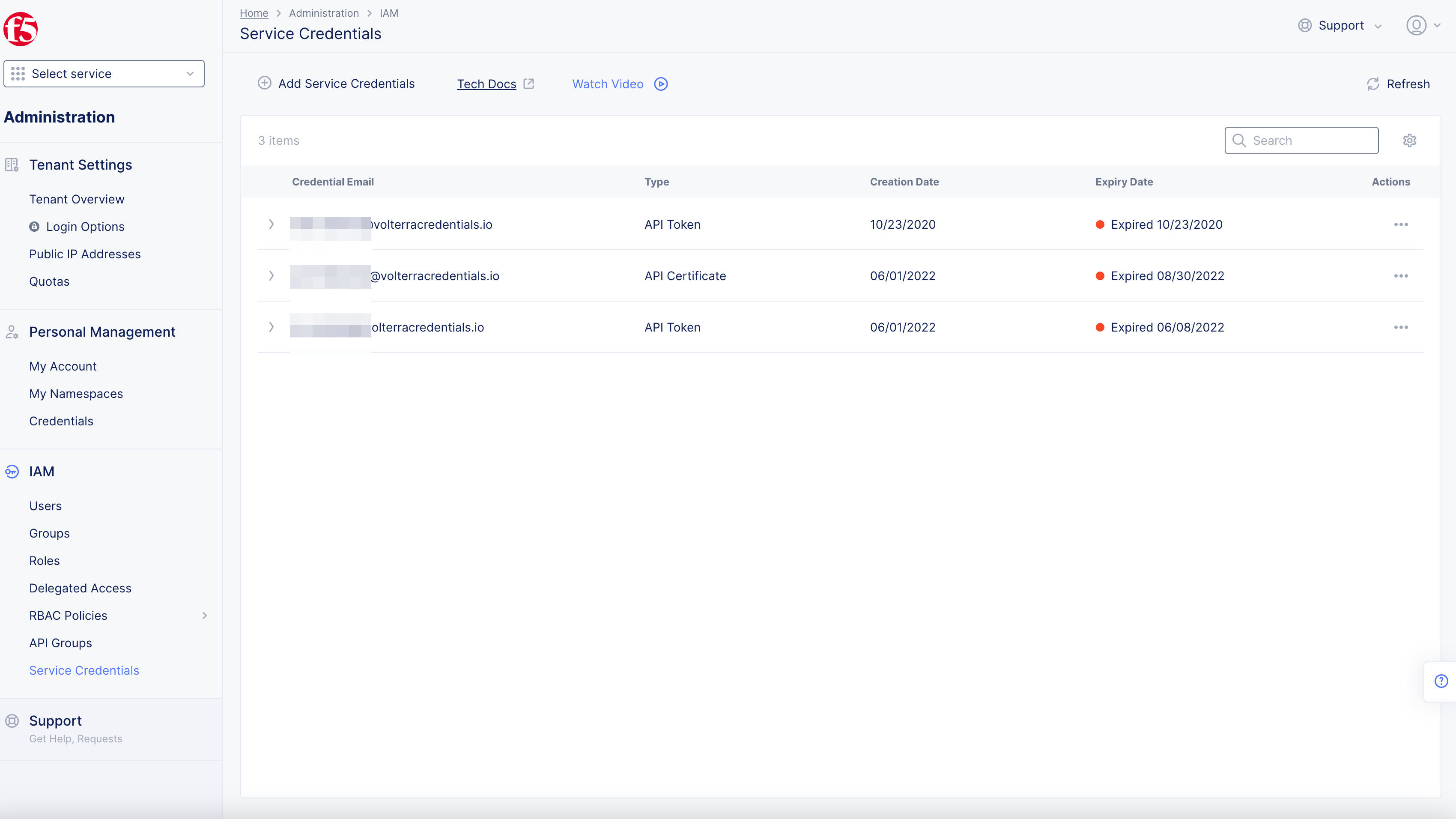
Figure: Credentials
Step 2: Setup Credential type.
-
Enter
NameinCredential Emailbox to generate unique email name,name@volterracredentials.io. -
Select
API TokeninCredential typedrop-down menu. -
Select
Expiry datefrom calendar drop-down. -
Optionally select
Assign Service Credential to Group. Select the groups to which you want to add the service credential and then selectAssign to Group.Note: You can also assign service credentials to user groups when you enable SCIM.
