Create Cloud Credentials
Objective
This guide provides instructions on how to create cloud API credentials using the guided wizards in F5® Distributed Cloud Console.
Cloud credentials are used to access services provided by AWS, Azure, and GCP. The credentials enable you to create, read, update, or delete objects needed to deploy and manage your applications in public cloud environments via F5 Distributed Cloud Services automation.
Prerequisites
-
F5® Distributed Cloud Account is required. In case you do not have an account, see Getting Started with Console.
-
Public cloud account with credentials, tenant definitions, and certificates previously created. Refer to the required permissions to create cloud resources in the Cloud Credentials Reference guides. These guides also provide instructions to create the roles and associated service accounts using the cloud formation templates.
Configuration
Perform the steps provided in the following chapters to create cloud credentials for various supported cloud providers.
Add Cloud Credentials
Perform the following steps to start creating cloud credentials object:
Step 1: Navigate to the Cloud Credentials page.
-
Select the
Multi-Cloud Network Connectworkspace. -
Navigate to
Manage>Site Management>Cloud Credentials.
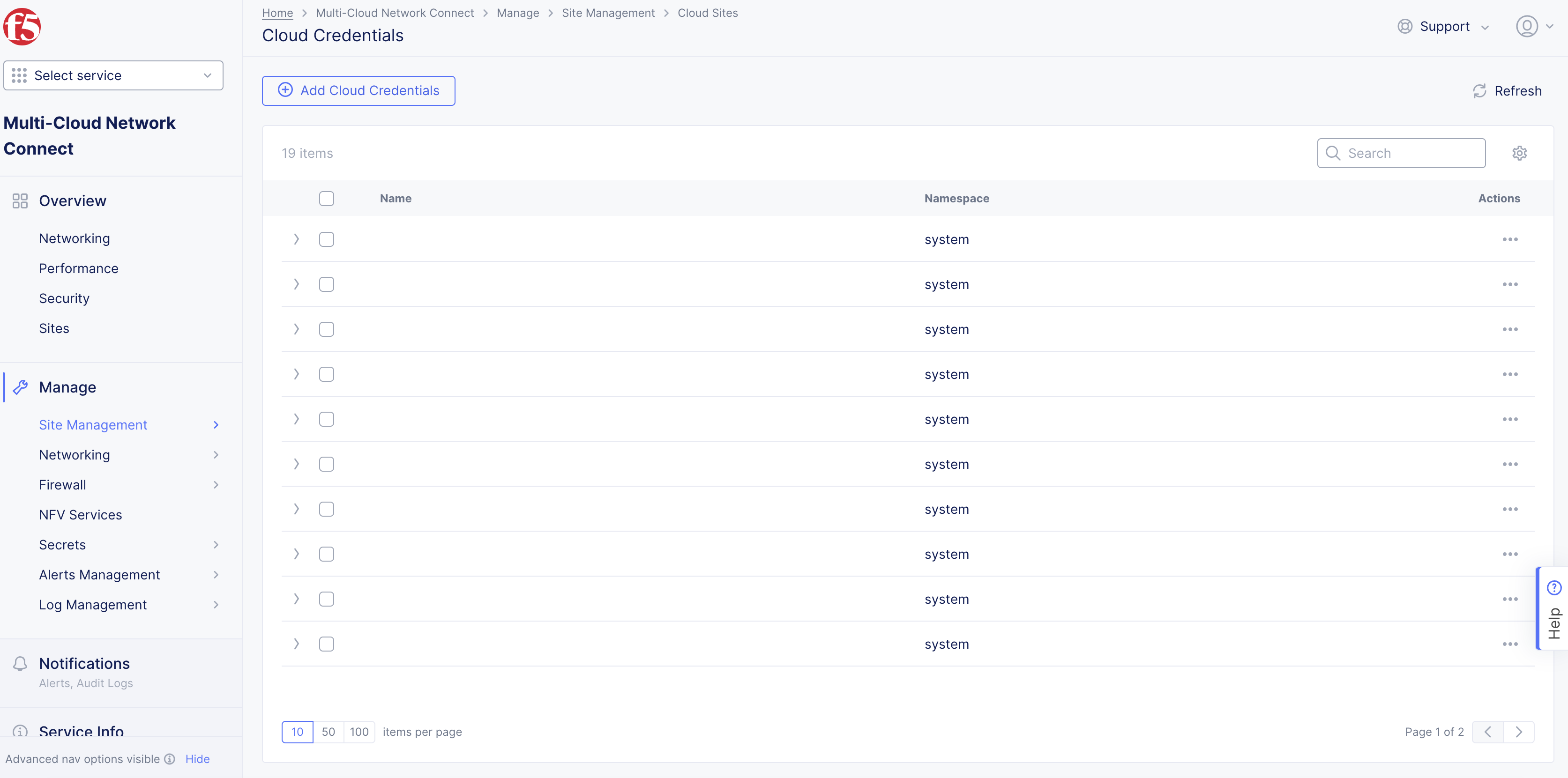
Figure Cloud Credentials Page
Step 2: Start creating cloud credentials.
