User Behavior Analysis
Objective
This document provides instructions on how to enable User Behavior Analysis (UBA) using the F5® Distributed Cloud Services Artificial Intelligence (AI) and Machine Learning (ML) features. The user behavior analysis covers the following:
-
Clear suspicious behavior - This is based on security events such as the following:
- WAF security events generated by a user
- Login failures
- L7 policy denies
-
Anomalous behavior - This is identified by analyzing behavioral aspects of user activity.
Note: The user in this context is mapped by the requesting IP address.
Using the instructions provided in this document, you can enable the user behavior for your application and monitor the related anomalies and events in the load balancer monitoring.
Prerequisites
Note: If you do not have an account, see Getting Started with Console.
- One or more applications deployed on Distributed Cloud site and services configured.
Note: See App Management for more information. See Site Management for site creation instructions.
Configuration
Configuration Sequence
The following table presents the sequence of activities in enabling the UBA:
| Activity | Description |
|---|---|
| Create App Type | Create app type and configure the user behavior analysis features. |
| Create App Settings | Create the app settings object and associate with the app type. |
| Monitor User Behavior | Monitor the load balancer to check for anomalies detected and reported for user behavior. |
Create App Type
To enable user behavior analysis for your application services, it is required to first enable it for those services using the app type object.
The app type object is created in the shared namespace. The load balancers of that app type in different namespaces need to be assigned with the label of the app type object.
Perform the following to create app type and enable generating the user behavior model.
Step 1: Navigate to the App Types page.
- Select the
Shared Configurationservice. - Navigate to
Security>AI & ML>App Types.
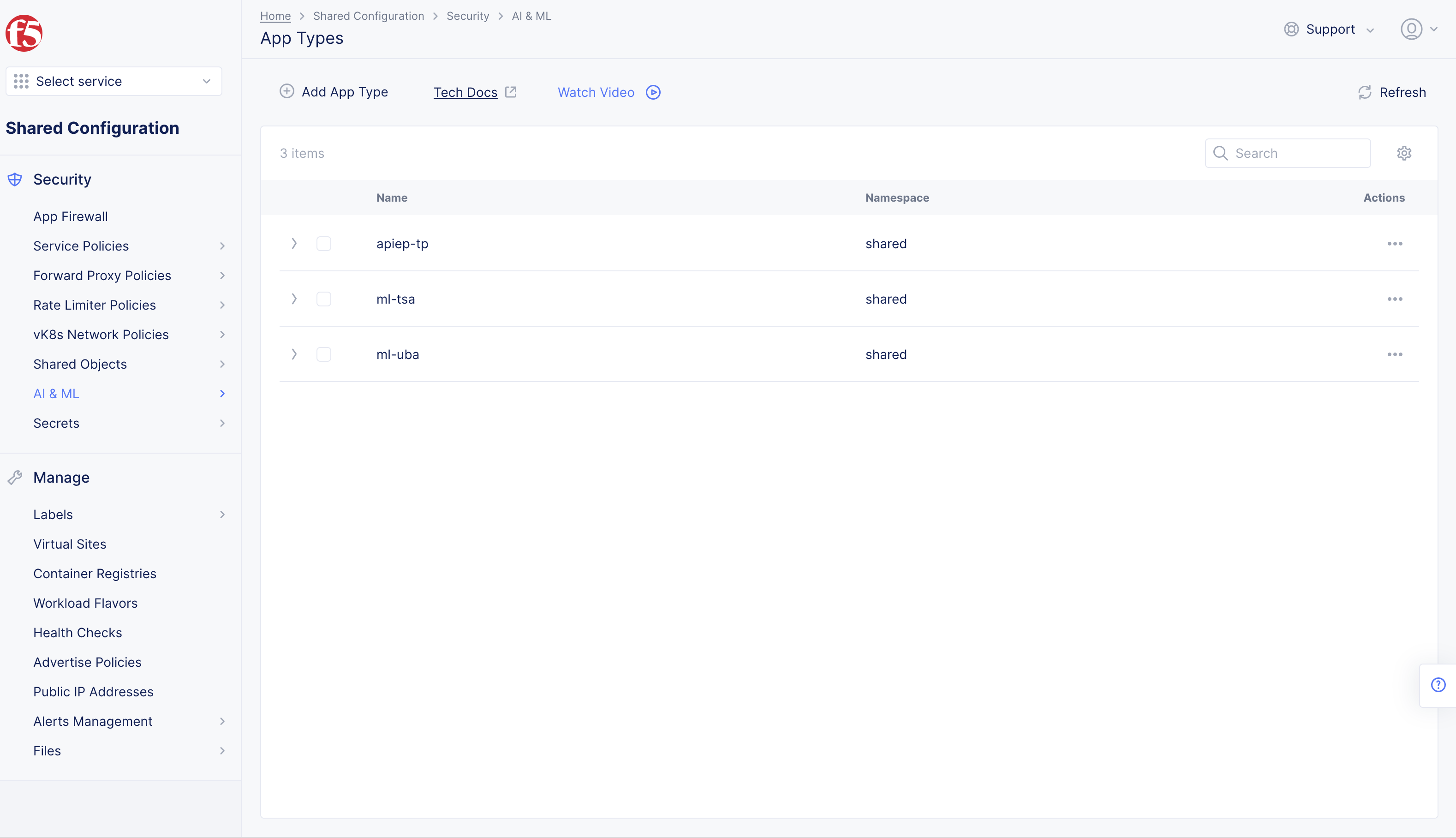
Figure: Navigate to App Type Configuration
Step 2: Configure app type object settings.