-
Optionally: Select
Assign roles and namespacesto open pop-up window.-
Select
Namespacedrop-down option.-
all application namespaces -
shared -
system -
default -
your custom namespace, Example:aatw
-
-
Select
Make Admincheckbox to grant the admin role. -
Select
Roleboxes to select a role from the displayed options.
Note: You can add more roles using the
+ Assign Roles and Namespaces.- Select
Assign rolesbutton.
-
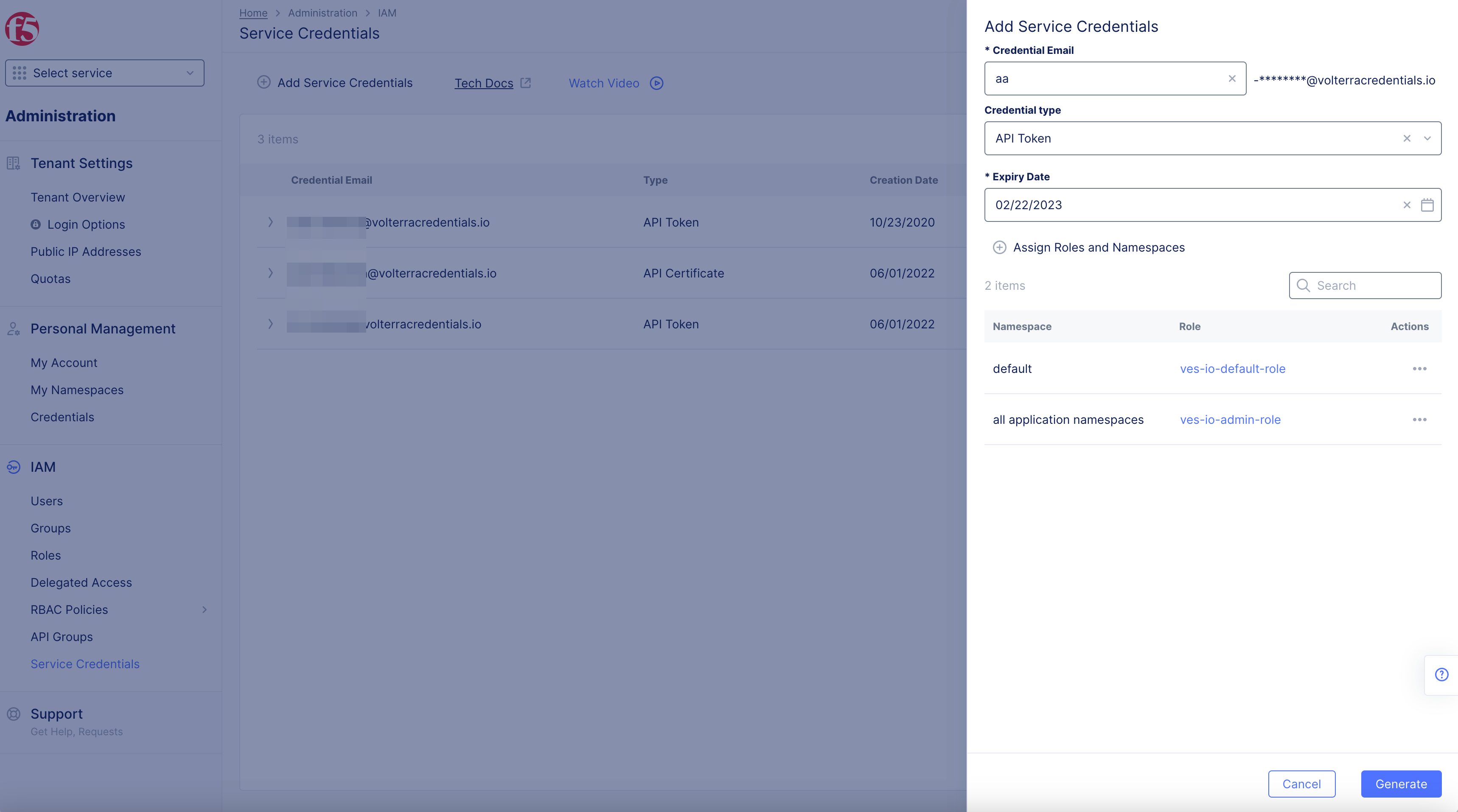
Figure: Create Service API Token
Step 3: Generate and copy Credentials.
- Select
Generatebutton to generate the service API token.

Figure: Create Service API Token
- Select
Copybutton to copy token.
Note: Ensure that you save the copied token for later use.
