Create Cloud Connects
Objective
This guide provides instructions on how to create a Cloud Connect using a guided wizard in F5® Distributed Cloud Console (Console). Cloud Connect is a cloud-neutral approach to enable you to attach your private cloud network onto F5 Distributed Cloud Platform's cloud customer edge (CE) sites.
A transit gateway (TGW) acts as a regional virtual router for traffic flowing between virtual private clouds (VPCs) and on-premises networks.
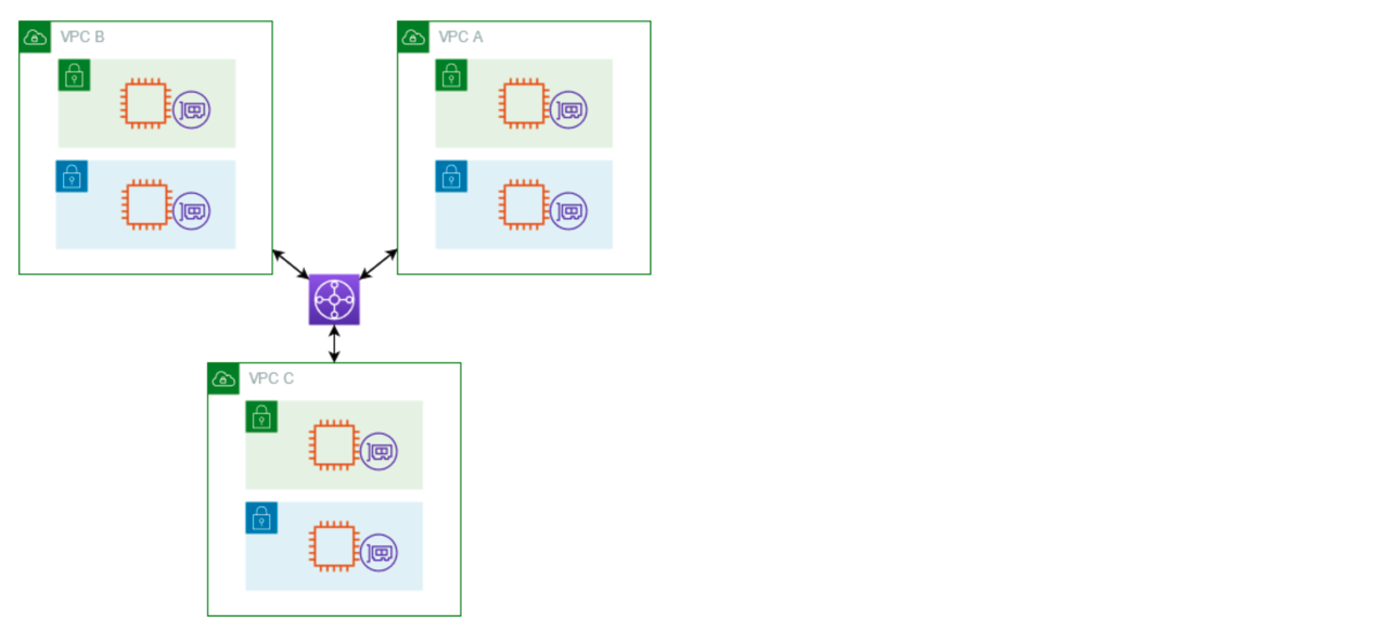
Figure: Cloud Connects Configuration
Prerequisites
-
F5 Distributed Cloud Services account. If you do not have an account, see Getting Started with Console.
-
An existing AWS TGW site with Hub, Spoke, and Services route tables.