- Select
+ Add App Typeand enter the configuration in the app type object creation form using the following guidelines:
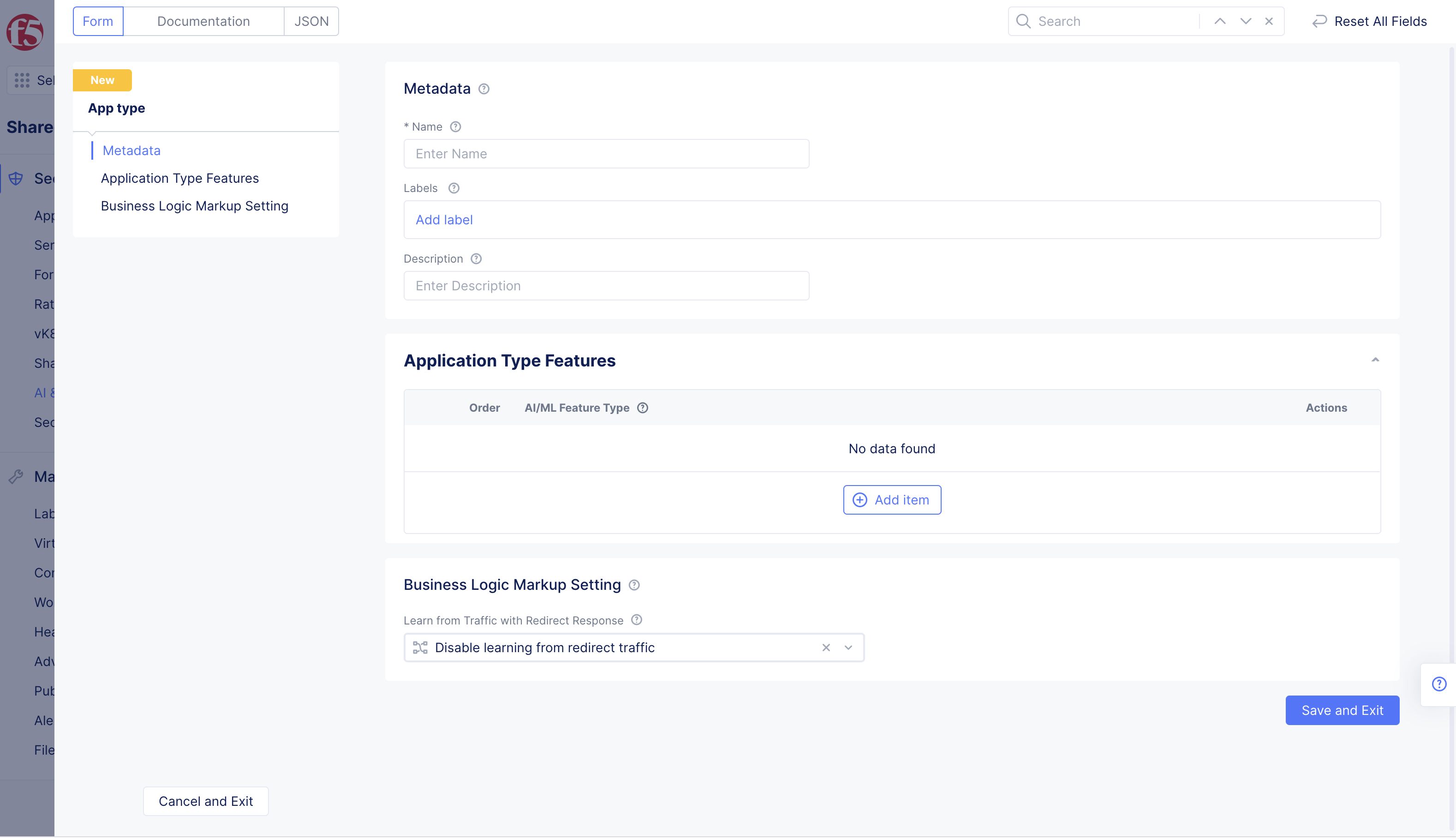
Figure: App Type Feature Configuration
-
Enter
Namefor the app type. This is the value for the app type label to be assigned to the load balancers for which the API discovery needs to be enabled. -
Select
+ Add itembutton inApplication Type Featuressection. -
Select
Malicious User Detection - Enable User Behavior Analysisfor theAI/ML Feature Typefield. -
Optionally, select
Enable learning from redirect trafficin theBusiness Logic Markup Settingsection. This enables the AI engine to learn the endpoints from redirected traffic. -
Select
Save and Exitbutton to complete creating the app type object.
Assign App Type Label to Load Balancers
After creating the app type, it is required to assign the app type label to the load balancers for which you want to enable UBA detection.