-
Select
Add Cloud Credentials. -
Enter a name for the credential you are creating.
-
Optionally, add labels and a description to this entry.
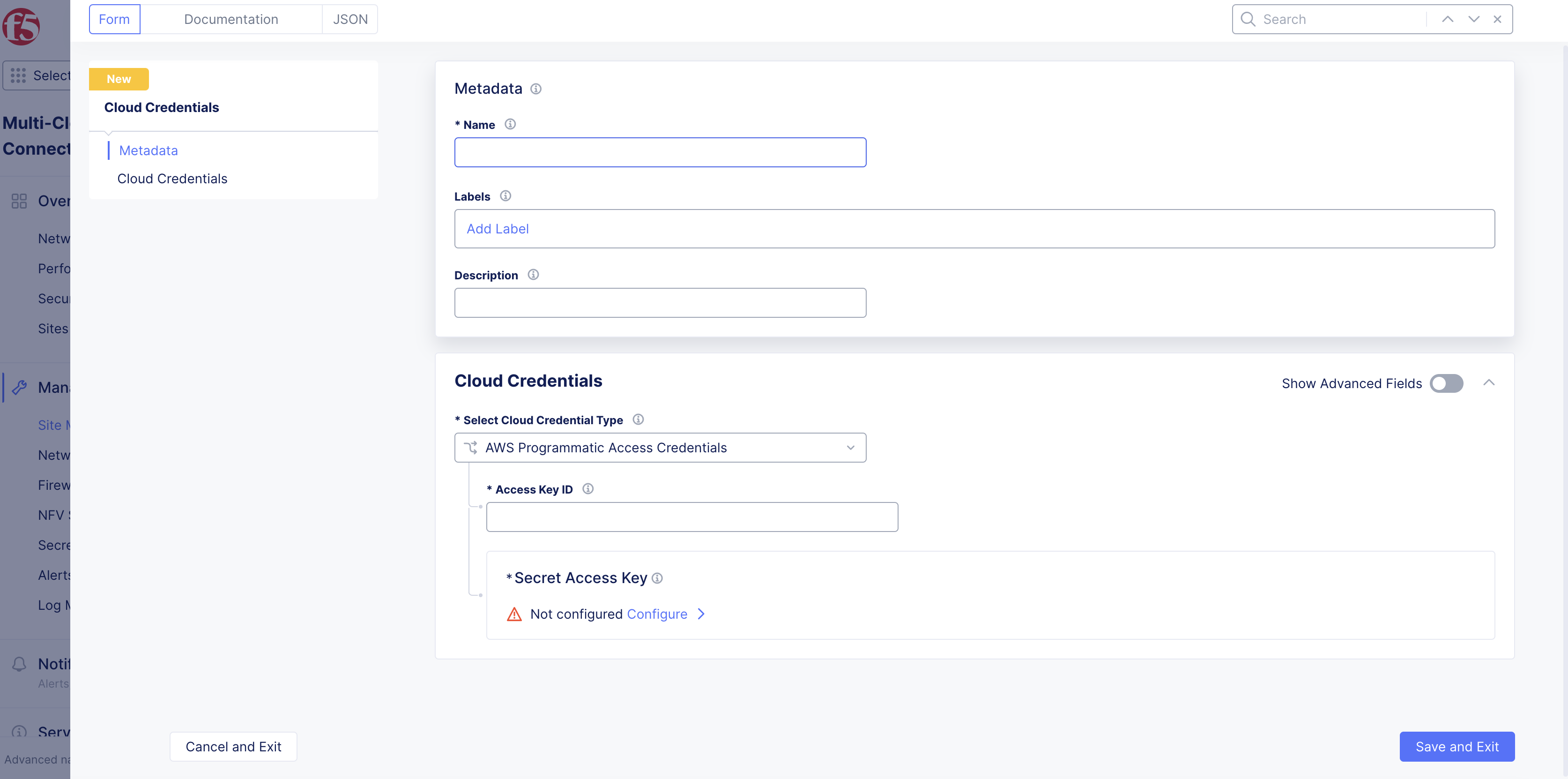
Figure: Cloud Credentials Metadata
Step 3: Select cloud credential type.