-
Transit Gateway must be in
Availablestate. -
Cloud credentials with the following permissions are required to create a Cloud Connect:
| AWS Elastic Compute Cloud (EC2) Permissions | AWS Resource Access Manager (RAM) Permissions |
|---|---|
| ec2:CreateTransitGatewayVpcAttachment | ram:GetResourceShareInvitations |
| ec2:DeleteTransitGatewayVpcAttachment | ram:AcceptResourceShareInvitation |
| ec2:ModifyTransitGatewayVpcAttachment | |
| ec2:AcceptTransitGatewayVpcAttachment | |
| ec2:DescribeTransitGatewayVpcAttachments | |
| ec2:DescribeVpcs | |
| ec2:DescribeSubnets | |
| ec2:CreateRoute | |
| ec2:DeleteRoute | |
| ec2:DescribeRouteTables | |
| ec2:DescribeNetworkInterfaces |
Configuration
Create a Cloud Connect
Perform the following steps to create a Cloud Connect:
Step 1: Navigate to the Cloud Connects page.
- Log into Console and select the
Multi-Cloud Network Connectservice.
Figure: Console Homepage
- Click
Manage>Connectors>Cloud Connects.
Figure: Cloud Connects
Step 2: Create a Cloud Connect.
- Click
Add Cloud Connect.
- Select a cloud provider and site type from the
Providerdrop-down menu. The choices are detailed below.
AWS TGW Site
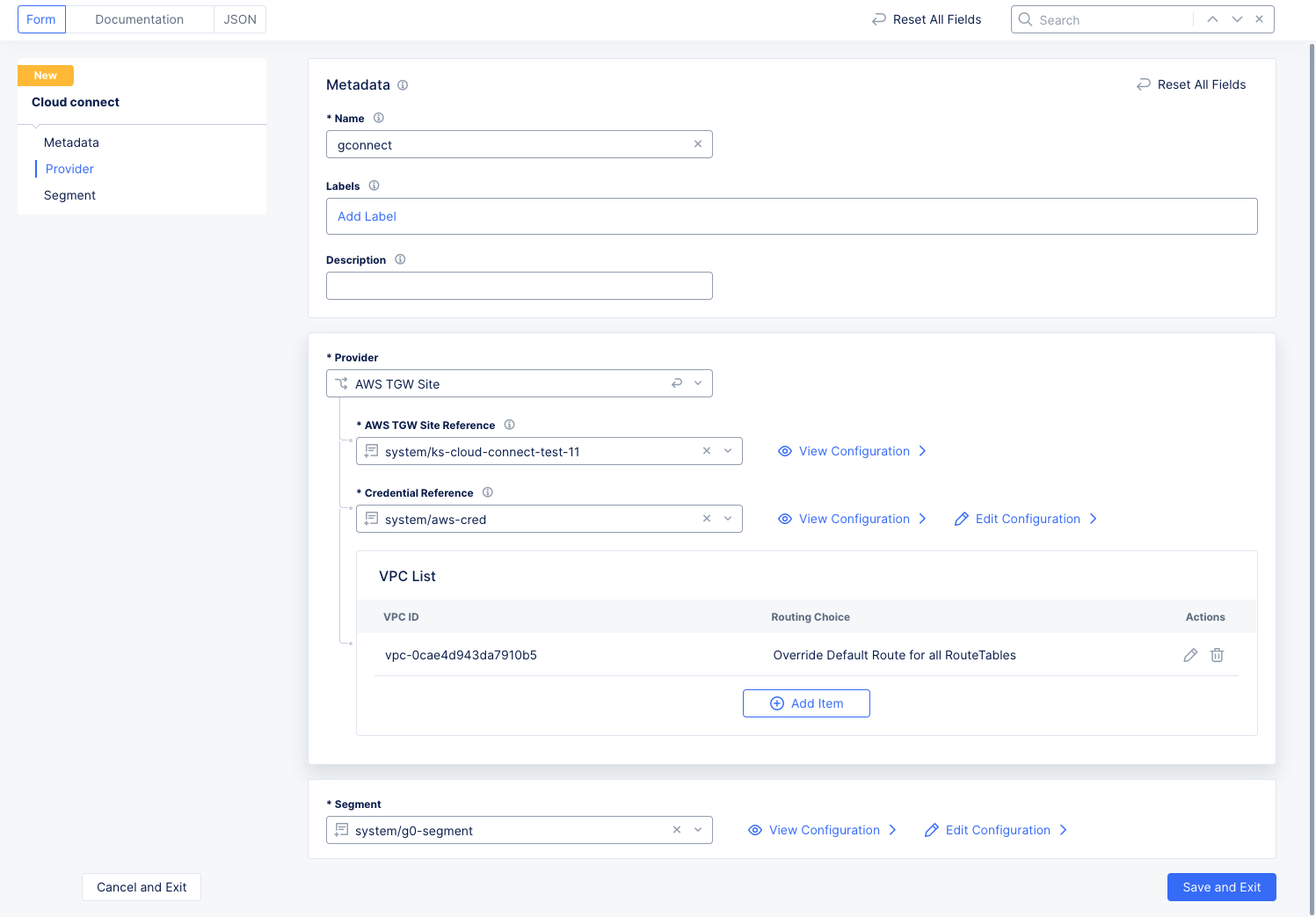
Figure: New AWS Cloud Connect
-
Select a site reference from the
AWS TGW Site Referencedrop-down menu. Once you've made a selection, you can clickView Configurationto verify the configuration details. -