Note: Enabling UBA detection for all load balancers in a namespace requires you to apply the app type label to all load balancers in that namespace.
Perform the following to assign the app type label to your load balancers.
Step 1: Navigate to load balancer management.
- Select the
Multi-Cloud App Connectservice. - Select the desired namespace from the
Namespacedrop-down menu. - Navigate to
Manage>Load Balancers>HTTP Load Balancers. - Select
...>Manage Configurationfor the load balancer for which the app type label needs to be assigned. - Select
Edit Configurationin the upper right corner.
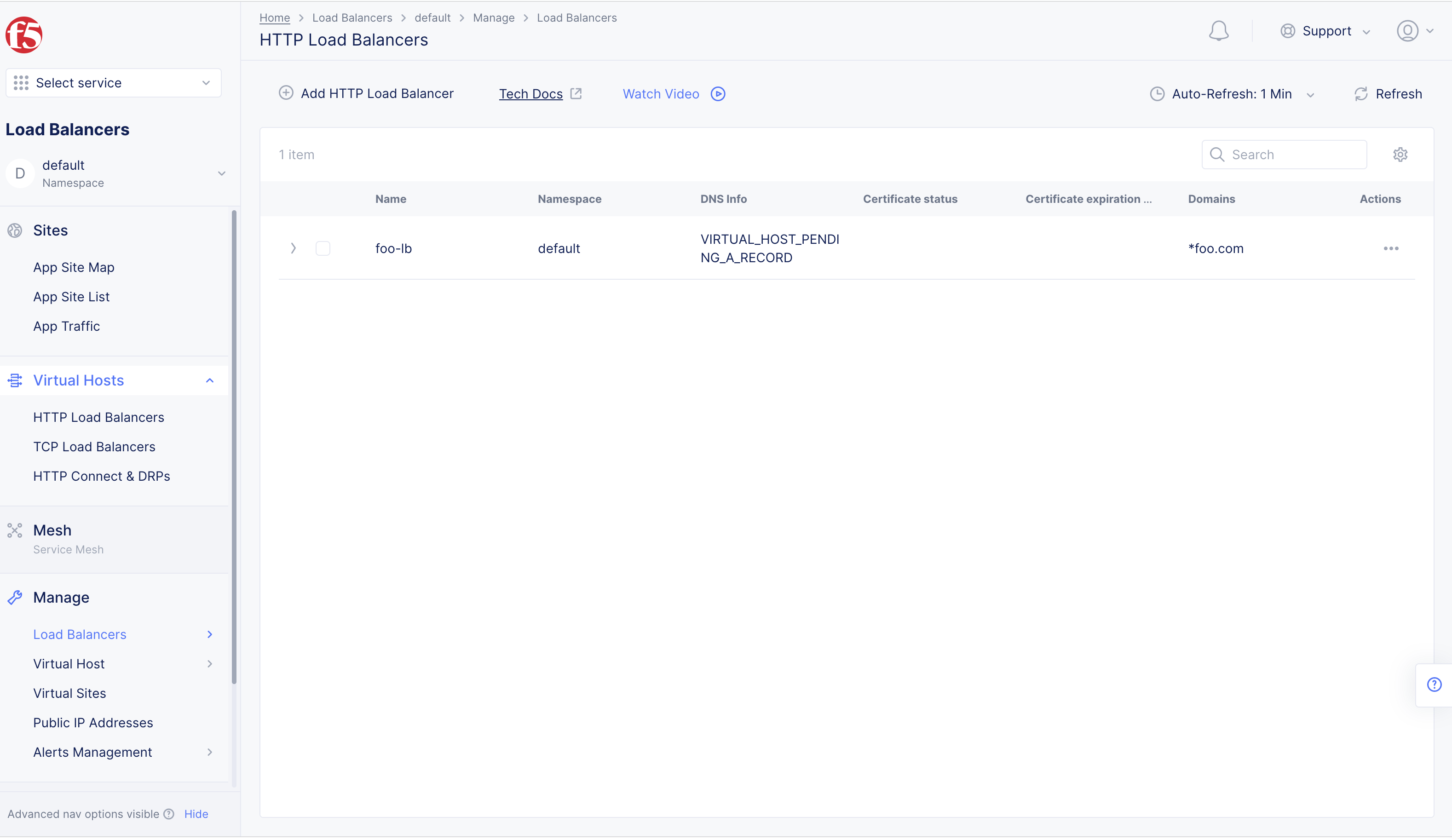
Figure: Navigate to load balancer Edit Configuration
Step 2: Assign the app type label.
- Select
Add labelinLabelsbox. - Select
ves.io/app_typefor theLabelsbox.