Select a cloud credential type from the drop-down menu:
AWS Programmatic Access CredentialsAWS Assume RoleAzure Credential Client CertificateAzure Client Secret for Service PrincipalGCP Credentials
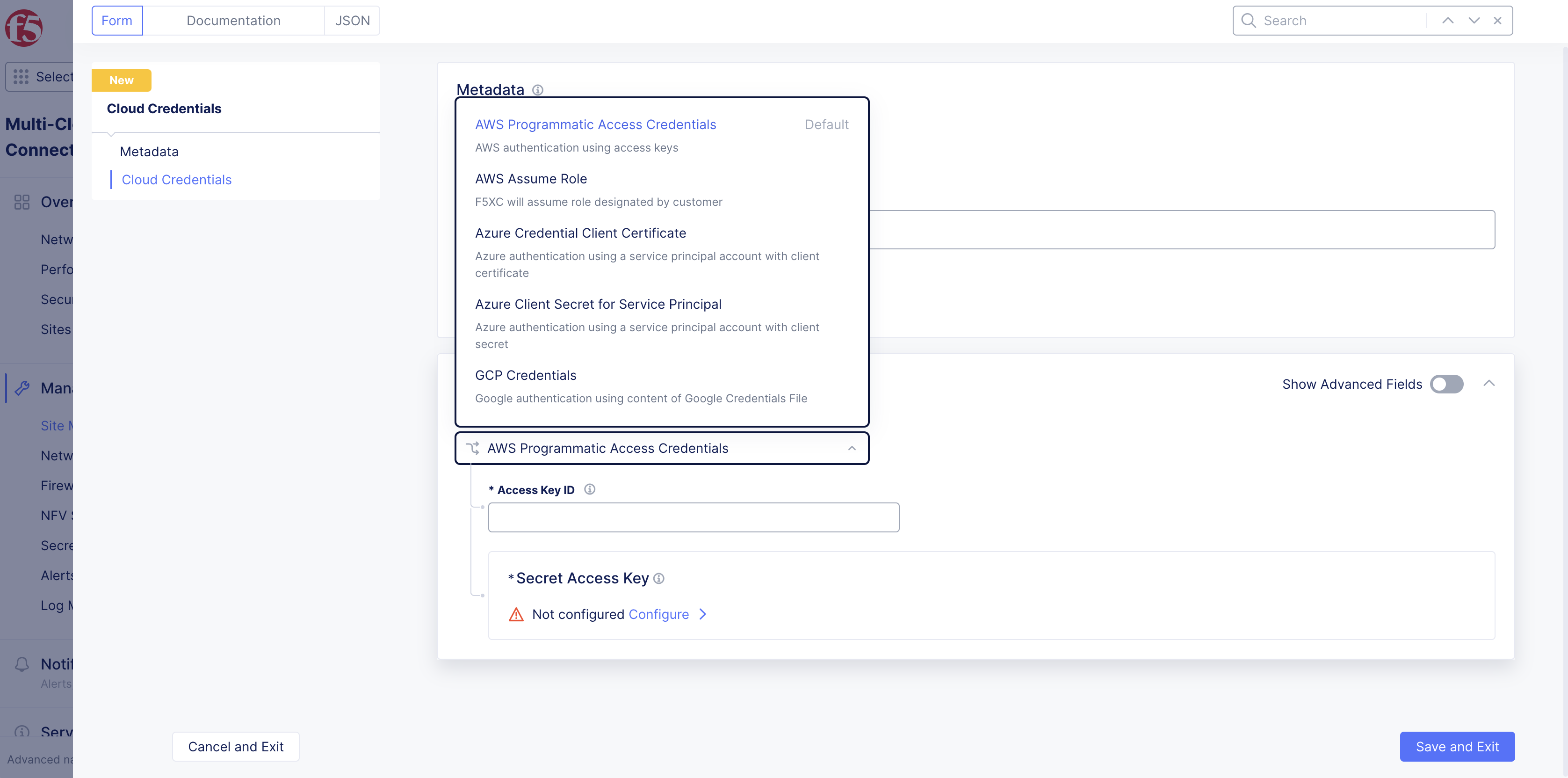
Figure: Cloud Credential Types
Configure Credentials
AWS Programmable Access Credentials
Perform the following steps for AWS programmable access credentials:
Note: Temporary security credentials, such as credentials generated using AWS STS, are not supported.