Select a cloud credential from the
Credential Referencedrop-down menu to deploy resources, or selectAdd Itembelow the list to create a new one. Once you've made a selection, you can clickView ConfigurationorEdit Configurationto verify the configuration details or make changes. -
Click
Add Itemto create for each VPC Attachment.- Enter a
VPC IDof the VPC to be attached. - Select which traffic should be routed toward the customer edge (CE) from the
Routing Choicedrop-down menu.Manual: You manage routing.Override Default Route: You select the route tables. Next, select theOverride Default Route Choice. If you chooseSelective Route Tables for AWS, then you must also add one or moreRoute table IDs.Advertise Custom CIDRs- User specifies CIDRs routes toward the CE to be installed for this subnet. Next, clickAdd Itemfor each route table in your list. For each route table, select aRoute table IDand then enter one or moreStatic Routesusing theAdd Itembutton.
- Enter a
Note:
- The AWS TGW CE site must be in
onlineandavailablestate.- The cloud credentials you select must have the listed permissions attached to it.
- The VPC will be discovered from the site region using the selected credential.
- The maximum number of supported VPCs is 128 for each Cloud Connect.
- The VPC must have a t least one subnet.
- Editing a selected credential and AWS TGW site is not supported.
Azure VNET Site
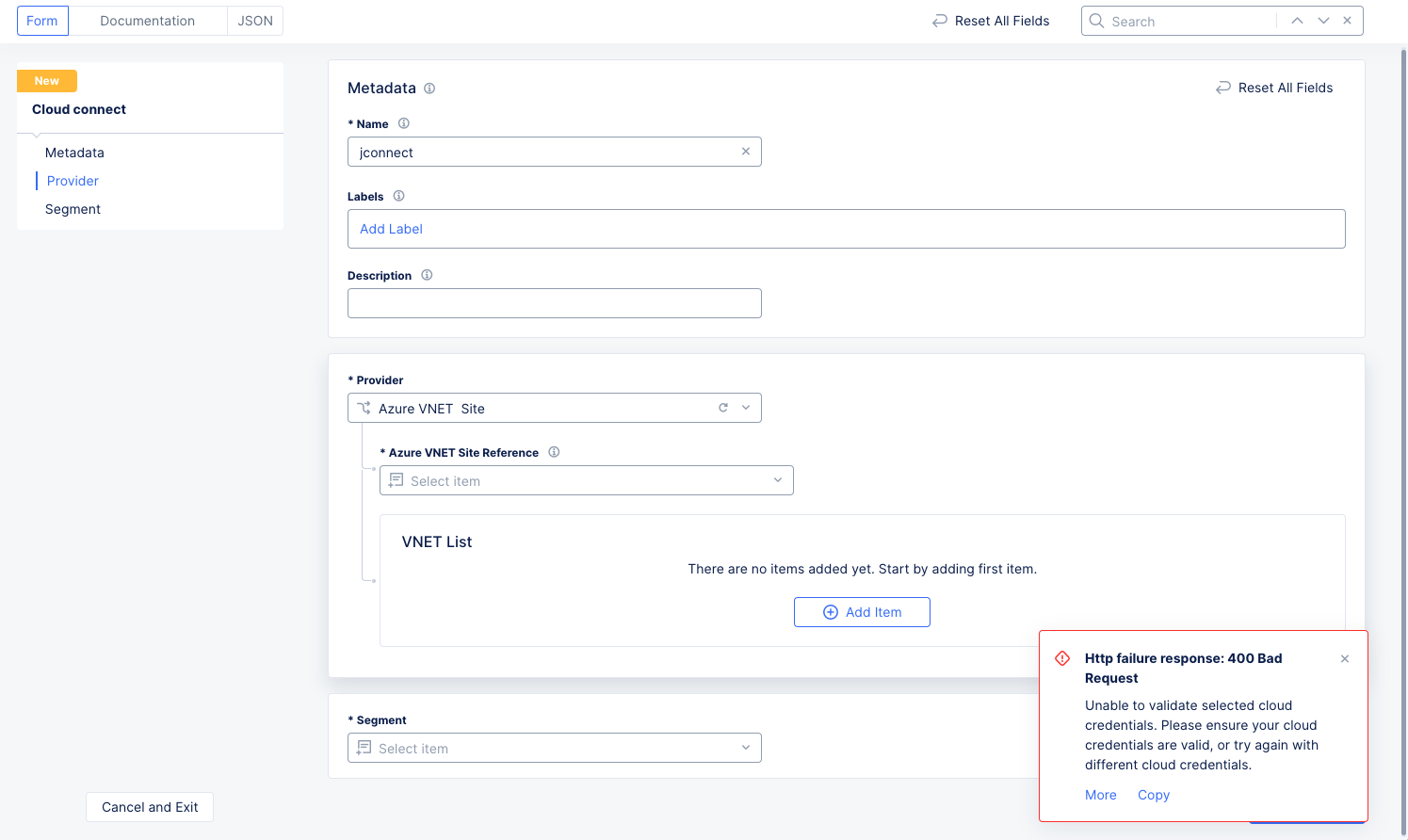