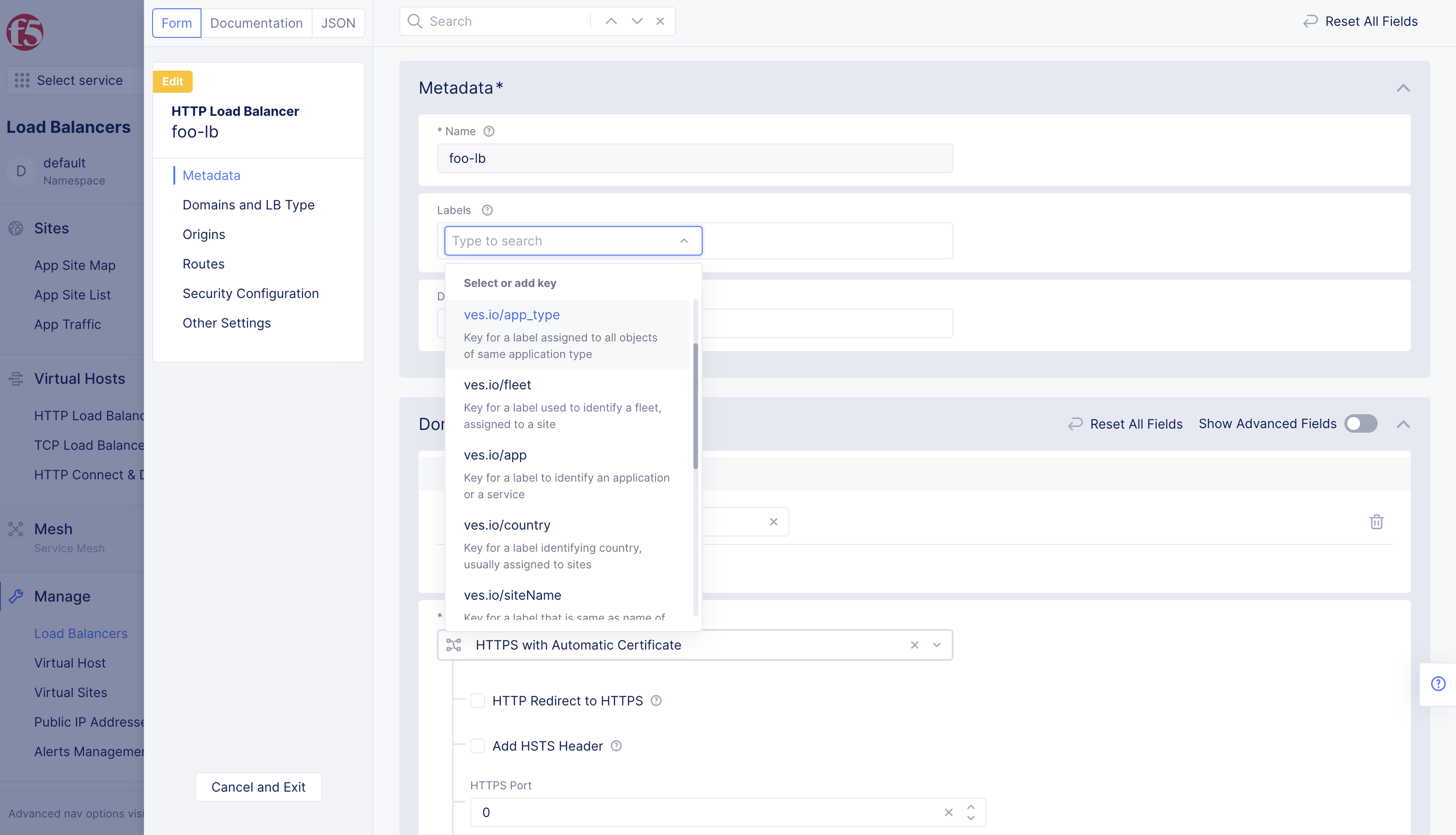
Figure: App Type Label Selection
- Type
Nameof the app type object created in the previous step, and selectAssign a Custom Valueto add the app type label.
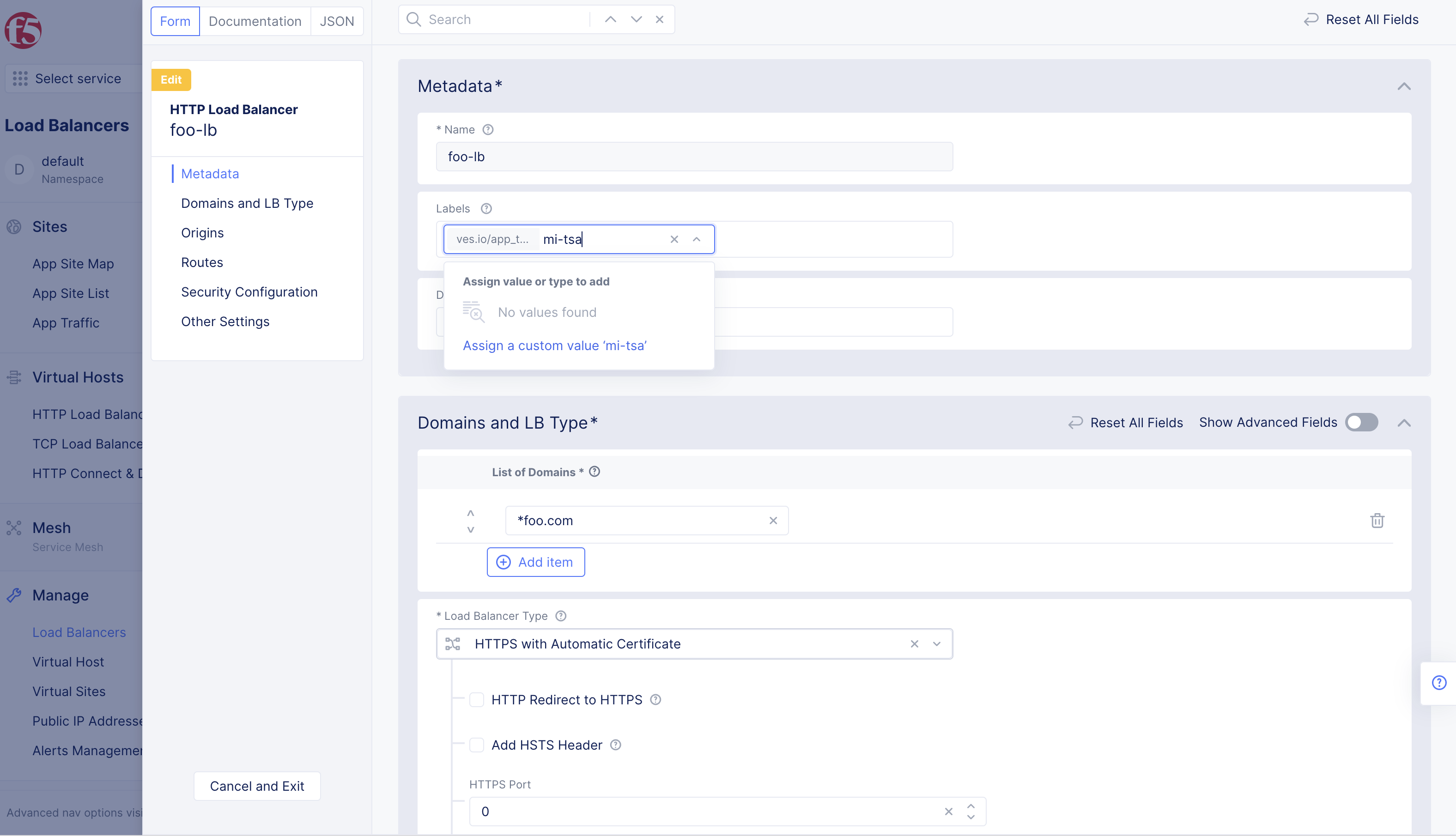
Figure: App Type Label Addition
- Select
Save and Exitbutton to apply the label to the load balancer.
Note: The Distributed Cloud Services AI model learns from all namespaces where the load balancers or vK8s services are applied with the app type label. You can turn off learning from specific namespaces using the app settings object.
Create App Settings