Step 1: Obtain your access key ID and secret from AWS.
Retrieve your access key ID and secret you intend to use for accessing AWS API services from your AWS Management Console IAM Dashboard. See AWS Identity and Access Management Documentation for more information.
Step 2: Set the access key and configure secret.
-
From the
Select Cloud Credential Typemenu, selectAWS Programmable Access Credentials. -
Enter the AWS
Access Key IDthat you retrieved from your AWS account.
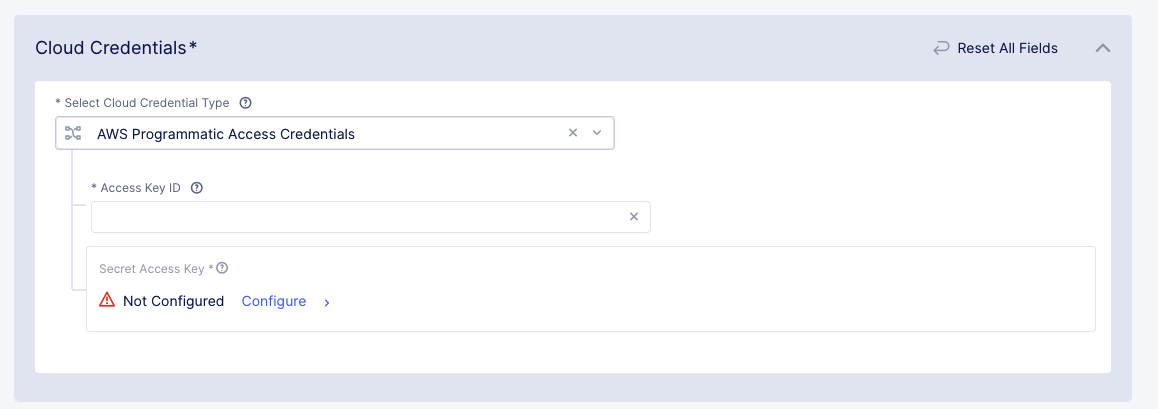
Figure: Secret AWS Access Key Entry
-
Click
Configure. -
Secret information can be one of two types via drop-down:
-
Blindfold Secret: Used for secrets managed by Distributed Cloud Secret Management Service (recommended as this service provides a high level of security). -
Clear Secret: Used for secrets that are not encrypted.
-
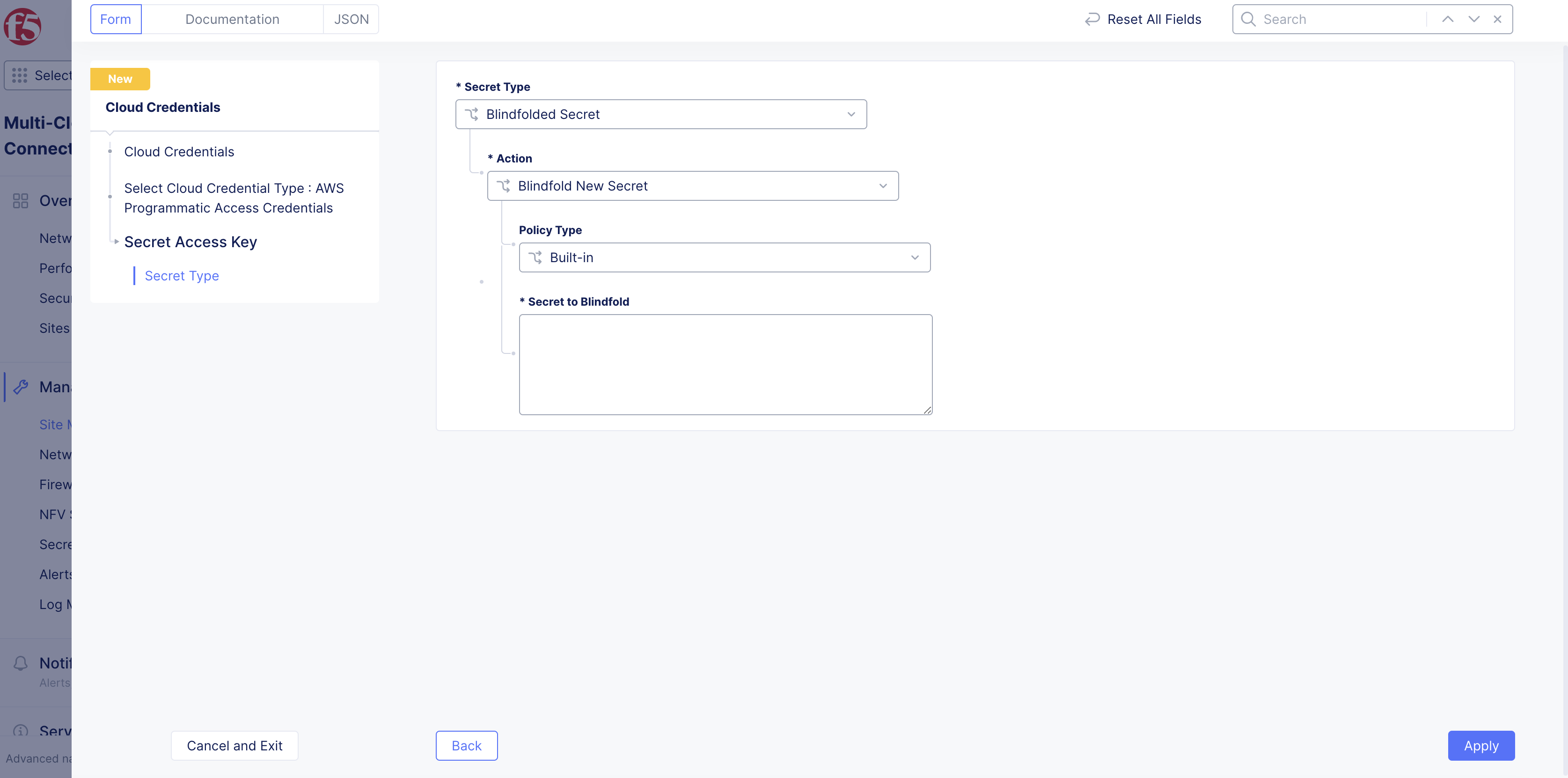
Figure: Configure AWS Access Key
-
Policy information can be one of two types via drop-down:
-
Built-in: Provides a list of Distributed Cloud Services provided set of generic policies. -