Figure: New VNET Cloud Connect
-
Select a site reference from the
Azure VNET Site Referencedrop-down menu. Once you've made a selection, you can clickView Configurationto verify the configuration details. -
Click
Add Itemto create a VNET Attachment.- Enter the Suscription ID of the VPC to be attached.
- Enter a
VNET IDof the VPC to be attached. It should be in this format:/<resource-group-name>/<vnet-name>. - Select which traffic should be routed toward the customer edge (CE) from the
Routing Choicedrop-down menu.Manual: The user to manages routing.Advertise Custom CIDRs: User specifies CIDRs routes toward the CE to be installed for this subnet. Next, clickAdd Itemfor each route table in your list. For each route table, select aRoute table IDand then enter one or moreStatic Routesusing theAdd Itembutton.Override Default Route: User specifiesAll RouteTablesorSelective RouteTables for Azure Site. For the latter, enter one or more Route table IDs.
- Optionally add labels.
Step 3: Select a segment and save .
-
Use the
Segmentdrop-down menu to select an existing segment, or selectAdd Itembelow the selection list to create a new segment. -
Click
Add Cloud Connectto create the Cloud Connect.
Step 4: Verify your Cloud Connect.
- Click
Manage>Connectors>Cloud Connectto see you new Cloud Connect. You may need to click theRefreshbutton to see your new Cloud Connect in the table.