- Select
Donebutton.
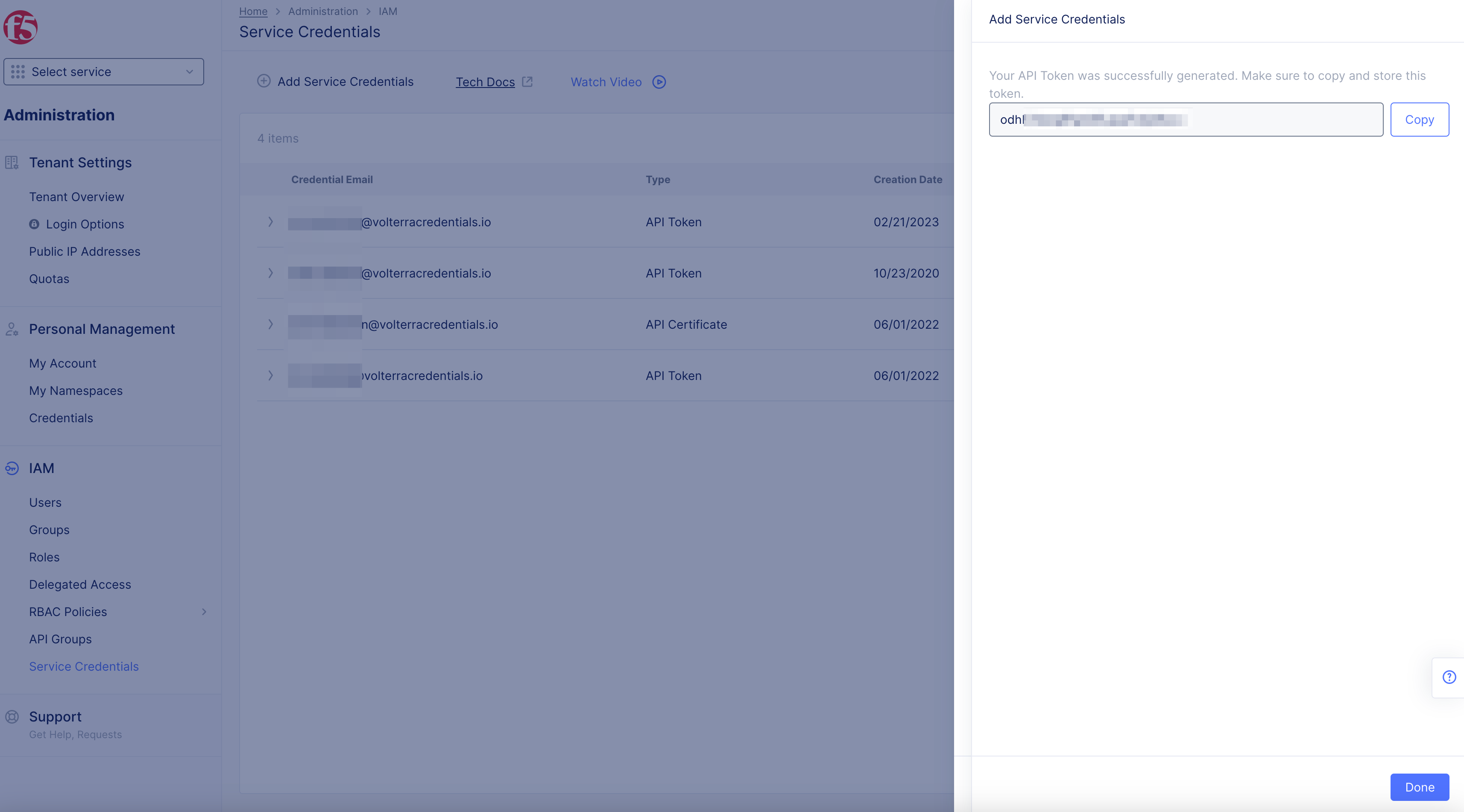
Figure: Copy Service API Token
Revoke Service Credentials
You can force credentials to be expired before the configured expiry time.
Step 1: Open Service Credentials in F5® Distributed Cloud Console.
- Open
F5® Distributed Cloud Consolehomepage, selectAdministrationbox.
Note: Homepage is role based, and your homepage may look different due to your role customization. Visit [Homepage Customization] to adjust your homepage.

Figure: Homepage
- Select
IAM> selectService Credentials> select+ Add Service Credentials.