Custom: Provides a list of user defined policies which have been defined underManage>Secrets.
-
-
Enter or paste the text or blindfold value of the AWS Secret Key.
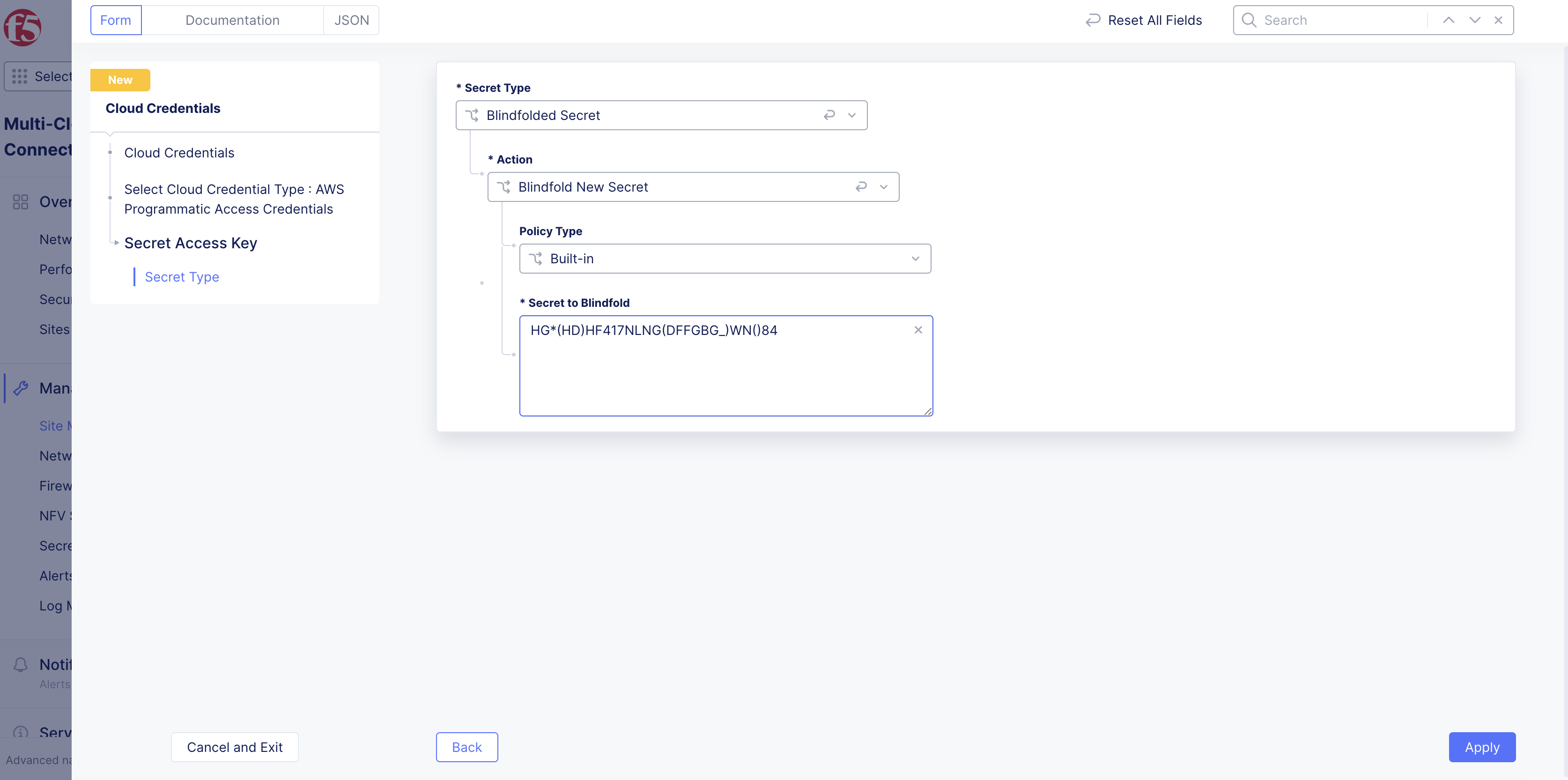
Figure: Secret Access Key Entry
- Click
Applyand then clickSave and Exitto exit the wizard and save your AWS credentials for use with Distributed Cloud Services.
AWS Assume Role
Perform the following steps for configuring AWS Assume Role:
Step 1: Obtain the assume role details.
Create an AWS assume role as described in the AWS VPC Permissions Reference guide and obtain the role_arn value.
Step 2: Configure assume role details in the Console.
-
From the
Select Cloud Credential Typemenu, selectAWS Assume Role. -
Enter ARN value in the
IAM Role ARNfield. Use the value obtained in the previous step. -
Enter a name in the
Role Session Namefield.
Step 3: Optionally, configure advanced settings.
-
Enable
Show Advanced Fields. -
Set a session duration value in seconds in the
Role Session Duration Secondsfield. This will limit the role session to the set duration of time.
Note: The session duration value should be less than or equal to the maximum session duration configured in AWS Console.
-
Click on the
Add Labellink in theRole Session Tagsfield and add labels per your needs. -
Click
Apply.
Step 4: Complete creating the cloud credentials.
Click Save and Exit to complete creating the cloud credentials of type AWS Assume Role.
Azure Credential Client Certificate
Perform the following steps for configuring Azure Credential Client Certificate for Service Principal:
Step 1: Obtain the authentication details from Azure.
Retrieve your Client ID, Subscription ID, Tenant ID, Certificate and Certificate Password you intend to use for accessing Azure API services from your Azure Portal. See Azure Key Vault Reference and Azure Key Vault Quick Start.
Step 2: Enter the identities and configure secret.
-
From the
Select Cloud Credential Typemenu, selectAzure Credential Client Certificate. -
Enter the Azure
Client ID,Subscription ID, andTenant IDthat you retrieved from your Azure account. -
Enter the
URL for Client Certificatein the following format:string:///<base64 encoded string of the certificate>.