After creating an app type with the UBA feature enabled, it is required to associate it with the metrics and sources for which the user behavior analysis is required. This is done by configuring the app settings object.
Perform the following to create the app settings object:
Step 1: Navigate to the App Settings page.
- Select the
Multi-Cloud App Connectservice. - Select the desired namespace from the
Namespacedrop-down menu. - Navigate to
Security>AI & ML>App Settings. - Select
Add App settingfor the load balancer for which the app type label needs to be assigned.
Figure: Navigate to load balancer Edit Configuration
Step 2: Enter basic configuration for the app setting object.
- Enter a name for the app setting.
- Go to the
Application Type Feature Configurationsection, and selectAdd itemto configure an AppType.
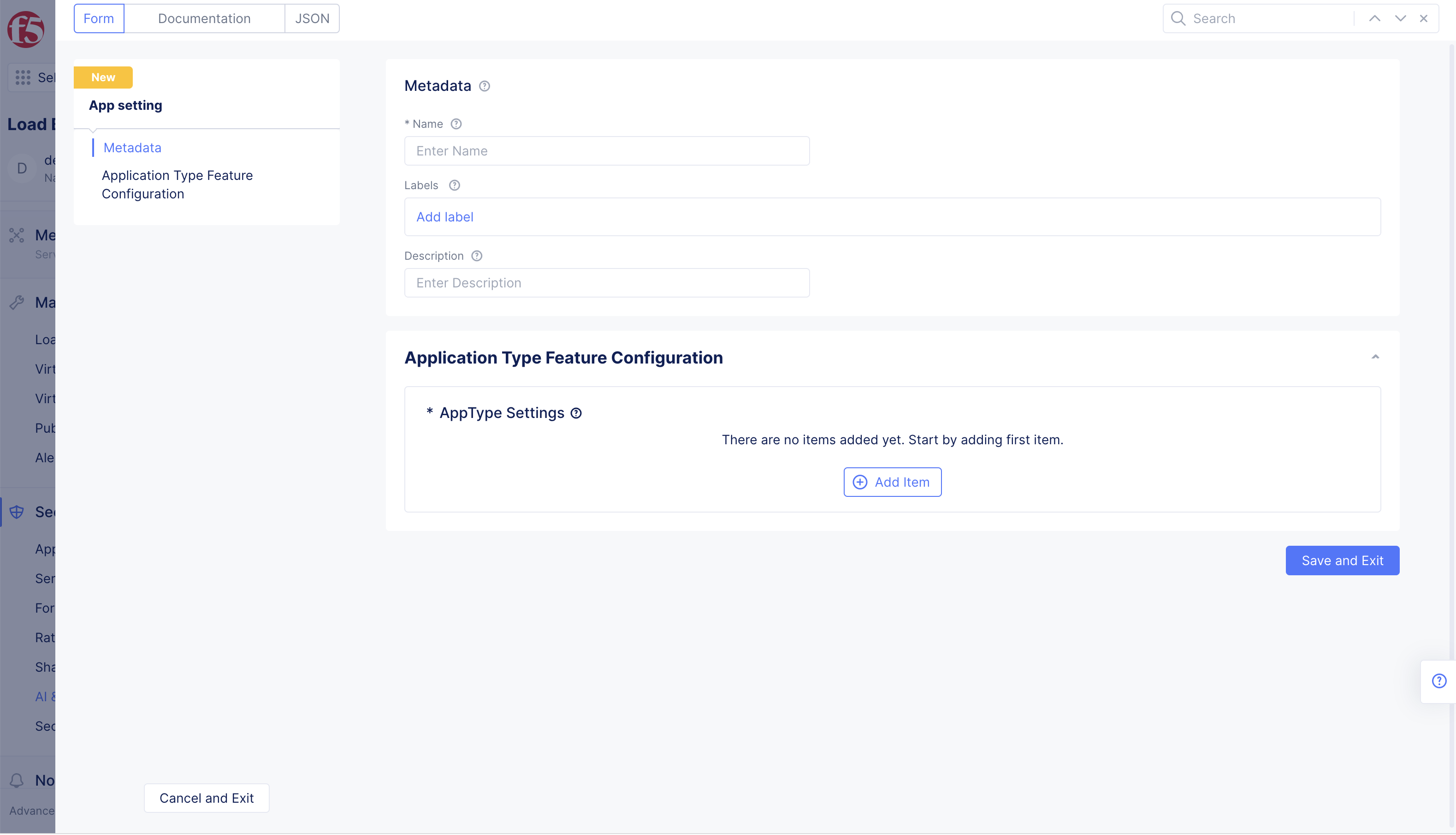
Figure: App Setting Basic Configuration
- In the
AppTypefield, select the created app type object from the drop-down list. - Select
+ Add Item.
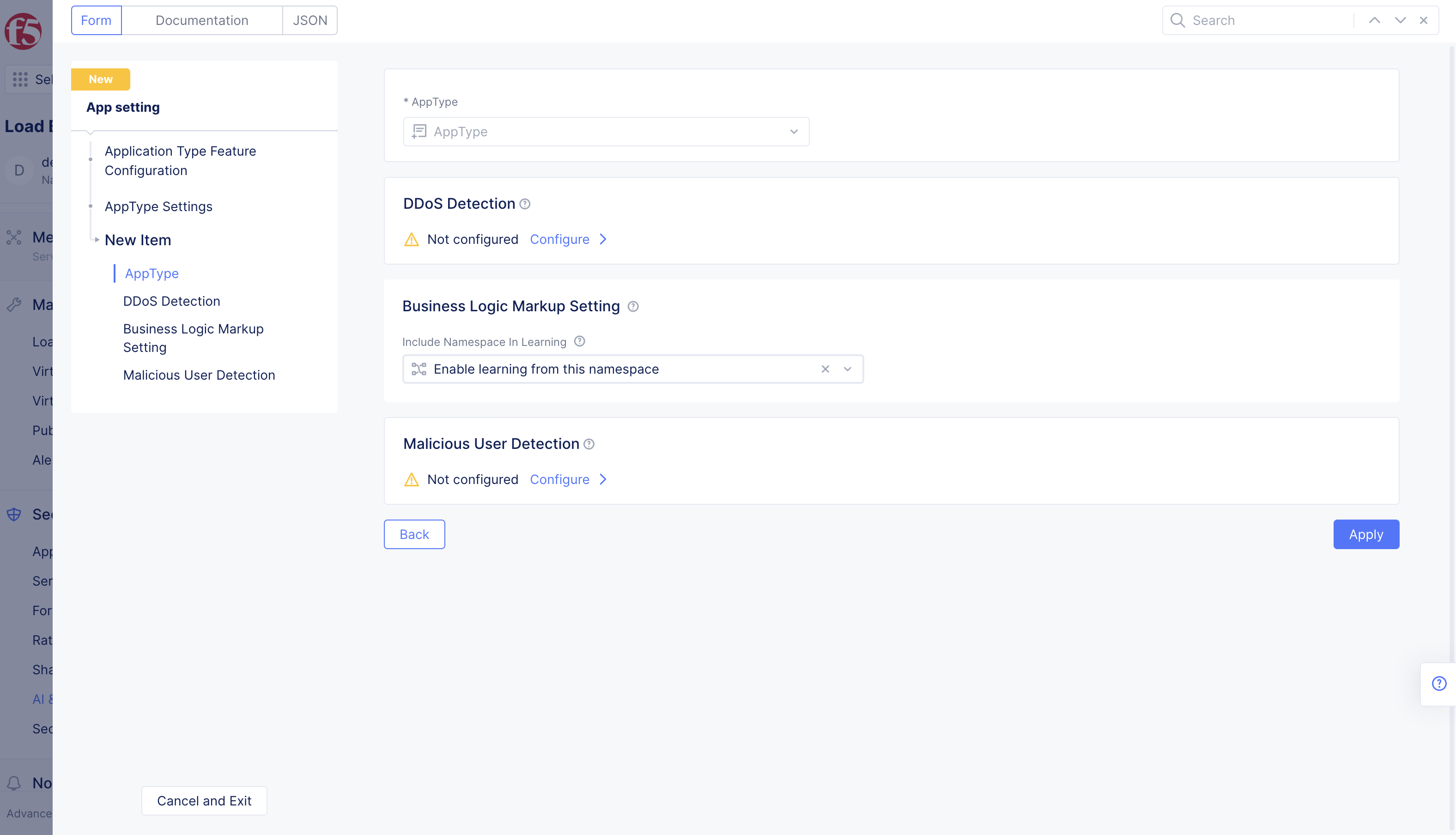
Figure: AppType Settings
Note: Optionally, select
Configurefor theMalicious User Detectionfield and selectDisable learning from this namespaceoption for the displayed fields. With this, the Distributed Cloud Services AI engine does not include data from this namespace for user behavior analysis.