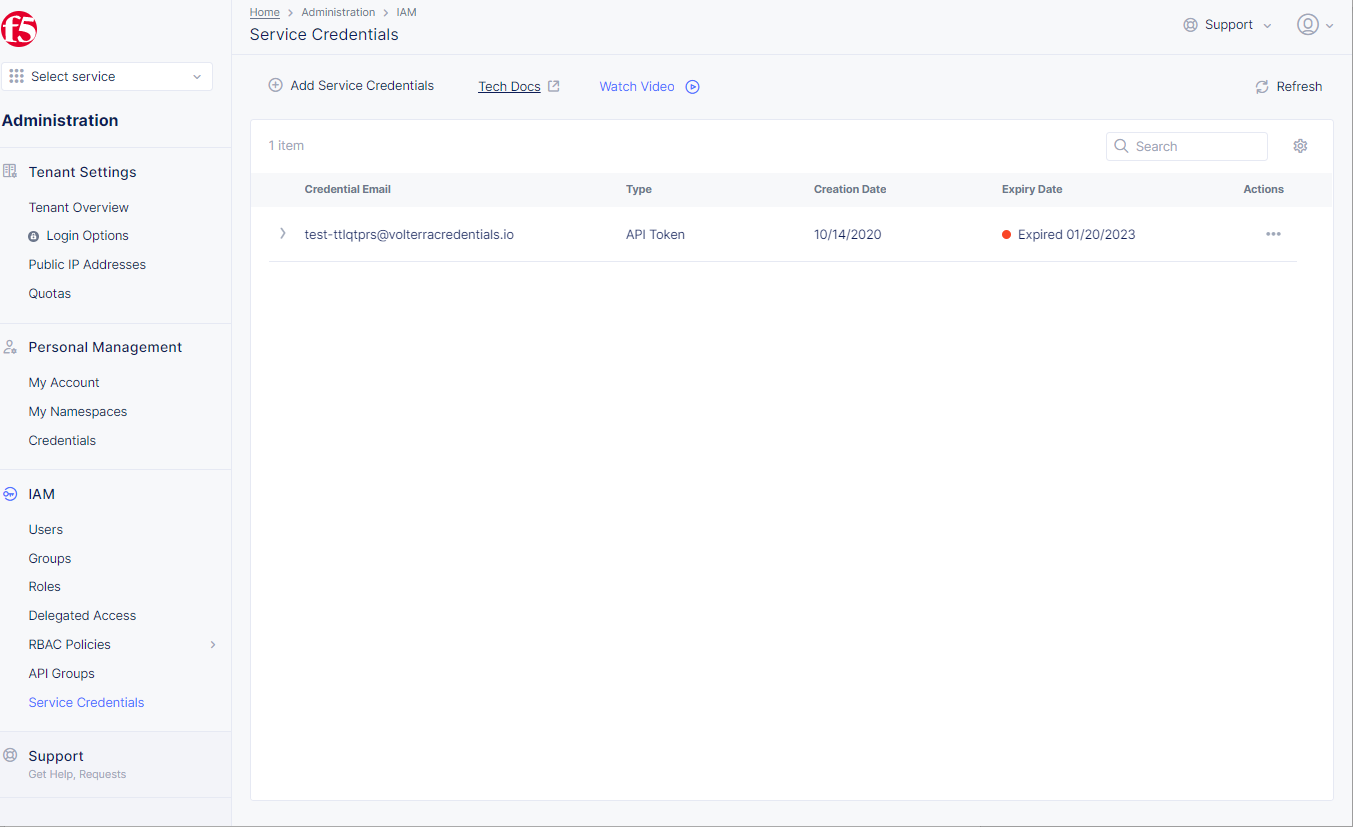
Figure: Credentials
Step 2: Perform revoke operation for an existing service credential object.
-
API Token: Select...inActionscolumn, selectForce Expiryto revokeAPI Token. -
API Certificate: Select...inActionscolumn, selectDeleteto revokeAPI Certificate. -
vK8s KubeConfig Credential: Select...inActionscolumn, selectDeleteto revokevK8s KubeConfig Credential.