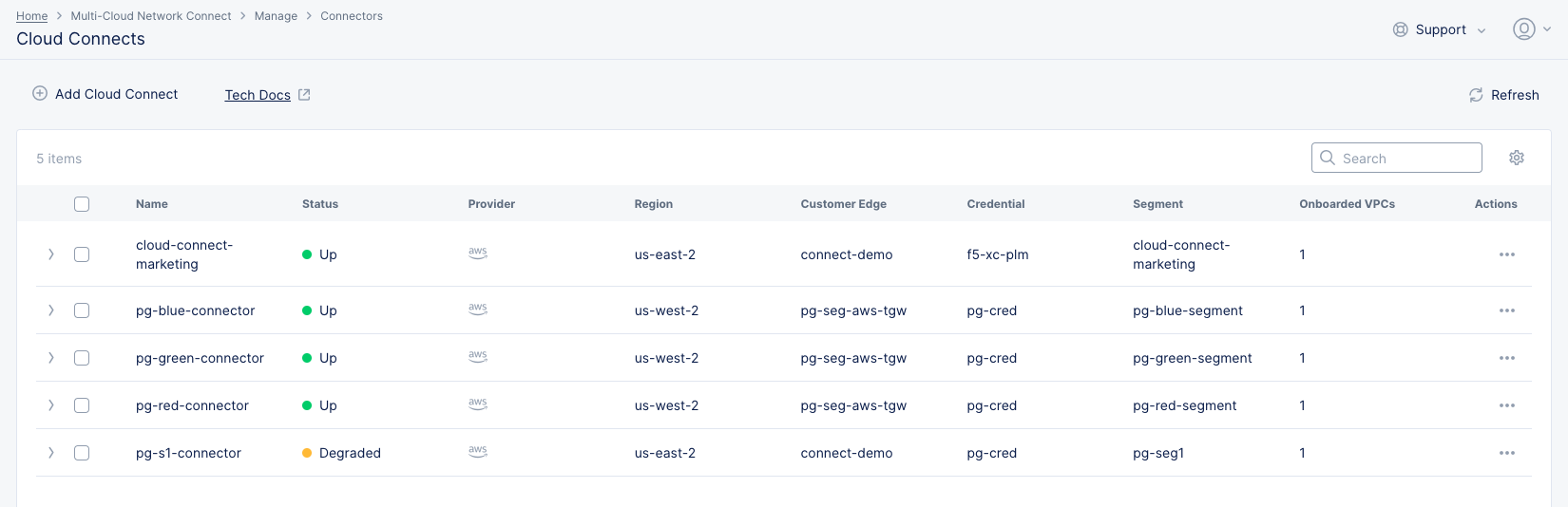
Figure: New AWS Cloud Connect
- Click
...>Show Statusfor your new Cloud Connect and then click theUIDobject.
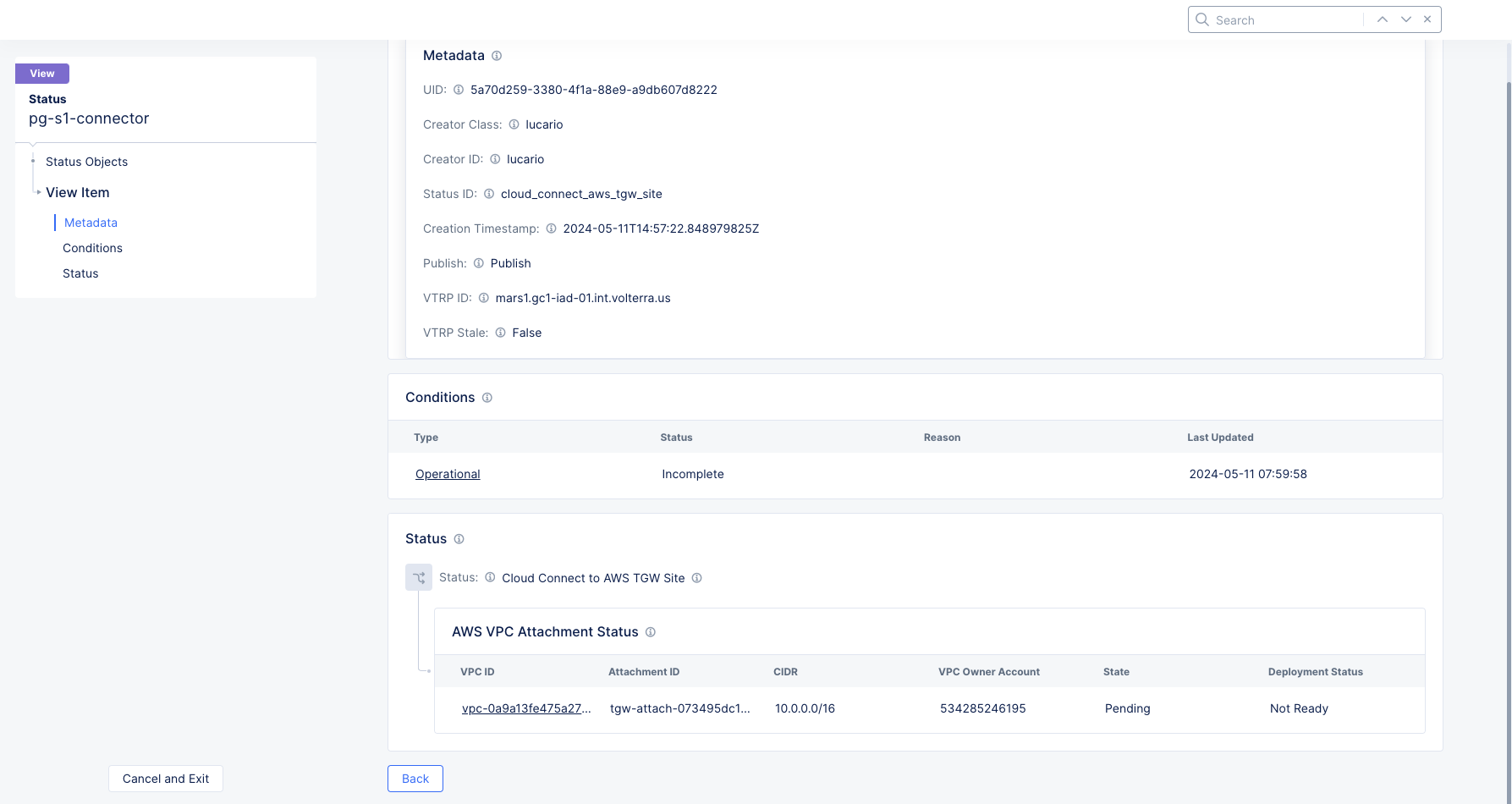
Figure: AWS Cloud Connect Status
- The
Statussection shows the current state of your Cloud Connect. During creation, theStatecolumn will showPending, and theDeployment Statuswill showNot Ready. After a minute or two they will change toAvailableandReady, at which time your Cloud Connect will be available.
Delete a Cloud Connect
Perform the following steps to create a Cloud Connect:
Step 1: Navigate to the Cloud Connects page.
- Log into Console and select the
Multi-Cloud Network Connectservice.

Figure: Console Homepage
- In the
Multi-Cloud Network Connectservice, clickManage>Connectors>Cloud Connects.
Step 2: Delete a Cloud Connect.