Step 3: Complete creating app settings object.
Select Save and Exit button to complete creation of app settings object.
Monitor User Behavior
You can monitor the user behavior for anomalies and also inspect alerts using the HTTP load balancer monitoring.
Perform the following to monitor user behavior:
Step 1: Navigate to the load balancer monitoring.
- Select the
Multi-Cloud App Connectservice. - Select the desired namespace from the
Namespacedrop-down menu. - Select
Manage>Virtual Hosts>HTTP Load Balancers. - Hover over your load balancer from the displayed list, and select
Security Monitoringunder the load balancer name. Or select your load balancer from the displayed list to load itsPerformance Monitoringview, and then use the pulldown to change to theSecurity Monitoringview.
Step 2: Load Security Events view.
The Dashboard is loaded by default. Select the Malicious Users tab to inspect malicious user events. The graph shows a timeline over of malicious activity for the time period specified. Below the graph is a timeline of suspicious and malicious activity.
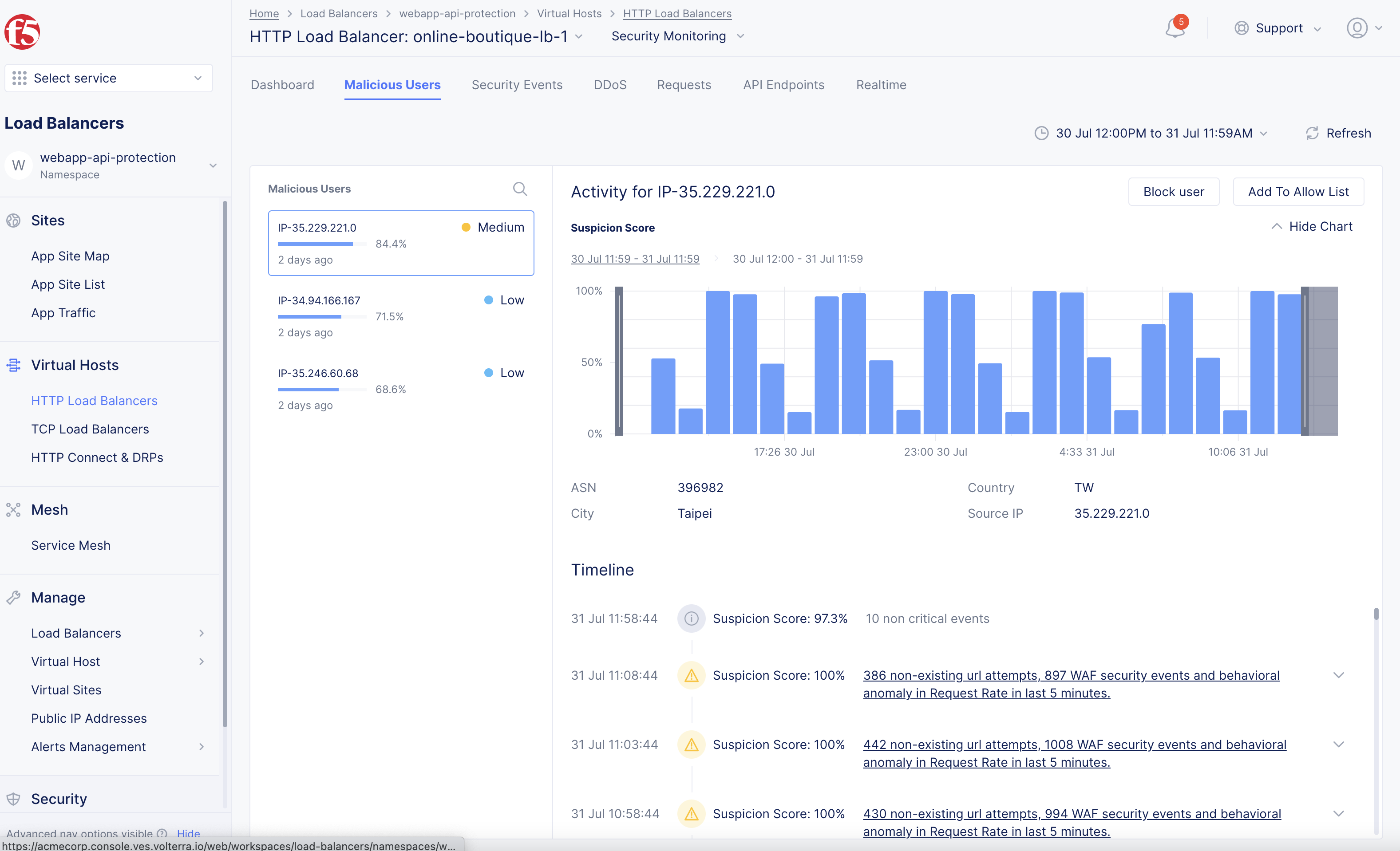
Figure: User Analysis View for Malicious Users
Select on one of the timeline links to see details for that time period, or select on the Security Events tab to dive into any time period.