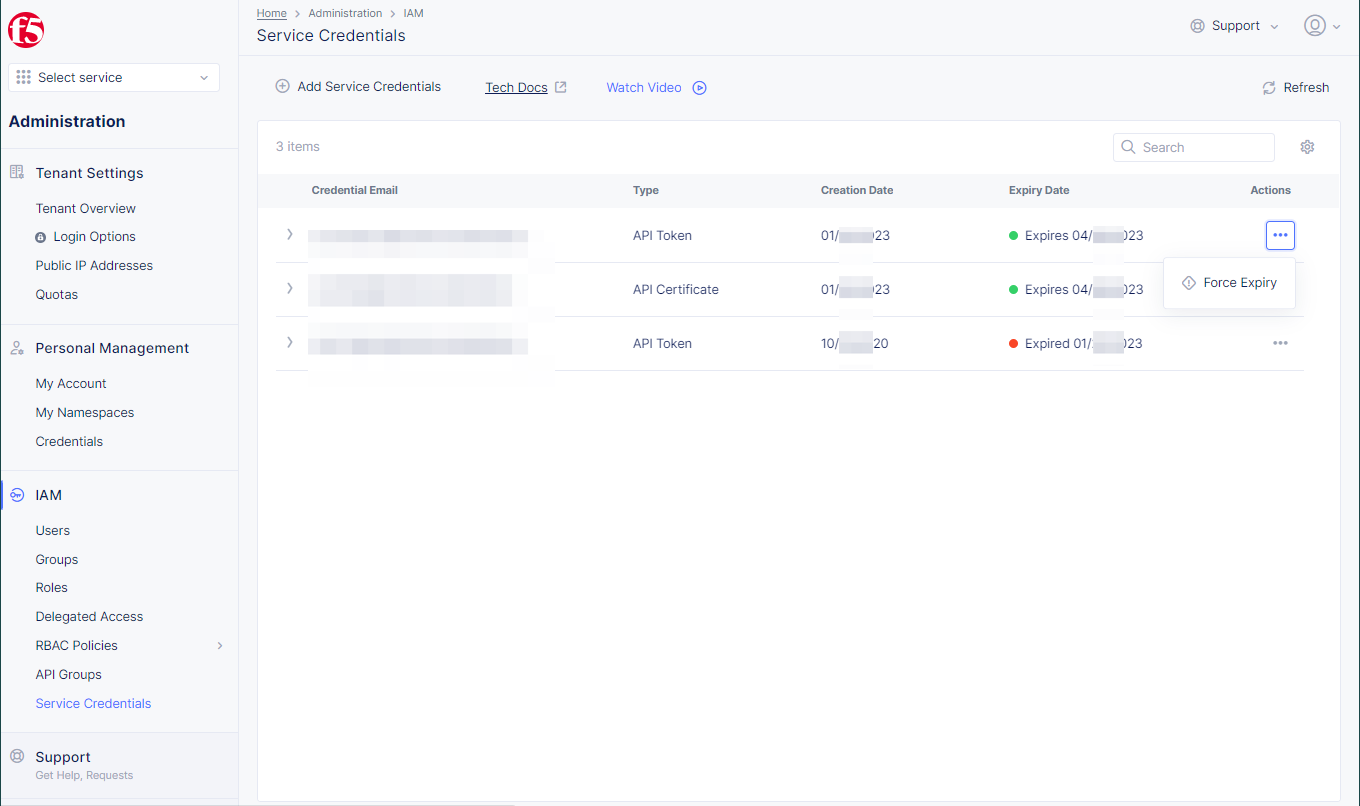
Figure: API Token Force Expiry Option
Step 3: Complete revoke operation.
- In case of
API Token, selectForce Expiryin the confirmation window to cause API credential object expiry.