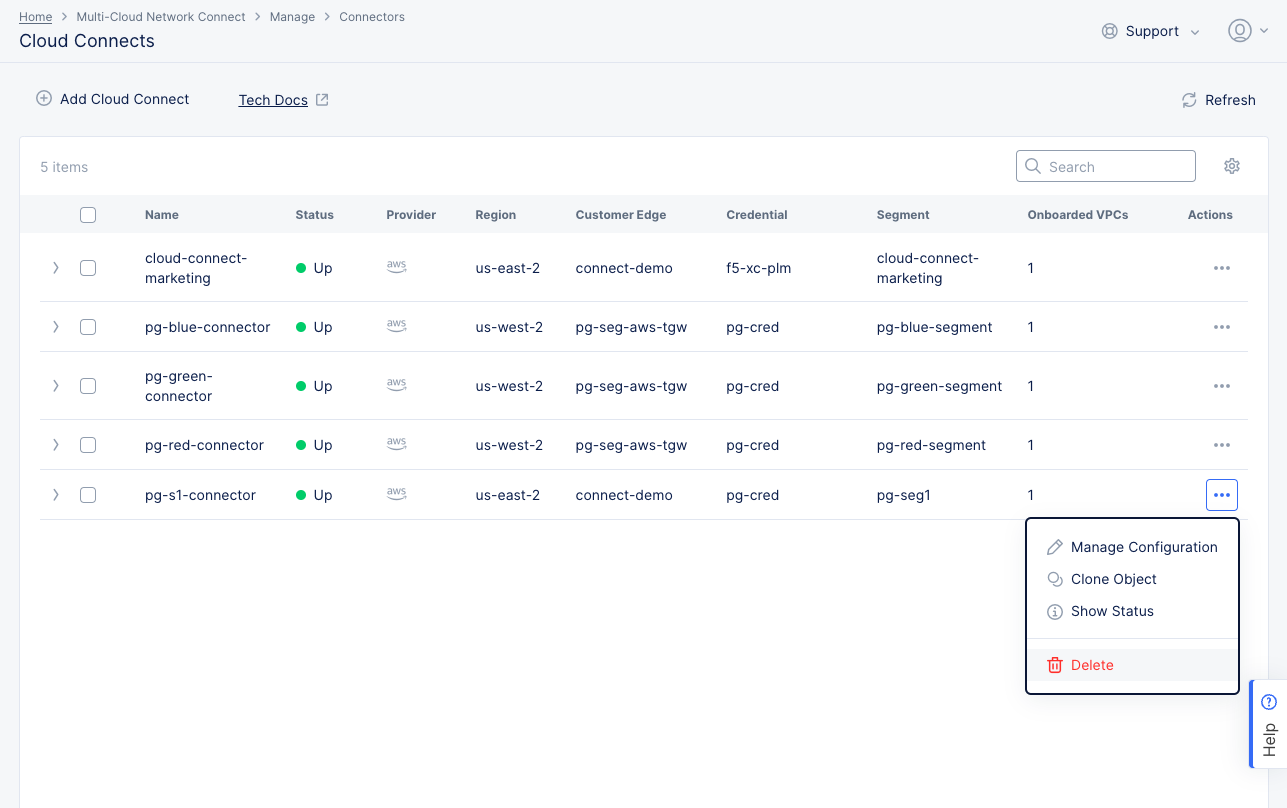
Figure: Cloud Connects
-
Click
...>Deletein theActionscolumn for the Cloud Connect you want to delete. -
Click
Deletein the confirmation pop-up window. -
The
Statuscolumn for your Cloud Connect will change toDegradedduring the deleting process. Once deleted, that Cloud Connect will be removed from the table.
Limitations
-
When you attach a VPC to a transit gateway, any resources in Availability Zones where there is no transit gateway attachment cannot reach the transit gateway. If there is a route to the transit gateway in a subnet route table, traffic is forwarded to the transit gateway only when the transit gateway has an attachment in a subnet in the same Availability Zone.
-
The resources in a VPC attached to a transit gateway cannot access the security groups of a different VPC that is also attached to the same transit gateway.
-
A transit gateway does not support routing between VPCs with identical CIDRs. If you attach a VPC to a transit gateway and its CIDR is identical to the CIDR of another VPC that is already attached to the transit gateway, the routes for the newly attached VPC are not propagated to the transit gateway route table.
-
You cannot create an attachment for a VPC subnet that resides in a Local Zone.
-
You cannot create a transit gateway attachment using IPv6-only subnets.
-
Transit gateway attachment subnets must also support IPv4 addresses.
-
A transit gateway must have at least one VPC attachment before that transit gateway can be added to a route table.