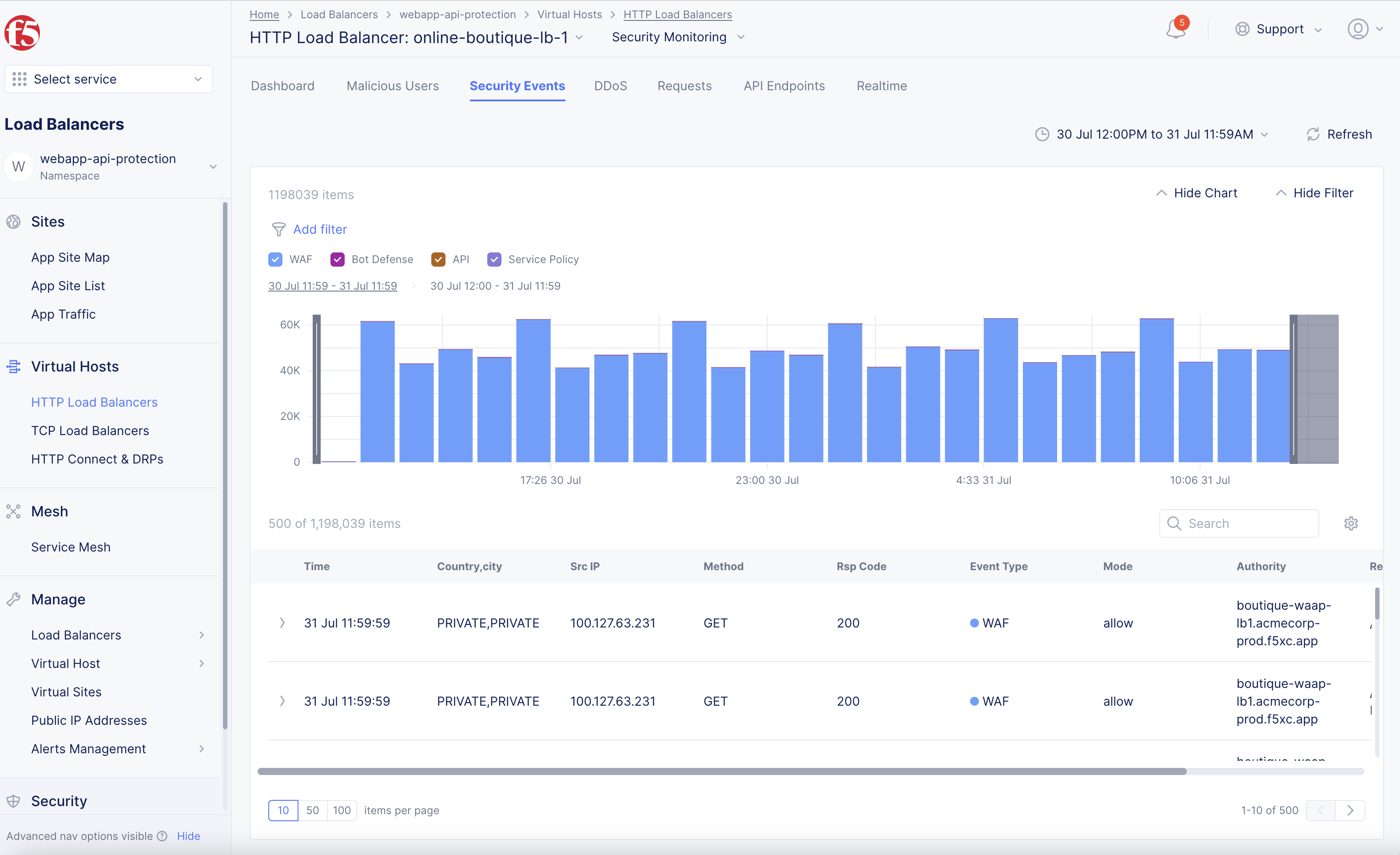
Figure: User Analysis View for Security Events