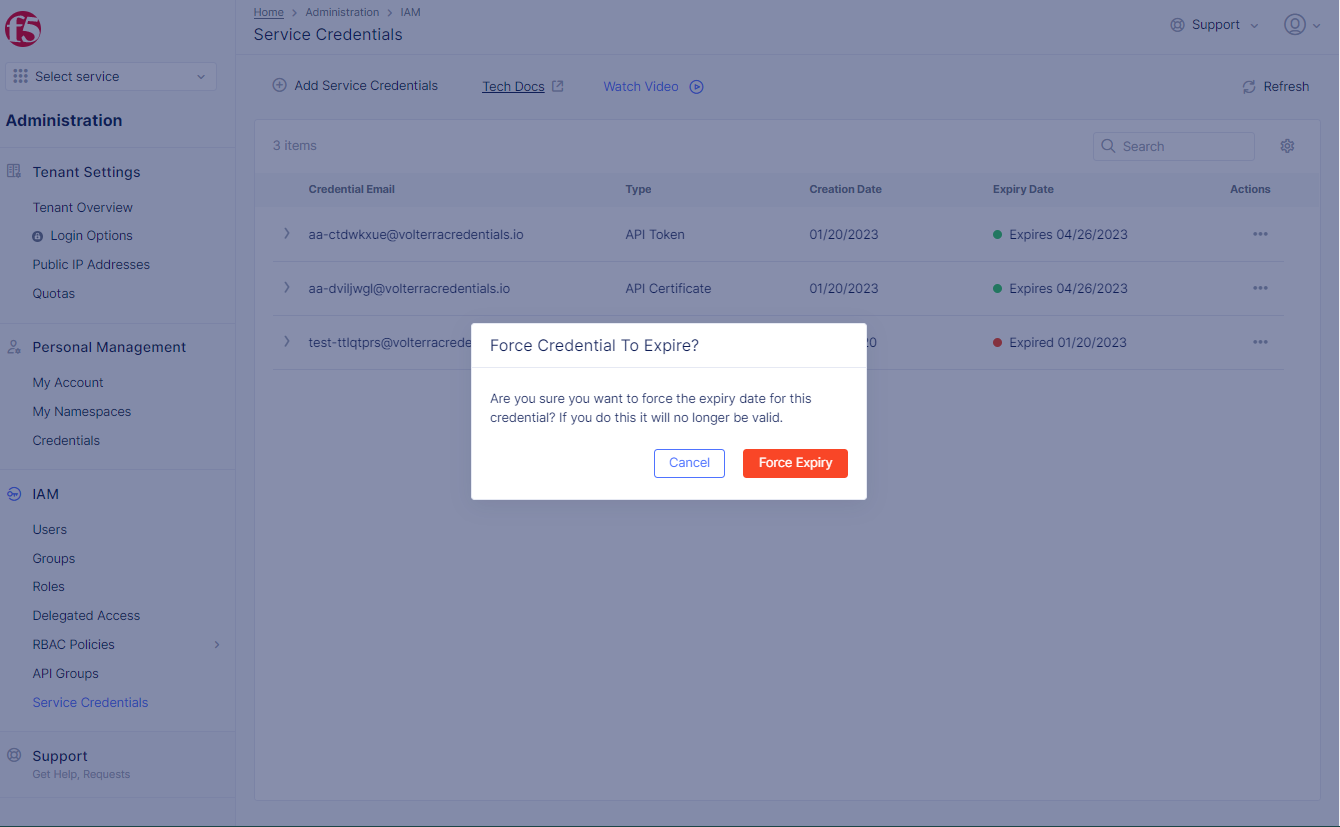
Figure: API Token Force Expiry Confirmation
Note: You can renew or delete an expired credential. For instructions, see Update Service Credentials.
- In case of API certificates or vK8s KubeConfigs, select
Deletein the confirmation window. This forces the expiry for the object and also deletes it from the F5® Distributed Cloud Console.
Update Service Credentials
You can perform the the following updates to your existing API Token and API Certificate service credentials.
Note: You can revoke but not update K8s Global KubeConfig service credentials. For instructions, see Revoke Service Credentials.
Edit a Service Credential
- From the
Administrationnavigation panel, selectIAM > Service Credentials. - From the Actions column, select the Action menu
...next to the credential you want to edit and then selectEdit. - Make updates to
Expiry Date, assigned groups, or assigned roles and namespaces and then clickSave Changes.
Renew an Expired Service Credential
- From the
Administrationnavigation panel, selectIAM > Service Credentials. - From the Actions column, select the Action menu
...next to the credential you want to renew and then selectRenew. - Enter a new
Expiry Dateand selectRenew Credentialto confirm.
Delete an Expired Service Credential
- From the
Administrationnavigation panel, selectIAM > Service Credentials. - From the Actions column, select the Action menu
...next to the credential you want to delete and then selectDelete.Note: If the service credential is not expired, you can first revoke and then delete it.
- Select
Deleteto confirm.
Note: You can use the API to delete multiple service credentials at the same time. See your Distributed Cloud API documentation for information.
Concepts
On this page:
- Objective
- Prerequisites
- My Credentials
- Generate API Certificate for My Credentials
- Generate Kubeconfig for My Credentials
- Generate API Tokens for My Credentials
- Revoke API Credentials for My Credentials
- Service Credentials
- Generate API Certificate for Service Credentials
- Generate Kubeconfig for Service Credentials
- Generate API Token for Service Credentials
- Revoke Service Credentials
- Update Service Credentials
- Concepts