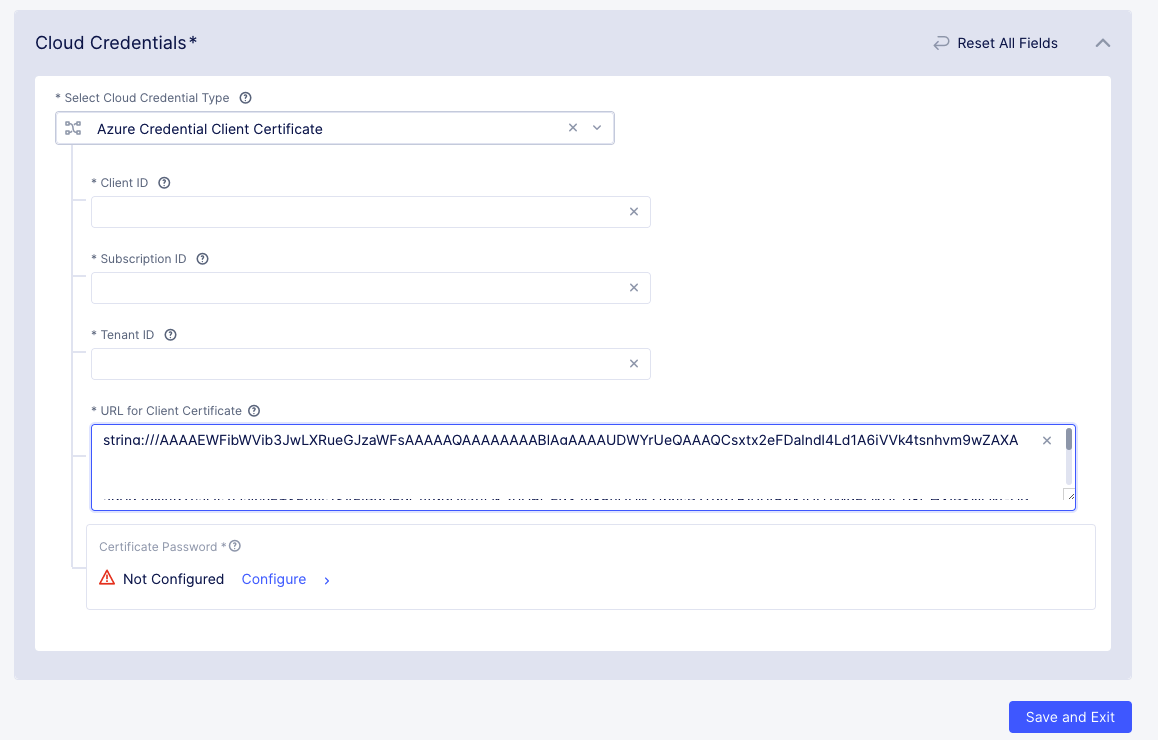
Figure: Entries for Azure Client Secret
-
Click the
Configurelink to enter the certificate password you retrieved from Azure Portal and enter in same manner as was done for the AWS Access Secret Key in the AWS Programmable Access Credentials chapter using either theClear SecretorBlindfold Secretoptions. -
Click
Applyand then clickSave and Exit.
Azure Client Secret for Service Principal Credentials
Perform the following steps to configure Azure client secret for service principal credentials:
Step 1: Obtain the authentication details from Azure.
- Retrieve your Client ID, Subscription ID, Tenant ID, and Client Secret to use for accessing Azure API services from your Azure Portal. See Azure Key Vault Reference and Azure Key Vault Quick Start.
Step 2: Enter the identities and configure secret.
-
From the
Select Cloud Credential Typemenu, selectAzure Client Secret for Service Principal Credentials. -
Enter the
Azure Client ID,Subscription ID, andTenant IDthat you retrieved from your Azure account.
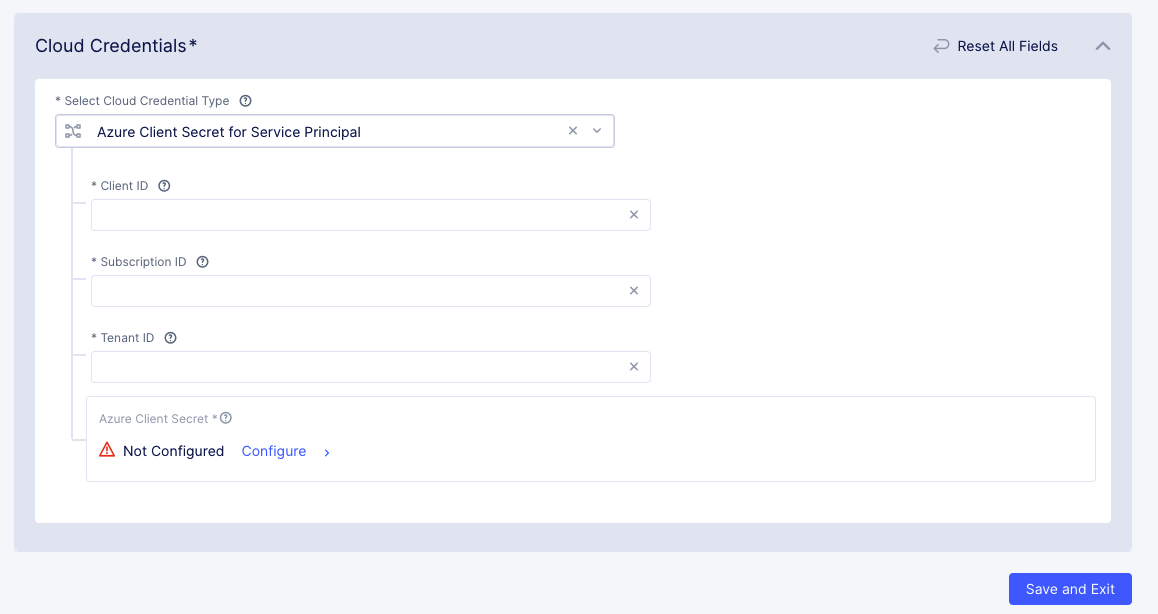
Figure: Entries for Azure Client Secret
-
Click the
Configurelink to enter the Secret Key you retrieved from the Azure Portal and enter in same manner as was done for the AWS Secret Key in the AWS Programmable Access Credentials chapter using either theClear SecretorBlindfold Secretoptions. -
Click
Applyand then clickSave and Exitto complete creating Azure credentials.
GCP Credentials
Perform the following steps to configure GCP credentials:
Step 1: Obtain the authentication details from GCP.
- Retrieve the service account key for your project from GCP. For information on how to generate a service account key, see the Create and delete service account keys guide.
Step 2: Configure the secret with the service account key.
-
From the
Select Cloud Credential Typemenu, selectGCP Credentials. -
Click
Configure.
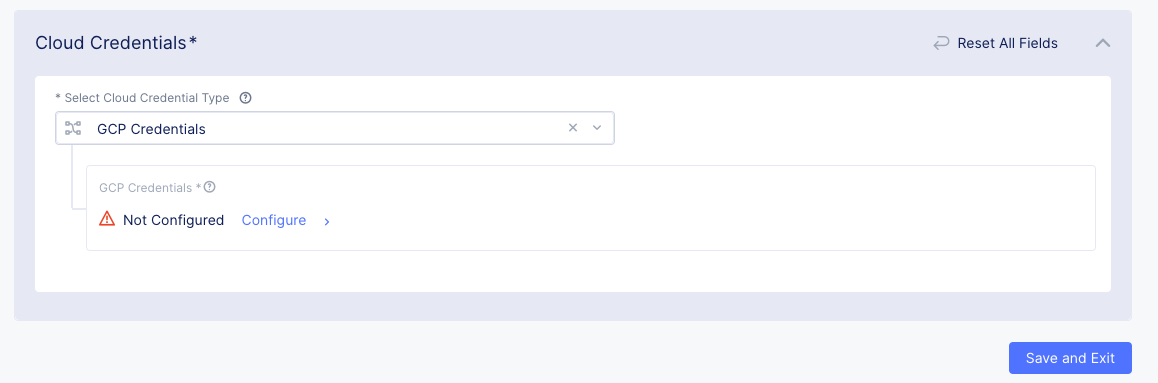
Figure: GCP Credentials
-
Enter the service account key you retrieved from the GCP and enter in same manner as was done for the AWS Secret Key in the AWS Programmable Access Credentials chapter using either the
Clear SecretorBlindfold Secretoptions. -
Click
Applyand then clickSave and Exitto complete creating GCP cloud credentials.